Cyberattacks have always been there, but the Covid-19 pandemic changed everything. We’re still trying to figure out how the shift to remote working changed the
However, one thing is certain: cybersecurity threats have likewise reached pandemic levels, particularly among small organizations.
What’s happening on the ground?
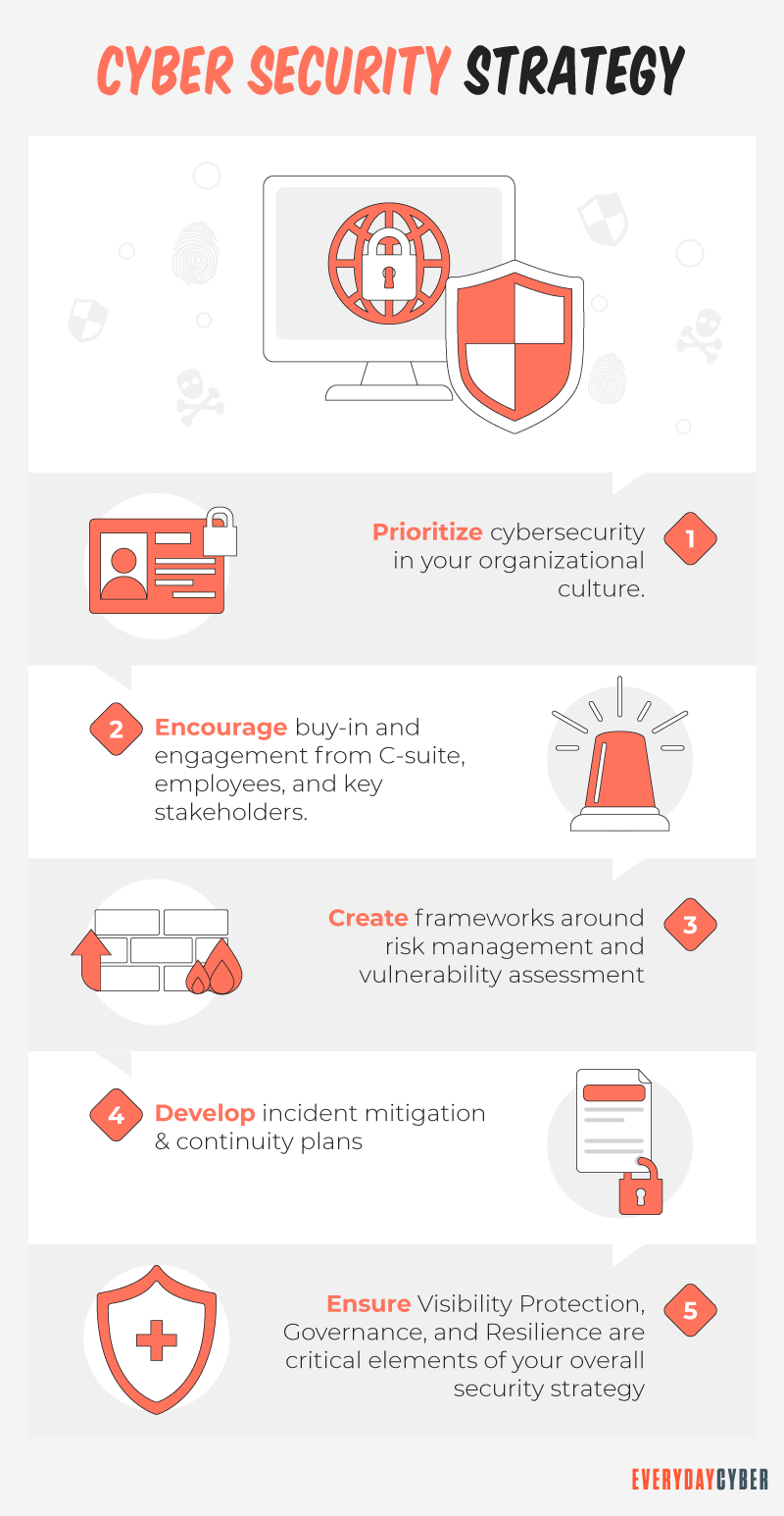
Small and midsize companies can’t afford to learn cybersecurity haphazardly while cyberattacks are steadily rising. If you’re a decision-maker, you can’t ignore the 424% increase in cyber breaches in 2021.
A look at other alarming cybersecurity realities in 2021, such as the following, should open your eyes to the level of exposure your business is in:
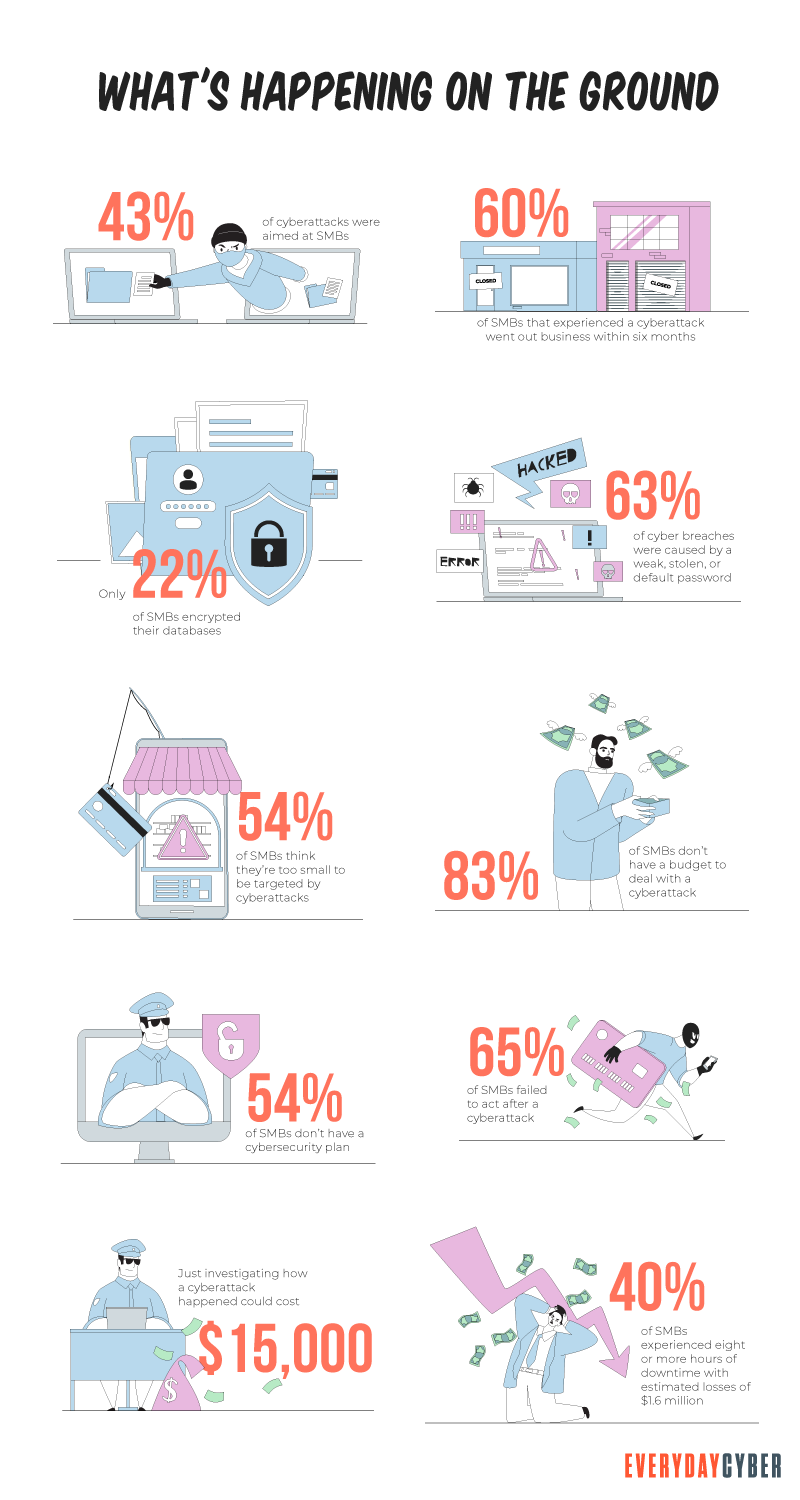
These figures aren’t just disturbing but devastating enough to put SMBs out of business. They are costly, both in terms of their reputation and revenue. They are also a compelling reason for small business owners to protect their companies by building a comprehensive cybersecurity strategy.
Your computers, devices, and software are the backbone of your business. You use them to communicate with vendors and clients, make important business decisions, and keep your trade secrets safe. As such, you can’t afford to commit any of these cybersecurity blunders:
Mistake No. 1: Underestimating Cybersecurity Threats
Computer viruses and worms are all too common; they may have lost their real meaning, or rather significant impact, on cybersecurity. They have even become more sophisticated allowing hackers to launch attacks undetected.
Computer viruses can do enormous damage. They can rapidly multiply on your system. They can change or delete critical data.
Worms propagate through your network, infecting every computer in your network almost instantaneously and modifying and deleting crucial information.

Spyware quietly monitors you and your employees. They send crucial information about your organization to cybercriminals for extortion or industrial espionage.
Keyloggers are devious tools that record your keystrokes and send them to hackers who use them for cyber fraud.
Ransomware is a particularly deadly virus that encrypts your important files, folders, computers, or entire network. Ransomware actors hold your information until you pay them a ransom.
SMBs think they’re unlikely targets of cyber attacks
Many small business owners have a negative mindset when it comes to cyberattacks. They often think that their business isn’t a big thing for cybercriminals. This false sense of
Most SMBs don’t have an IT administrator or dedicated IT
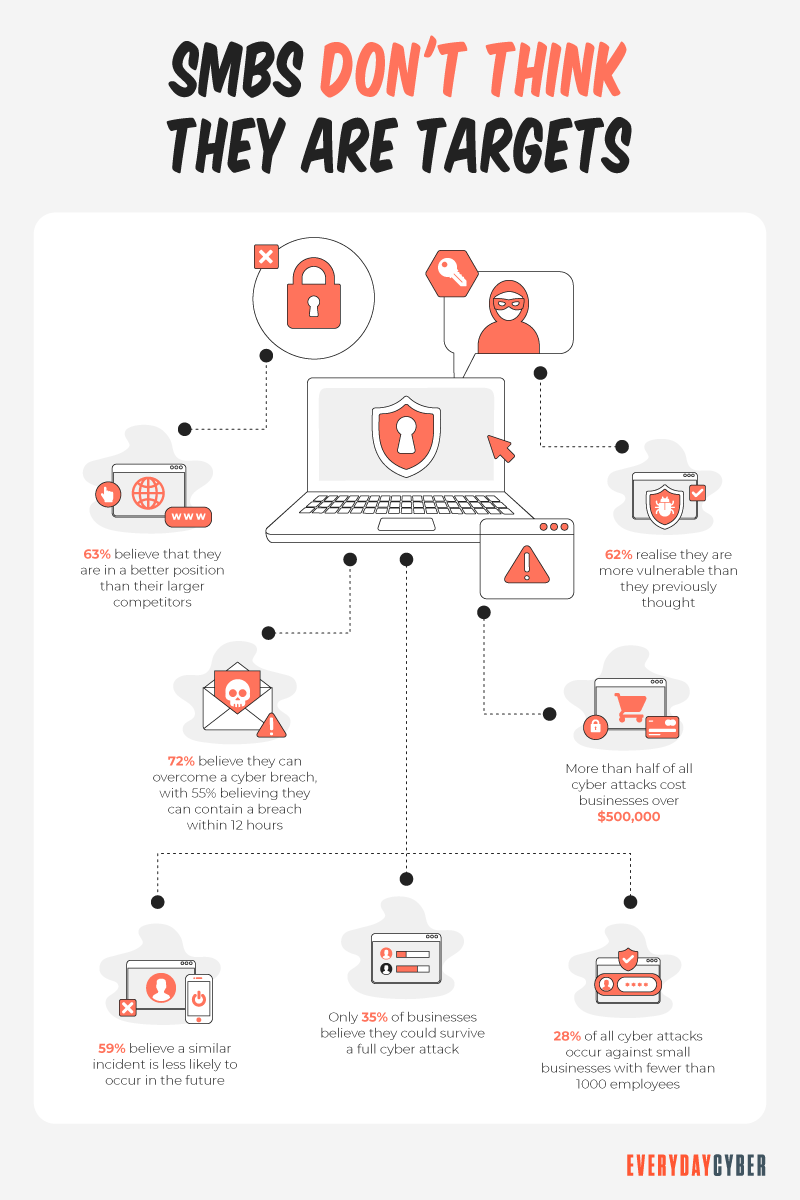
Another big reason why cyber criminals target SMBs is that there are more small businesses than big enterprises. They consider small businesses as low-lying fruits that are easier to pick than the large fruits that are well protected by an army of IT
SMBs have a vague understanding of supply chain threats
The supply chain comprises third party entities doing business with other companies. They are often small companies that act as vendors, suppliers, service providers, consultants, partners, and resellers who have built Trust relationships with each other.
A supply chain attack happens when a hacker compromises any of these third parties to eventually reach their target company. Many small companies don’t understand their role in the supply chain when it comes to cybersecurity.
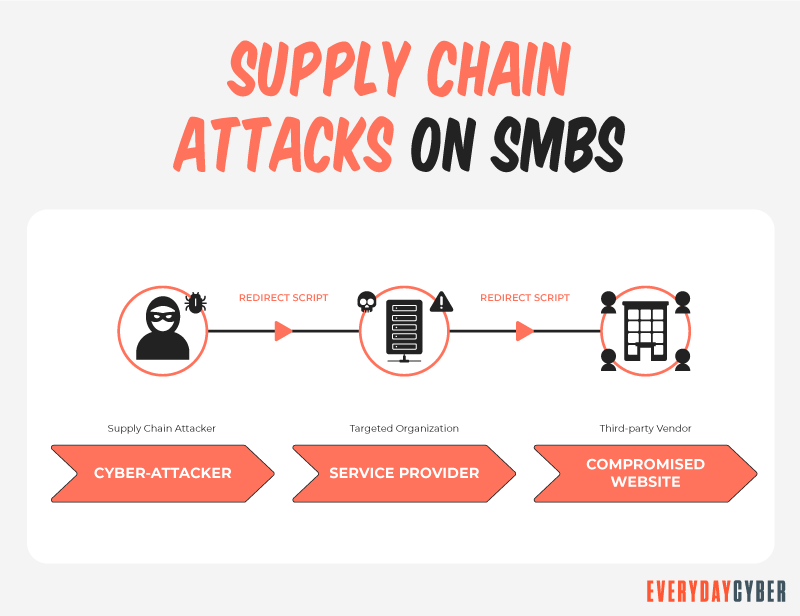
Supply chain attacks can be done with stolen certificates. Since the certificates are authentic, they vouch for the legitimacy or safety of products. Once hackers steal the certificate, they can insert malicious code undetected for a long time.
What many SMBs don’t realize is that without proper defenses, they are exposing themselves and the rest of the chain to cyber threats. Many supply chain attacks have been successful, such as the Target data breach in 2013, the SolarWinds incident in 2020, and the Mimecast attack in 2021.
Many SMBs ignore cloud challenges
SMBs are turning to the cloud for various reasons.
First, they’re using the cloud for rapid growth. SMBs believe the cloud empowers them to scale and grow faster. The rationale is that the cloud helps to simplify and streamline operations, thus unlocking new opportunities, new markets, and new revenue streams.
Second, SMBs are turning to the cloud to keep up with the changing business environment. They cite flexibility, mobility, and remote working as the key motivation for cloud adoption, rather than cost savings.
Employees may work from anywhere, thanks to cloud computing. They are not required to use specific equipment. They can use a cloud-based workflow and file-sharing tools to complete their jobs with their team members in real-time if they have an Internet connection.
But how safe is the cloud?
Moving to the cloud has its own risks. Even after shifting to the cloud, SMBs may still experience a data breach. When data is stored in the cloud, it can be more difficult to discover instances of unwanted access. By misusing an employee’s stolen account credentials, external attackers can get access to the cloud provider’s assets.
Erich Kron, security awareness advocate for KnowBe4, puts it succinctly. He says,
“You’re a smaller organization, and you’ve heard, the cloud is secure. What they don’t realize all the time is that, while the cloud provider takes care of their infrastructure in the back end, the data you put out there securing that is up to you. It’s not up to them.”
He continues,
“And applications are one thing. But especially when you’re storing data, or you’re doing your own app, in a cloud environment, you cannot rely on the cloud provider to be the
Is it safe to use free cloud-based services?
In order to keep costs down, many SMBs rely on free software and cloud-based applications. These free services, such as Gmail and Yahoo Mail, do not provide the level of
Some tips to avoid Mistake No. 1
To combat malware, you need robust anti-malware software from a trusted provider. You also need to have a deeper understanding of supply chain threats and cloud challenges so you can create a strategic cybersecurity plan to avoid them.
Mistake No. 2 – Lack of Cybersecurity Strategy
Information is the key driver of daily operations and top-level decision-making. Information loss as a result of
If you don’t take cybersecurity seriously, your business’s reputation will suffer irreparable damage. Fines and ransoms are both expensive. Breaches result in negative press coverage, heightened anxiety, and stress among employees.
Inadequacies in a cybersecurity strategy can include the following:
No cybersecurity risk assessment
Many SMBs don’t do a cybersecurity risk assessment because cash flow is tight, resources are scarce, and everyone is donning multiple hats to handle a variety of responsibilities.
With a mindset of being unlikely targets of cyber attacks, SMBs naturally don’t care much about assessing potential cyber threats. Many of them claim that: [8]
- They don’t have information that criminals will want to get
- They have
security protocols in place that prevent breaches - They think their business could survive a breach
- They manage their own IT
security needs
While the cost of breaches isn’t much of an impact on big enterprises, it could be devastating to small companies. Remember, the average cost of investigating a cyber breach alone is $15,000. Add to that ransom payment, fines, and loss of revenue and you have a business that’s plunging to its end.
No security asset inventory appraisal
Asset protection is network protection. Many small firms ignore hardware and technology protection. This includes all devices, applications, and systems.
It will be difficult to track, secure, patch, or back up assets if you don’t know what assets you have or use. Ransomware and other malware incursions can be particularly destructive to your business if you don’t back them up on a regular basis.
Some tips to avoid Mistake No. 2
Oftentimes, SMBs have an incomplete picture of their assets. This leaves their vulnerability assessment wanting the needed protection for crucial assets. This also creates
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Mistake No. 3 – Weak Cybersecurity Tactical and Operational Practices
SMBs aren’t always as concerned about cybersecurity as they should be. Again, they believe they aren’t vulnerable to cyber threats. This leads them to implement weak cybersecurity practices, cut corners, or apply bandage solutions to unexpected cyber incidents.
Here are common cybersecurity tactical and operations practices that every small business should avoid:
Implementing bad password practices
Weak passwords like “123456,” “password,” and “qwerty” continue to top the lists of weak passwords year after year. Using a brute-force password-cracking program, a cybercriminal could crack a password in less than a second.
It’s also risky to reuse passwords for multiple accounts. Cybercriminals know that people repeat passwords. They can use credential stuffing and other sorts of attacks to look for compromised credentials on several accounts.
Relying on default passwords is a common practice among SMBs. Despite the fact that providers normally advise clients to change the default password before using new software or hardware in their businesses, many SMBs fail to do so. The default passwords used by vendors are easy to locate on the Internet, making it easy for cybercriminals to get into such service accounts.
Sharing passwords is another bad practice that many employees are guilty of. It can make accountability difficult to pinpoint because it’s never evident who was genuinely responsible for system activity.
Not using encryption
Every company relies on digital information, which is vulnerable to breaches if it isn’t encrypted. Encryption is an important line of defense since it ensures that even if hackers gain access to your networks, they won’t be able to use your information.
Think about what may happen to your unencrypted information in intercepted emails, lost or misplaced devices, or malicious activities of users. Criminals can sell it to the dark web or use it themselves to launch scams, ransom offensives, and other money-making fraudulent activities.
Reliance on default security technology
Default
Because of the frequent discovery of security flaws in certain operating systems, the poor performance of a default
Dependence on legacy software
Paying less for safety may appeal to a small business owner that lacks the infrastructure or cash to invest heavily in their own IT. However, it comes with its own set of risks. Rundown legacy computer programs are easier to hack.
In the long term, the cost of greater protection may be less expensive than the cost of repairing a cyber catastrophe caused by old programs.
Using free cloud services
Cloud service providers are expected to use the most up-to-date standards and certifications. However, storing sensitive information using free cloud services often poses a cybersecurity risk. Any data-related arrangements must consider safety and privacy, especially when dealing with sensitive information.
As the owner of a small business, you are responsible for managing employee usage, and it is up to you to carefully consider all possible defense scenarios.
Another drawback of cloud storage is that support isn’t great. Many providers will direct you to a knowledge base or a list of frequently asked questions.
Using free antivirus software
It’s not a bad idea to rely on pre-installed
Other safety measures must be used to supplement it. Layers of defenses are used in good cybersecurity. If one layer fails, the others can step in to fill the void. Multi-factor authentication, firewalls, network monitoring, private WiFi, and active monitoring solutions are some of the other layers to deploy.
Lack of multi-factor authentication
There are three components to multi-factor authentication:
- Something you’re familiar with – a password
- Something you have – a
security ID badge, a hardware token, or an authenticator app - Something you are – biometrics
Cyber thieves need at least two of these factors to gain entry to individual accounts or networks. Not only would they need a password, but they would also need to steal to a
MFA can also be hacked by sophisticated cybercriminals using phishing emails, SIM swaps, man-in-the-middle assaults, or even rebuilding the password generator.
All in all, MFA does not completely eliminate all potential dangers, but it certainly mitigates it. And it’s a step better than having none.
Not updating consistently
Failing to update your systems and software consistently exposes your network to certain risks.
Updates serve a variety of purposes, but the most important is to patch vulnerabilities. The longer you have an obsolete or unpatched operating technology, the greater the chance of a network hack.
Cyber syndicates are always trying to find
Viewing a rogue website, clicking on a corrupted email, or playing infected media can all lead to all kinds of exploits on your organization. Malware can steal your information or give an attacker access to your systems. You end up being at their mercy once they gain control.
Failure to backup
Information is essential to a company’s success. Its loss can have serious effects, such as shutting down operations and losing a lot of money. This is why failing to backup your whole network is a major blunder made by SMBs.
If you just have one copy of your information, you risk losing parts or all of it, forcing you to find cheap solutions that are unlikely to sustain your business over time.
Lax security patching
Many SMBs have a backlog of patching to do. Small business owners argue that their staff is overworked or that they are unable to afford to hire IT personnel to deploy patches on time. One of the most potentially devastating small business cybersecurity blunders is a lack of patch management. With new threats emerging every day, unpatched vulnerabilities expose organizations to malware infection.
Using public WiFi
SMBs provide remote work as a benefit to their employees as well as a cost-cutting option for their organization. Employees will most likely connect to their company email, business software, and file servers via public WiFi.
It’s not safe to use public WiFi. To intercept private information, such as passwords, an attacker could use packet sniffing or a man-in-the-middle attack. They might also set up a false hotspot in the area with the same name and login credentials as the legitimate public WiFi.
Not monitoring privileged accounts
Users with privileged administrative roles in an organization is in control. Whether the environment is on-premises, in the cloud, or in a mixed setup, the accounts used for access must be protected.
The integrity of the privileged accounts that govern your IT systems is critical to the protection of your corporate assets. Credential theft attempts are used by cybercriminals to target privileged accounts and obtain access to critical information.
Some tips to avoid Mistake N0. 3
Cyber attacks are out there waiting for opportunities to strike. Avoid these weak cybersecurity practices to protect your network from them.
Mistake No. 4 – Inadequate Cybersecurity Training Program
Not having an effective cybersecurity training program puts organizations at risk of cyber exploits and other threats. Sadly, many small firms don’t have continuing cybersecurity training for their employees.
Even the strongest
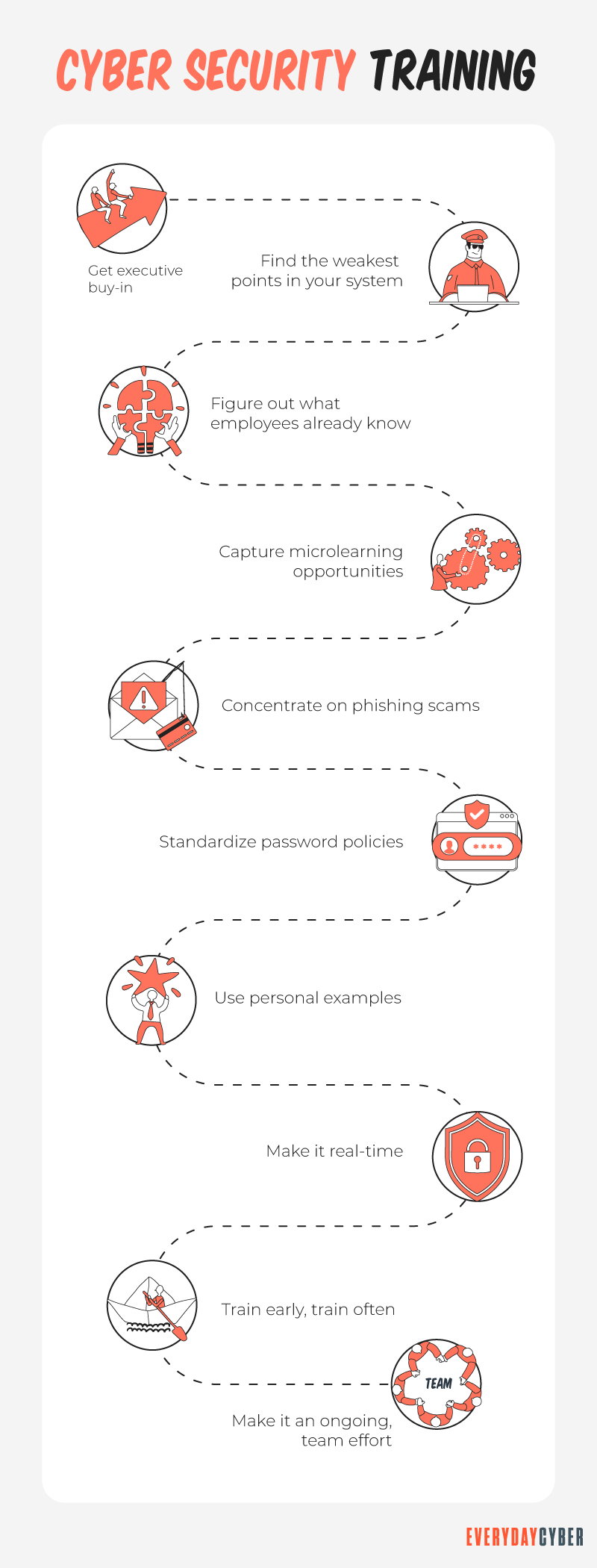
Your employees will be more suited to defend your network if they are taught and are knowledgeable about cybersecurity dangers.
Some tips to avoid Mistake N0. 4
Invest in your staff, educate them on threats and make it clear what you expect of them in terms of what they should and shouldn’t do.
Mistake N0. 5 – Lack of a recovery plan
What’s the worst that can happen if you don’t have a recovery plan? Any or all of these can occur:
Complete loss of data. The cost of a total data loss can range from thousands to millions of dollars, depending on the size and operations of a company. Data loss sets off a chain reaction from which many firms are unable to recover.
Business disruption. You are losing money every minute you are not working. Your company is also losing employee productivity. Downtime costs money. If you lose data, your company will be without the information it needs to get back to business as usual.
Loss of customers. Your customers are unlikely to be concerned about a breach. They’re more interested to know when you’ll be back up and running and where their information has gone.
Consumers have requirements, and they have chosen you to meet their needs. They will begin to doubt your ability to preserve their sensitive information if they perceive that you don’t have a recovery strategy in place.
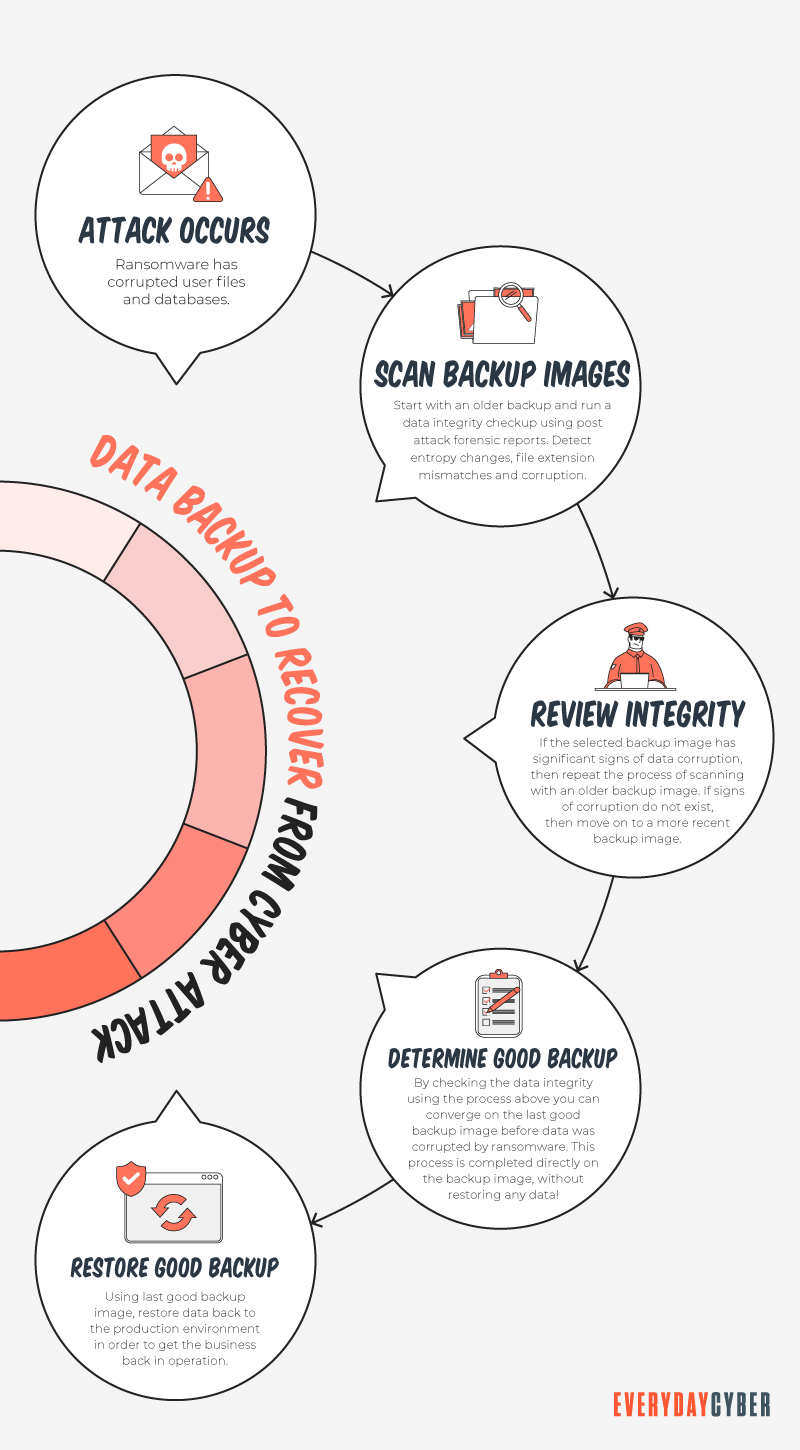
When word comes out that all of your data has been lost, it will spread like wildfire.
Costly recovery. Many factors influence the expenses of a data loss, including the costs of investigating the breach, replacing hardware, and rekeying data, as well as the loss of daily earnings and staff productivity.
Our tips to avoid Mistake No. 5
To ensure business continuity and compliance to regulations, SMBs should give priority to a resilient recovery plan.
Our final thoughts: Small and medium-sized businesses are increasingly under attack from cybercriminals. Many of them lack a clear understanding of the complex nature of cybersecurity and so commit mistakes that can be catastrophic.
What is important is to learn from these mistakes to help you avoid doing the same mistakes again and help you improve your
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is Social Engineering?
Social Engineering in the digital world is the intentional deception and manipulation of victims to cause the release and sharing of confidential information used to commit fraud and other cybercrimes.
Lock the Door. Bad Passwords: The Greatest Threats to Password Security
Bad passwords are the entry way for hackers to get into your accounts. Learn how to protect your cyber assets by using better passwords now.
What is a zero-day threat?
A zero day threat is a security flaw known or unknown to the software vendor which hasn't had a patch made to fix the vulnerability.
What is Spear Phishing and How to Protect Yourself from It?
Spear phishing activities are becoming more sophisticated and rampant. The best defense against it is to maintain a vigilant mindset.
Strong Passwords. One giant step to protect our digital lives
Here's how to create long, complex, and unique passwords to protect your accounts and keep your sensitive info safe from hackers.
What is a Potentially Unwanted Program (PUP)?
PUPs refer to programs, applications and other software downloaded onto computers or mobile devices that may have an adverse impact on user privacy or security. The term “potentially unwanted program” was coined by McAfee to distinguish the program from malware.