Cyber attacks are flourishing among all types and sizes of businesses across all industries. They are growing in volume, frequency, gravity, and sophistication. The volume of cybercrime has increased by 600% since the start of the pandemic because businesses needed to embrace remote work, something they were not prepared for.
Cybercrimes can be hacking, installing malware, or outright theft of sensitive data. They can also be DDoS attacks and installing viruses, malware, and botnets. Cyber attacks can also be web jacking, typosquatting, and — the most common of all — phishing scams.
Phishing attacks are the #1 cyber threat small businesses face in 2021
…And many small businesses may not even realize it.
Phishing attacks are the most widespread and most damaging threat to small businesses. They have grown 65% over the last year, accounting for 90% of all breaches that organizations faced. They have also grown in sophistication. Attackers have become more persuasive in pretending to be legitimate contacts.
Small businesses are popular targets for phishing attacks. Criminals know they’re not prepared against emerging network
security breaches. They have inferior defenses because they have less time and resources to put into cybersecurity.
Phishers are also leveraging the rapid increase in remote work as a result of the pandemic. While bigger businesses have more resources to attack, small businesses are no less lucrative. With automated attacks, criminals can target thousands of remote devices at a time.
Among the many phishing attack techniques, business email compromise (BEC) attacks account for a small volume in the number of attacks but a massive volume in cost. The 2021 Email Threat Report published by Area 1

What makes phishing attacks so damaging is that they are difficult to fight. Attackers don’t just exploit technological weaknesses. They use social engineering to execute their phishing scams.
What is phishing?
Phishing is a cybercrime that tries to deceive people using email, text,
The bad actors behind a phishing scam often disguise themselves as trustworthy sources. They target sensitive information, such as:
- bank accounts
- credit card numbers
- Social
Security numbers - birth dates
- addresses
- phone numbers
- email addresses
- other personal information
The goal of attackers is to steal your money or
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
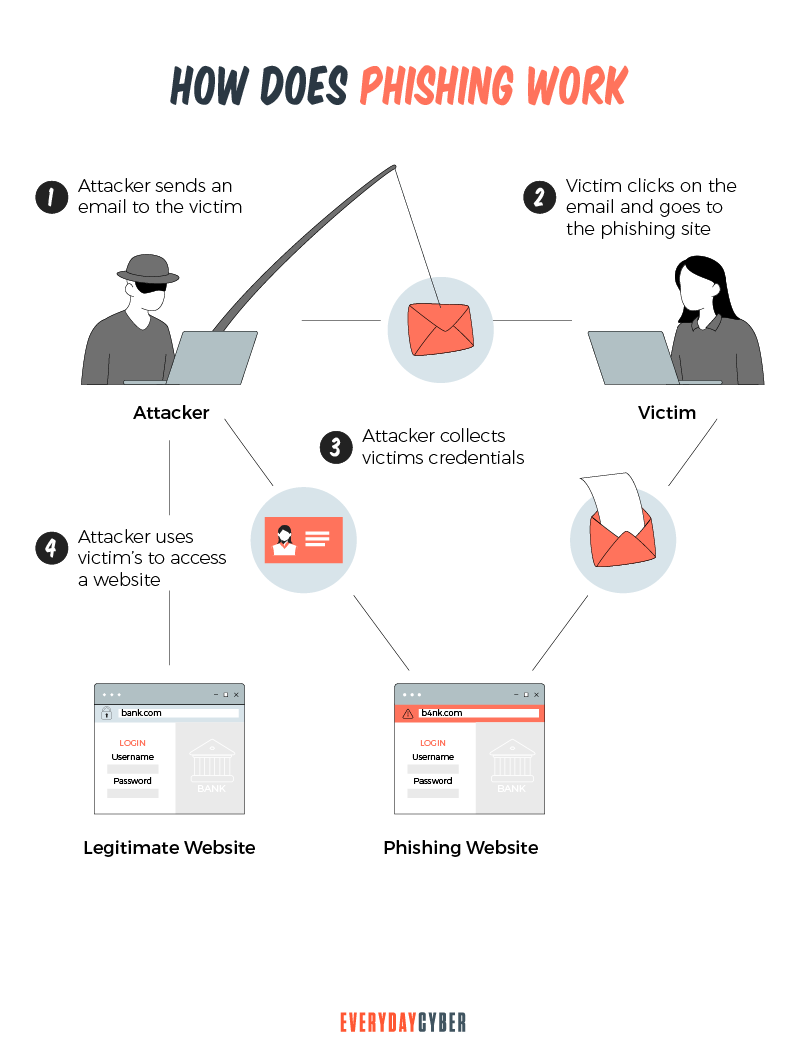
How does phishing work?
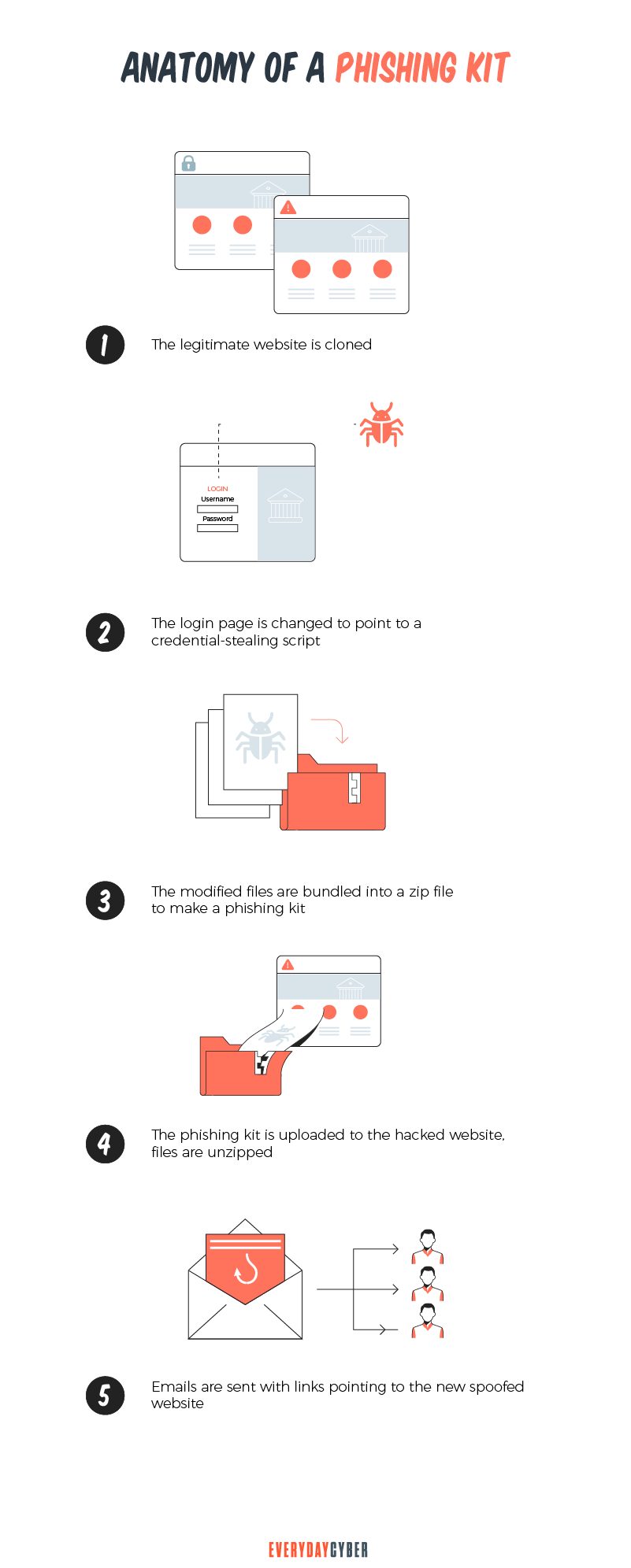
Attackers come well prepared for their phishing attempts. Before they even determine their target, which may be individuals or businesses, they have already created fake email accounts and fake websites.
The bad guys then send their phishing messages. They pose as trustworthy contacts. Sometimes, they even spoof relatives, friends, or colleagues of their targets. They trick users with sweet offers or instill fear to force them to click on a malicious link. The link leads them to a phishing website or download malware that poses a
Once the phishing attack is in motion, the attackers collect the data they need. They then use these data to commit other fraudulent activities or sell them on the dark web.
What are the types of phishing?
Phishing started in 1995. It was back in the days when America Online (AOL) was the leading Internet provider in America. Hackers and software pirates also flocked to the service to communicate. This group made up the “warez” community. They are responsible for making the first phishing attacks.
The group’s phishing attacks involved stealing users’ passwords. They also used to create randomized credit card numbers. AOL shut it down. But that didn’t prevent the hackers from devising what would become an enduring technique — sending messages through AOL’s instant messaging and email systems and posing as AOL employees.
Since then, phishing campaigns have evolved to target all sorts of businesses. The types of phishing attacks we are about to discuss are the most common ones, but the list is growing. There are definitely more that we probably don’t know of yet.
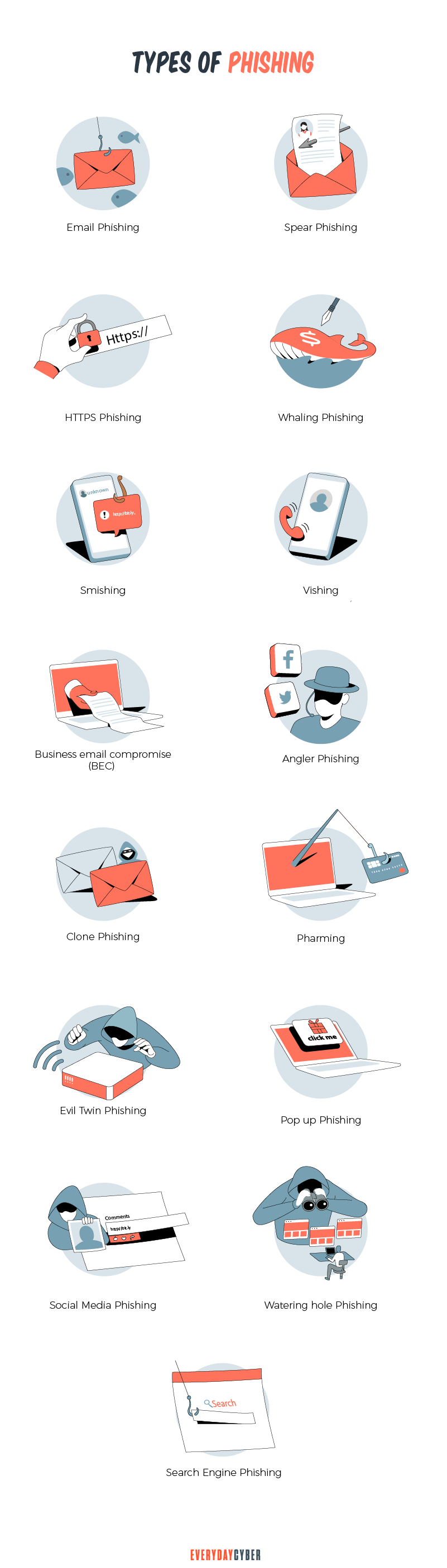
1. Email phishing
Email phishing is the most common method of phishing. Hackers pretend to be popular brands or legitimate organizations. They then send mass emails to as many addresses as they can.
Attackers try to trick users into taking action using social engineering. They urge them to, say, click a link or download an attachment. They manipulate people’s decisions by instilling a sense of fear or urgency. Or they offer irresistible deals.
The links are often malicious ones that lead to fake login pages that ask for the the users’ credentials. They don’t know that they’re handing over their personal information straight to hackers.
The links may also take them to malicious websites that install malware on their devices. The downloads are usually in PDF form. These contain malicious code that installs malware once the user opens the document.
How to spot phishing emails
The sender uses a public email domain. Organizations don’t use “@gmail.com” or @yahoo.com” for their company emails. They have their own email domain and company accounts. For example, legitimate emails from XYZ Company will use “@xyzcompany.com”.
The domain name’s spelling is wrong. There are many ways to create phishing domains that look like legitimate ones. For example, google.com may become:
- g00gle.com
- gogle.com
- goggle.com
- Googgle.com
The email contains grammatical mistakes, but not spelling mistakes. When constructing phishing emails, hackers often use spell checkers. Each word is spelled correctly, but many words and phrases are used in the wrong context. The message is full of grammatical errors, such as “an unauthorized user might trying to access”.
Some experts believe that the errors are part of a filtering system. Hackers can better target the most gullible victims using this filter. Only the most naive and unsuspecting will take the bait. And the hackers hope the targets believe the rest of the scam.
The email contains a limited amount of text but with malicious attachments or links to a malicious website. Phishing emails usually contain limited messages but will ask you to download an attachment or click a link. These attachments and links are where the malware infection originates.
For example, the phishing email you receive may ask you to check a credit card penalty in the attachment. When you download it, you find out that the penalty is not intended for you. But it’s too late, the downloaded malware has infected your computer.
The email asks for urgent action. Phishing messages have a manufactured sense of urgency or even fear. They make you feel like if you don’t take action now, it may be too late. This phishing email is often seen in the workplace. For example, an employee receives supposed instructions from the boss to process a vendor payment. Too timid to confront the boss, they may go on and complete the payment.
2. Spear phishing
Normal phishing attacks involve sending messages to random addresses. In spear phishing, the attackers send the emails to specific targets. These may be a particular individual, group, or organization.
Hackers first collect information about the targets to win their trust. Then they spoof email addresses that normally send to their
spear phishing targets.
They then send the messages when the targeted users are expecting the emails.
How to spot spear phishing attacks
Hackers use spoofed domain names and email addresses. They do this by changing a character, such as using “i for l”. They can also remove an inconspicuous character such as a dot (.) or comma (,).
A spear phishing email takes on an unusual format. If the email doesn’t look like any of the emails you used to receive from that sender, try calling them to check.
The email contains shared links. Hackers can trick victims into shared documents, such as Google Docs. These shared documents will then redirect them to a malicious website.
The email requires user login credentials. Be wary of instructions that request for user login ID and password. This is a
The message makes urgent requests.
3. HTTPS phishing
HTTPS, or Hypertext Transfer Protocol Secure, uses encryption to secure communications between a website and your browser. A website that uses HTTPS is safe. At least, most of the time. Cybercriminals use HTTPS in their phishing campaigns. They avail free TLS/SSL certificates or hack websites for their malicious purposes.
How to spot HTTPS phishing
Phishers use shortened links. Shortened links mask the original web addresses. These links hide or beautify long or ugly links and provide a simpler link that’s easier to remember.
Phishers also use hypertext. Hypertext is text that contains links to other texts. It is a simpler and clickable link that hides the complete URL.
4. Whaling
Whaling is also called CEO fraud. It works like spear-phishing, but instead of targeting company employees, whalers go after the big fish. They go for the whales — the senior executives.
The criminals impersonate these executives and send phishing messages to higher-level employees. The emails may request the recipient to review a document, process a money transfer, or ask for details about the company.
How to spot whaling
The email contains an unusual request. You can easily spot CEO fraud if this is the first time an executive makes a request.
The sender’s email domain name or address does not match the legit one. There may be some extra characters added or removed from the official one.
The message contains a false sense of urgency. it will ask you to do something right away, sometimes with threatening language.
5. Smishing
Smishing uses a text or SMS message to launch a phishing attack. The bad actors send text messages from what seem to be legitimate senders such as known brands. The messages contain malicious links disguised as an offer for a discount, coupon, or a chance to win a prize.
How to spot smishing
The sender might address you with a generic “Sir”, “Madam” or “Customer”. A text message from a real company you’re doing business with will address you by your full name.
The text message is being sent from an unfamiliar
6. Vishing
Vishing is short for voice phishing. Like phishing emails and texts, vishing uses a
For example, the attackers say you need an audit by the Internal Revenue Service (IRS). They then ask you for your Social
How to spot vishing
The caller uses an unfamiliar number. The
The caller coincides the timing of the call with seasonal events. Often, hackers time fake IRS calls during tax season. They create a sense of panic in the recipients, tricking them into giving away private information.
The requested action is unusual. Your bank knows your bank account profile. They will never ask for your account name and number or your online banking credentials. Similarly, the IRS has its own list of the Tax Identification Numbers (TIN) and SS numbers of tax filers. They don’t need to ask for these personal details because they already have them.
7. Business email compromise (BEC)
BEC campaigns are like whaling attacks. Malicious actors target high-level company executives, such as the CEO, CFO, or other financial officers. They spoof or keylog their email accounts. Then they launch fraudulent financial activities, such as money transfers to their own accounts.
BEC operations don’t normally include malicious links or attachments so they can evade traditional
security solutions. BEC attackers rely heavily on social engineering to manipulate employees and executives.
How to spot BEC
BEC fraudsters spoof the emails of their targeted senders. Fraudsters pose as executives of the company. The spoofed email may be one or two characters off so it can go through inboxes without much thought.
For example, hackers use the account of CEO Paul Smith of ABC as paulsmith@abc.com instead. But his authentic email is paulsmith@abcinvestments.com.
Email messages contain requests to send funds with urgency. The sense of urgency puts pressure on the recipient to do the request coming from a high-level executive.
Invoices don’t look familiar. BEC operators will spoof invoices to match company records almost exactly. Sometimes, the user doesn’t notice the differences because of the urgency of the email.
8. Angler phishing
Angler phishing uses notifications and DMs in social media to push you to take action. Angler phishers pretend to be customer service reps to trick you into handing over your personal details.
For example, when you complain about a brand on social media, angler phishers swoop in. They pretend to be customer service staff and appear to be eager to help. Then they provide a link to chat with an agent, but the link leads you to a malicious site where they ask you to spill your personal information.
How to spot angler phishing
The messages include notifications added to a post. These can contain links that lead you to malicious URLs.
The messages contain unusual DMs. Unusual DMs from senders you don’t know may be a sign of fraudulent intent. These may be fake users or bots. The messages they send often include links to fake websites even if they look legitimate.
9. Clone phishing
A clone phishing attack takes a legitimate email with links or attachments and clones it. The clone looks like the original but the links or attachments aren’t the same. These now contain malware and new links that drive you to malicious websites.
The email is also spoofed to look like it was resent by the original sender. They often use the alibi that there were issues with the links or attachments in the first email.
How to spot clone phishing
The email is unexpected. The email may come from a known sender, but the timing is suspect. For instance, why would a service provider send invoices when you don’t have a project with them?
The email requests for personal information. Legitimate service providers and business colleagues don’t normally ask for personal details. Not even your own bank will.
10. Pharming
Pharming is a form of phishing that exploits the technical workings of Domain Name System (DNS) servers. DNS servers are responsible for directing website requests to the correct IP addresses.
Pharmers hijack DNS servers that direct you to the IP address of a malicious or fake website. Your personal information becomes vulnerable to theft once you’re on the fake website.
Another way to pharm is to use malware distributed through suspicious messages and phishing emails. When victims open the poisoned files, the malware immediately changes the infected device’s local host files. Whenever users access legitimate websites, they land on fraudulent ones.
How to spot pharming
The URL begins with HTTP. HTTP URLs are not secure. Look for websites with web addresses that begin with HTTPS or a black padlock symbol.
The URL contains typos and other grammar inconsistencies. You can spot a pharming attempt in URLs that show strange fonts when compared with the legitimate website. They may also have typos and use minor spelling tricks that are almost unrecognizable. For example, “everydaycyber.net” could be written as “evrydaycyber.net”.
11. Evil twin phishing
Evil twin phishing uses a fake WiFi hotspot that intercepts data during transmission of your email messages. You can find public WiFi hotspots in coffee shops, airport lounges, or hotels. The evil twin hotspot looks legitimate but it actually directs a victim to a phishing site.
Malicious actors then engage in eavesdropping or man-in-the-middle attacks. These let them collect data that pass through the connection, like login credentials or other personal details
How to spot evil twin phishing
The fake hotspot triggers an “unsecure” warning on your device. People often ignore this warning for convenience, especially if they are in a hurry. They may also feel comfortable with it because it looks familiar and they may have used the service before.
The hotspot requires login. If you’ve been using a hotspot that didn’t ask you to log in before but wants you to log in now, be careful. Ask the network administrator. It may be the evil twin of the authentic hotspot.
12. Pop-up phishing
This type of phishing uses pop-up messages or notifications that you see online. Pop-up phishers infect legitimate websites with malware. They make pop-up boxes to appear on these websites.
A pop-up phishing campaign often starts with urgent warnings, such as fake
How to spot pop-up fishing
The website frequently displays pop-ups. If the website has an unusual number of pop-ups, chances are it may have malicious software. The pop-ups themselves also contain malicious code. When clicked or opened, they infect your device or lead you to fraudulent websites.
The pop-up messages often involve issues on your device. A legitimate service provider or IT group concerned about helping will never use pop-ups to communicate. They will send them directly to you through their official channels, such as an email or a
13. Social media phishing
Social media phishing attacks take place on social networking sites, such as Facebook, Twitter, LinkedIn, and Instagram. The goal is to steal data, gain control of user accounts, or spread malicious software. Social media channels are favorite targets for phishing because they are awash with information that hackers can use to launch attacks.
Social media phishers create fake accounts impersonating people the victims know to gain their trust. They may also masquerade as customer service accounts of popular brands. These dupe customers reaching out to the brands.
How to spot social media phishing
The offer is too good to be true. Social media scammers often offer an enticing incentive to lure their victims. They ask you to click fake social media posts where malicious actors can harvest your personal information. If the brand is launching a promotional campaign, check their website to make sure.
There are branding inconsistencies in the phisher’s account. Social media phishers will create fake URLs that are almost like the real ones. Watch out for spelling errors, logo design, color scheme, and other details unique to the original brand.
There is a high volume of the same status being shared. Scammers are persistent until they get what they want. If the same status is being shared with other people, this is a warning that the campaign is a scam.
14. Watering hole phishing
Watering hole phishing is a sophisticated attack that targets members of an organization, such as the employees of a company. Using techniques employed in social engineering attacks, cyber criminals research the websites employees visit while at work. The websites usually include third-party vendors, industry news, industry regulatory boards or industry organizations, conferences or forums.
Once they have discovered the employees’ favorite websites, malicious actors look for vulnerabilities in those websites that they can exploit. They then start infecting those websites with malicious codes that can capture sensitive information once the employees visit them again. With the information they collect, the attackers launch ransomware attacks on the organization.
How to detect watering hole phishing
Victims receive suspicious emails and notifications. Attackers will prompt users to visit the specific parts of the compromised website. These email phishing attacks do not come from the attackers themselves but from the compromised website’s automatic email notifications and newsletter that go out regularly.
15. Search engine phishing
In search engine phishing, attackers create their own websites that get indexed on legitimate search engines, such as Google or Bing. These websites showcase cheap products and attractive deals.
It’s one of the most clever types of phishing attacks. The websites trick users into to registering to view the details or buy something. The scammers can then steal credit card information and other personal data for malicious activities.
How to spot search engine phishing
The website offers incredible products and deals. Some of the common deceptions search engine phishing websites use are:
- Amazing discounts
- Free giveaways
- Free credit card
- Low interest rates
- Job offers
- Emergency warnings
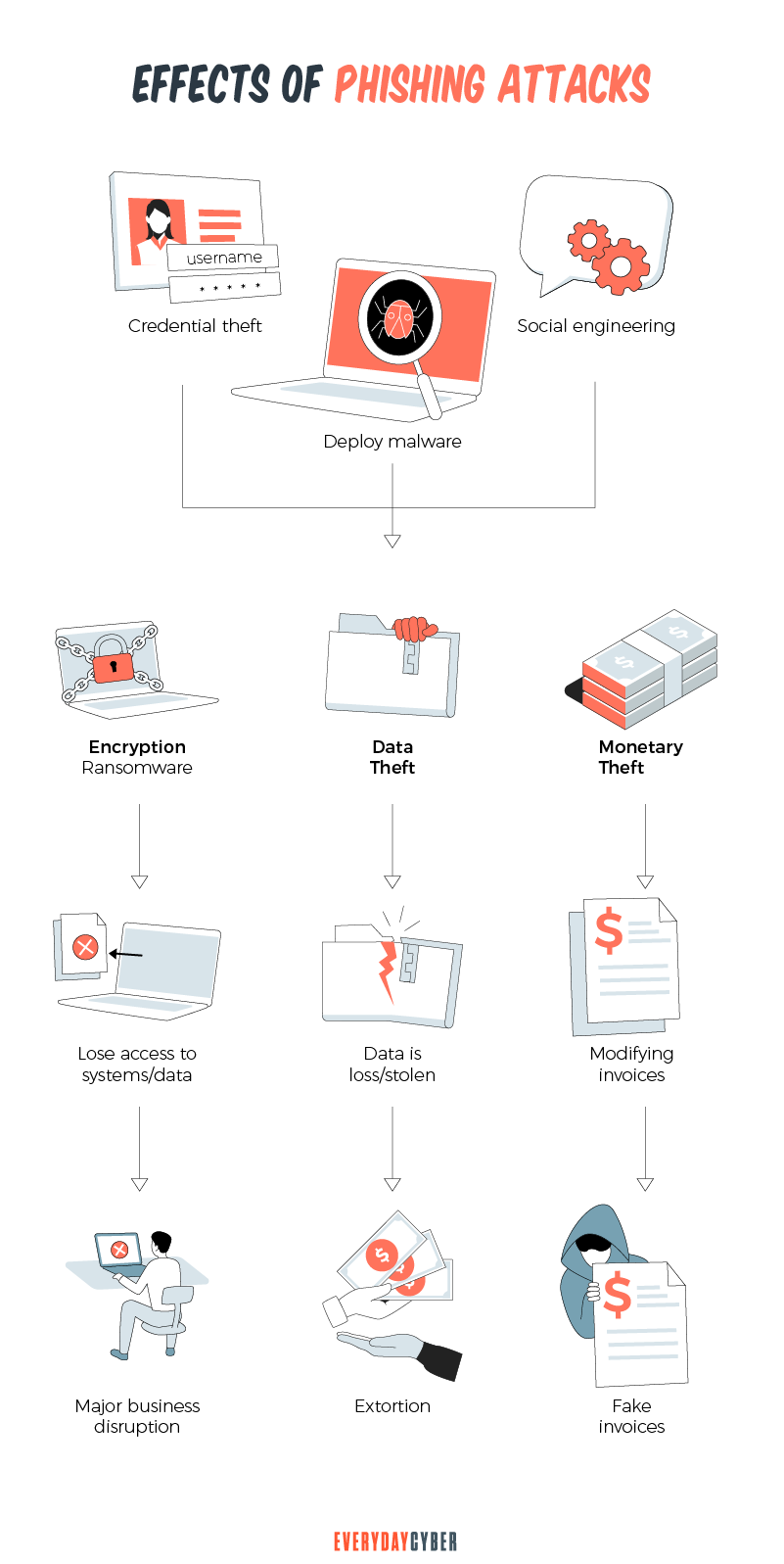
What are the effects of phishing on businesses?
Malicious actors behind phishing attacks aren’t just trying to steal money. They’re also stealing data, something much more valuable for businesses. The effects of data breaches on small businesses can be devastating. Here are some of them:
Damage to reputation
A company’s reputation takes a dive after news of a data breach. No matter how impressive a company’s PR department is, it will take years to rebuild back that reputation.
Loss of customers
The announcement of a data breach makes customers apprehensive. They may stop buying from the business for several months or never return to the business at all.
Decrease in investor confidence
Following a breach, company value decreases. Share prices fall as investor confidence decreases. The compromise experienced by Facebook in 2018 caused it to drop by $36 billion in value. The 2018 data breach of British Airways led to a more than 4% drop in its share price.
Business interruption
Phishing attacks can disrupt and paralyze businesses if data is stolen or damaged. Employees are unable to continue working. Customers are unable to access online services.
Most businesses victimized by phishing emails or other types of phishing attacks can restore operations in 24 hours. Business disruption from severe phishing attacks takes longer to recover.
Payment of data breach fines
Data breaches can cost companies hefty fines. Regulators are getting more serious on the protection of consumer data.
Equifax settled for a $575 million fine for its data breach in 2017. Uber had to pay $148 million in 2018 for not reporting its data breach that happened in 2016. Capital One Bank suffered a breach in 2019 and paid $80 million in fines.
How to mitigate phishing attacks
It’s often difficult to detect a phishing campaign, even for prudent users. These attacks are becoming more sophisticated and ever-expanding in method and speed. Scammers are always finding new ways to launch a targeted attack on unsuspecting users.
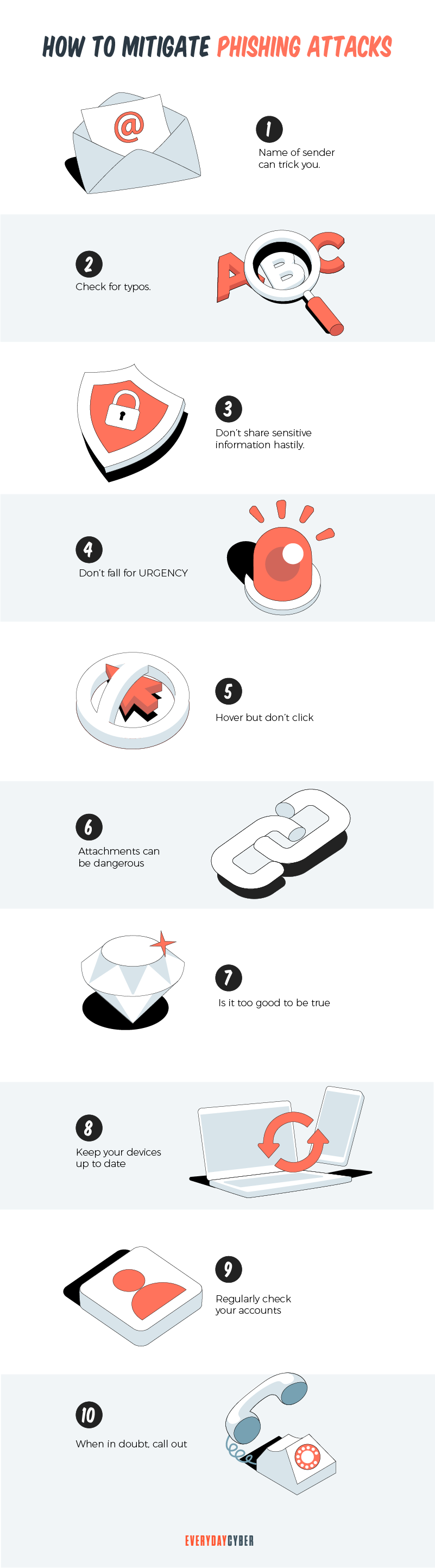
Here are some basic steps to mitigate phishing attacks:
1. Be vigilant before giving away sensitive information
When you get a notification from a government entity or your bank, verify if the website is authentic before clicking the link in the email. Type the address in the URL field of your browser to make sure it is real.
2. Be wary of warning messages
Getting warnings about your account or device having issues can be alarming. But this should not pressure you into handing over personal information. Reputable companies, such as your bank or insurance company, will not request account details. If you receive this type of information, call the company and delete the email immediately.
3. Do not click embedded links
If the email comes from an unknown source, the embedded link or URL is where the malware is. You can detect phishing by typing the correct URL into your browser to verify the sender. If the email comes from a vendor or contractor, review their contact policies for requesting information.
4. Avoid opening attachments
Email attachments can also contain malware. Attachments often come as a Word document, Excel, PowerPoint, or PDF.
5. Update your software, browser, and operating system
Personal devices running on Windows are popular targets of phishing attacks. Operating systems older than Windows 10 are especially vulnerable.
6. Reduce your spam
Random phishing content often arrive as spam emails. You can reduce your spam emails by separating your private email address from your public email address. Use your personal email client for personal correspondence and your public email to register on public forums, chat rooms, and other online services. Most importantly, never respond to any spam email.
7. Set up a security plan
To fully protect your business from phishing, have a
What do I do after falling victim to a phishing attack?
A phishing attack can happen to anyone, including you. If it does happen, here are steps to take immediately after it happens:
- Disconnect your device from the Internet.
- Back up your files to ensure your data doesn’t get erased in the recovery process.
- Change your username and password immediately after the attack happens.
- Use your anti virus software to run a scan on your system for potential malware or take your device to be fully scanned by a professional.
- Send out a fraud alert to any of the major credit bureaus, such as Equifax, TransUnion and Experian.
If you’re a victim of
Our final thoughts: Phishing remains to be the number one threat small businesses face. It is important to protect your business with increased awareness and due diligence. Be more watchful in your inbox and use a lot of common sense before clicking a link or downloading an attached file.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is Encryption?
Encryption is the process of scrambling data – text, audio, video into an unreadable form, known as ciphertext, so only authorized resources can decode/access it.
What is a Remote Access Trojan (RAT)?
A remote access Trojan is a software used by hackers to gain unauthorized access and remote control on a user’s computer or mobile device, including mouse and keyboard manipulation.
What is Phishing?
Phishing is a cyberattack that attempts to trick people using email, text messages, phone calls, or even fake websites into giving away sensitive and confidential information.
What is a Hacker?
A hacker is someone who challenges technology to see if it can be compromised. A hacker can black hat or white hat.
What is a zero-day threat?
A zero day threat is a security flaw known or unknown to the software vendor which hasn't had a patch made to fix the vulnerability.
A 10 Step Plan for Small Business Cyber Security
An effective cyber security plan outlines in simple language the best cybersecurity practices your organization needs to stay safe. It doesn't have to be complicated, but it should be pragmatic.