Vishing is a thriving cybercrime that’s threatening not just Americans but people all over the world. Attackers scam their targets through
Isn’t it scary that 46% of Americans are bombarded with spam calls everyday? Spam robocalls are growing because they are incredibly profitable.
Their objective is to steal your information in order to use a your credit card, deplete your bank account, engage in blackmail, and a whole host of other activities.
A personal experience
One day last year, I received a call from an unknown
Being a writer on technology, and more recently cyber
I was lucky to have some knowledge of this type of scam. But what about ordinary citizens who can be easily intimidated because they simply are unaware of the threats. Cybercrime is huge business. Vishing and its cousins, phishing and smishing, have proven to be very successful methods for extracting critical information and then stealing or scamming from their victims.
So What is Vishing?

Vishing, also known as voice phishing, is a type of phishing that uses
Vishing, like phishing, depends on tricking their targets into thinking that it’s for their own good to respond to the call. A caller usually impersonates a representative of the government, the tax authority, the police, or even the victim’s bank.
Cybercriminals use persuasive language and social engineering techniques like threats or urgency. Their intention is to convince victims that they have no choice but to give the requested information.
Most vishers speak convincingly to appear as though they are assisting the victim to avoid penalties or even criminal charges. Another typical strategy is to threaten the recipient by leaving voicemails that demand an immediate call-back or risk having their bank accounts closed, getting arrested, or worse.
Vishing is More Than Just Phone Calls
Vishing attacks involve more than just dialing numbers. Cybercriminals use a scheming plan to steal from victims. The process usually goes this way:
Vishers research their victims
The research process starts by sending random phishing emails, hoping that someone will reply and share their
Leave a number for those who don’t initially respond
Some phishing scams provide their victims with a
This strategy establishes confidence in their victims. It may even give the cyber criminal a clean slate. If the victim calls the number, he or she will be directed to a person who will complete the vishing scam.
Use social engineering tactics
If the intended victim answers the
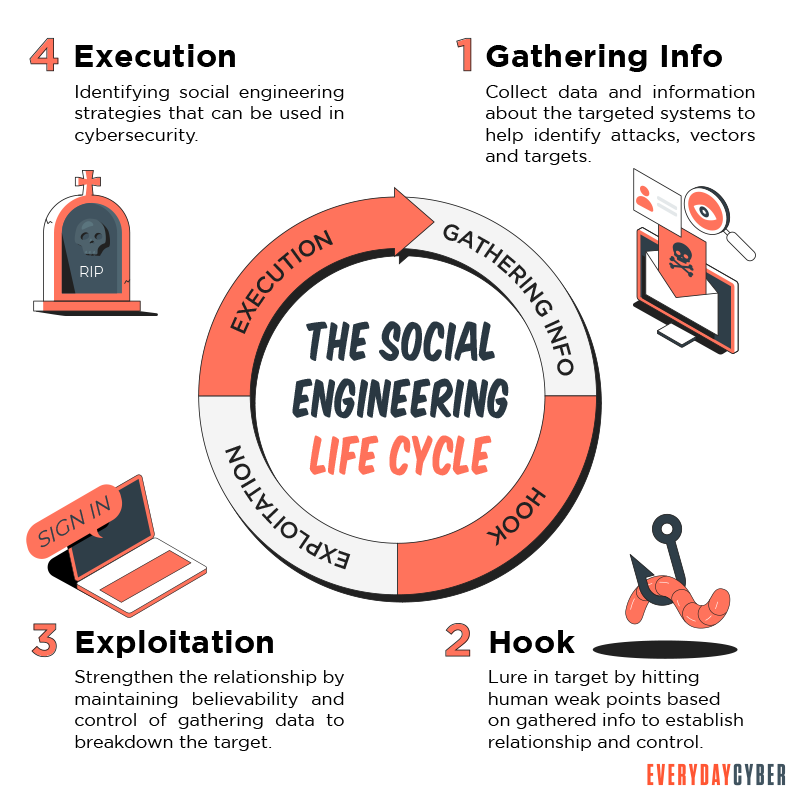
To trick their victims into believing they will benefit, fraudsters may employ all or just one of these social engineering strategies. Cybercriminals might request a mailing address, credit card information, bank account information, or work-related documents.
Harvesting the fruits
After gathering all the needed information, the vishing fraudster goes to work. They start draining bank accounts, making unauthorized purchases with credit cards, or stealing identities to commit other crimes.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Common Vishing Scam Examples
Vishing is gaining popularity among fraudsters because they don’t have to meet their victims in person to carry out their evil craft. Social engineering methods make it easy for them to convince victims to act on their requests. Here are common examples of vishing scams:
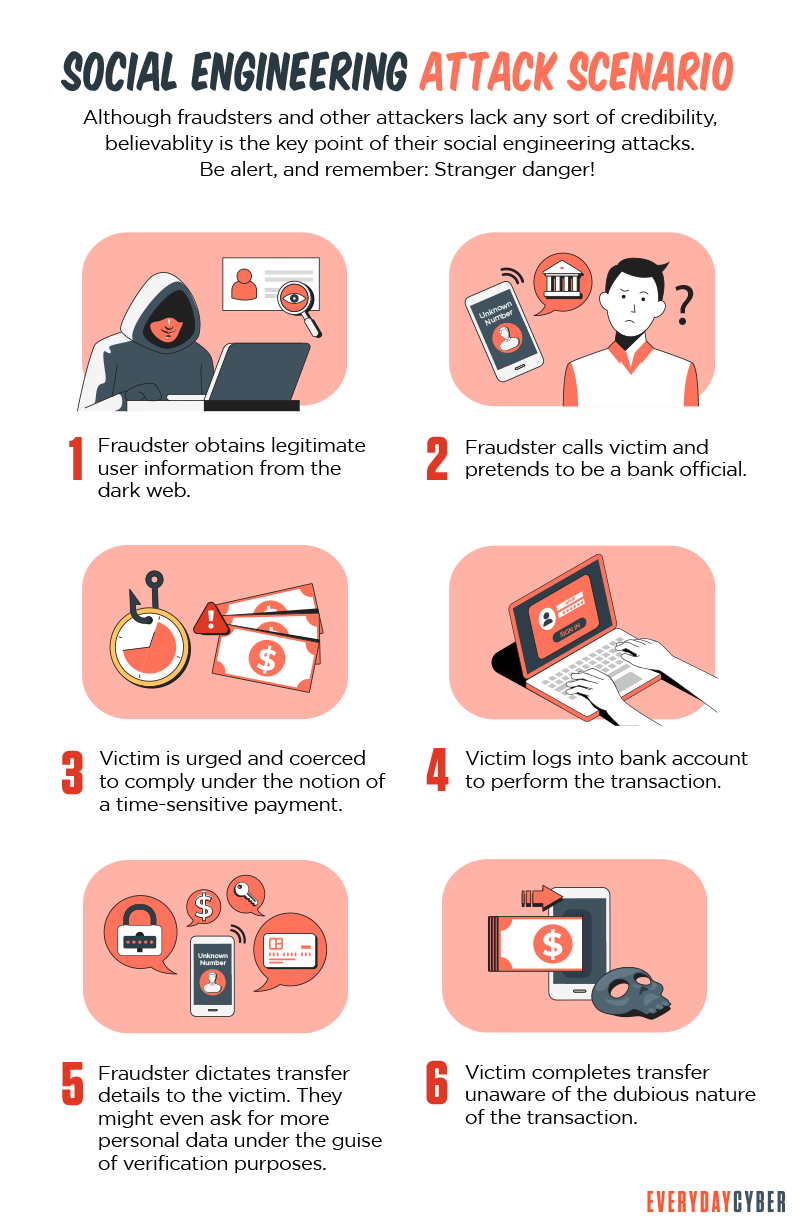
False alerts from financial institutions
The false alert may start with a text message, asking the target to call a number to resolve an issue. If the target responds, the fraudster decides that this person is a potential victim.
The fraudster calls the victim saying he or she is from the target’s bank or credit card company. The criminal informs the target that there is some issue with his or her account or credit card. If the vishing scammer gets access to the bank account or credit card, he immediately steals money or makes fraudulent purchases.
Unsolicited investment or loan offers
The opportunity to invest in a project or get a loan can get potential victims off guard. Vishers will go to work convincing their target to share personal and financial information. If the offer seems legitimate, the victim may be convinced to give up the information.
Social Security or health benefits scam
In some instances, con artists attempt to persuade their victims to provide their health plan details to take advantage of services. It’s also typical for scammers to pose as Social
This is the sad part. Attackers often target the elderly or sick people. They use the victim’s illness as leverage to persuade the target to provide their personal information. This could be a promise to sign them up for a refund or receive a check, but only if they provide private information.
Billing for a repair that didn’t happen
An alleged technical support service provider sends a link that opens a page informing you that a problem has been detected with your computer. The message requests you to call a number to receive technical support. If you respond to the call, the scammer will ask for your login credentials to proceed with the repair. In reality, there has never been anything wrong with your computer.
IRS tax scam
Impersonating an accountant, the vishing fraudster calls a taxpayer about an alleged tax deficiency. The caller offers a solution if the target is willing to reveal personal and tax data.
Vishing vs. Phishing
Vishing is a type of phishing. Vishing and phishing are both cyber attack methods that aim to steal
Prevalence
Phishing attacks are more common than vishing scams. In fact, 74% of American organizations encountered successful phishing attacks. Google has also registered more than two million phishing sites as of January 2021.
On the other hand, about 54% of American organizations experienced vishing attacks in 2020.
Method of delivery
Phishing attacks are aimed at a wide range of people through emails, text messaging, or malicious websites. The attacks are often automated.
Vishing attacks are directed at a lesser number of people through
Accuracy
Phishers typically have a vast knowledge about how to get into devices and networks. They use automation to target many individuals so they can catch more victims.
Vishing criminals typically do not have this knowledge. Their attacks are less accurate because one criminal can only take on one target at a time.
Information is obtained
Phishing attacks usually require the victim to click on a malicious link or download an infected file.
In vishing attacks, victims personally give up their information to the criminal over the
Types of Vishing Techniques
Cyber criminals use various techniques to carry out their vishing attacks. Here are the common ones:
Wardialing
Wardialing typically targets a specific area code and uses the name of a nearby business to hunt for potential victims. This strategy involves making hundreds or thousands of automated calls to numerous numbers.
As soon as the call is answered, an automated message starts. The caller will identify as a representative of a bank, credit card company, or government agency. The will then prompt the individual to enter his or her name, credit card information, bank account information, mailing addresses, and social
Caller ID spoofing
Many hackers mask their
VoIP
VoIP stands for Voice over Internet Protocol. It allows users to send and receive
Like caller ID spoofing, VoIP helps cyber vishers hide their
Dumpster diving
Digging into dumpsters behind buildings like banks, offices, or schools is a common way to gather
5 Ways to Protect Your Business From Vishing
Vishing isn’t only aimed at individual consumers. Vishing enthusiasts found that there’s more information and money in businesses. Vishers are a shrewd breed but there are ways to prevent vishing attacks to protect your business. Consider the following:
1. Provide vishing security awareness training to your employees
Your employees are on the front-lines, and they need your support.
Include surprise vishing simulations in your training program. This will allow your employees to experience first hand how to spot the signs and how to prevent attacks.
After your vishing exercises, it’s a good idea to evaluate the results and prepare a report with suggestions for the following steps. For specific jobs or users, this will typically be included in the next training.
The more relevant their training is to their daily tasks, the more they’ll remember and the more engaged they’ll be.
2. Enforce a zero-trust culture
Zero-trust limits access to information, authority, and privileges to those who need them in their work. The rest are off-limits. For example, if you store bank account information in a secure wallet but allow everybody to have access to it, it only takes one human error to compromise all.
3. Be wary of unfamiliar phone numbers
Never trust
It’s not unethical to hang up on a stranger. But if you do answer, never give sensitive personal information or confidential corporate data.
To verify the validity of links included in emails, hover your cursor over it. You can see here where the link will lead. Entering the right URL into the address box is an even safer way to access the website.
4. Install a caller ID app
Using a good caller ID software can improve your
The caller ID app can block spam numbers, while allowing good numbers to go through. If a number does end up being a vishing scam, you can add it to the database of spam numbers.
Just a word of caution. You may still receive phishing calls from spoofed numbers that appear to be valid. Avoid these numbers and those not in your
5. Watch out for strange requests from random callers
Any demand for sensitive information or actions that you don’t normally do could be signs of a vishing attack. These could be keying in your credentials, clicking a link, disabling
Our Final Thoughts
The vishing threat isn’t expected to go away anytime soon. You have all the more reason to protect yourself and your business from it. A good defense is to understand how vishing works and know the warning signs. The final line of defense is strong
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What to do if your phone is lost or stolen
When your phone is lost or stolen, it is more than just a pricey handheld that is lost. Our phones keep track of our lives. If you’ve lost your phone, there are things you can do to track, locate, and recover it depending on the type of phone you have. Read this to get tips on how.
Is a Cybersecurity Risk Assessment Worth the Money?
A cybersecurity risk assessment does more than just identify and analyze threats. It counteracts threats and keeps your IT systems safe.
What is Business Email Compromise (BEC)
Business email compromise is one of the most financially destructive cyber crimes. These are emails that appear to be sent by known or trusted sources asking for something legitimate.
What to do if your email Is hacked
Identity theft and bank account or credit card fraud are both possible consequences of a stolen email. If you suspect that your email has been hacked, act quickly to limit the harm. Here are 9 steps to take back control of your email if you have been hacked.
What is Social Engineering?
Social Engineering in the digital world is the intentional deception and manipulation of victims to cause the release and sharing of confidential information used to commit fraud and other cybercrimes.
14 Ways to Secure Your Home Wireless Network
Many homeowners are just unaware of the security threats that a wireless network might provide if not adequately safeguarded by a secure Wi-Fi network. We would never leave our house's front door unlocked. So you should do the same and never leave your Wi-Fi networks unprotected since it exposes you to the same or even worse threats.


