Smart devices are everywhere and rapidly becoming ubiquitous in our lives. Our homes are now full of smart devices. From smart TVs and thermostats to baby monitors and smart speakers. They bring convenience to our lives and we are becoming increasingly dependent on them. They can make our lives better, but they can also make our homes and digitally connected lives vulnerable to attacks by cybercriminals. That’s why it is more important than ever to have a plan to defend against such threats.
In today’s digitally connected world – if you connect it … you need to protect it.
Your smart home and its devices are at risk
Internet of Things (IoT) – IoT devices, which include everything from a smart fridge or smart washing machine to a smart speaker, create new targets for hackers and bad actors to exploit.
A hacker could do a lot of things if they gain access to one or more of your smart home devices. Here are just a couple of examples.
- What if they get access to your smart speaker and its digital assistant who recorded your password you use to access a financial service.
- Imagine they gain access to your network through a smart appliance. Infect it with ransomware locking you out of your network and all attached devices. Then demanding a ransom to unlock access with no guarantee of the hacker will restoring it.
- What if they get to your smart thermostat and are able to see you lower the temperature from 8am – 4pm. Suggesting you may be at work during those hours and the house is empty.
These just touch the surface. Even connected lightbulbs, equipped with infra-red sensors, are now being exploited. Scenarios like these raise alarm bells and represent just a sampling of the
Why are smart devices and smart homes vulnerable?
Turns out that
The other noteworthy point is that security has not been a top priority of smart device and IoT manufacturers. Manufacturers may change going forward as the market demands it, but currently, things are still weak. Examples of poor device
- Default or hardcoded passwords, which cybercriminals exploit.
- Inability to manually or automatically update the device’s software or firmware creates vulnerabilities.
- No hardening of the device operating system. Which, when done, creates a natural
security barrier.
Securing your smart devices starts with securing your home’s network
Every home with smart devices has a network (likely a wi-fi network) which your smart devices connect to and through which they connect to the internet. Home networks are built with one or more wi-fi routers. The router is the digital “front-door” to your smart home and like the front door of your house it needs to be tough and protected with locks to keep unwanted actors from entering.
A secure smart home starts with a properly configured wi-fi router. It is the foundation of a smart network and enables all your devices to connect to each other and to the internet.
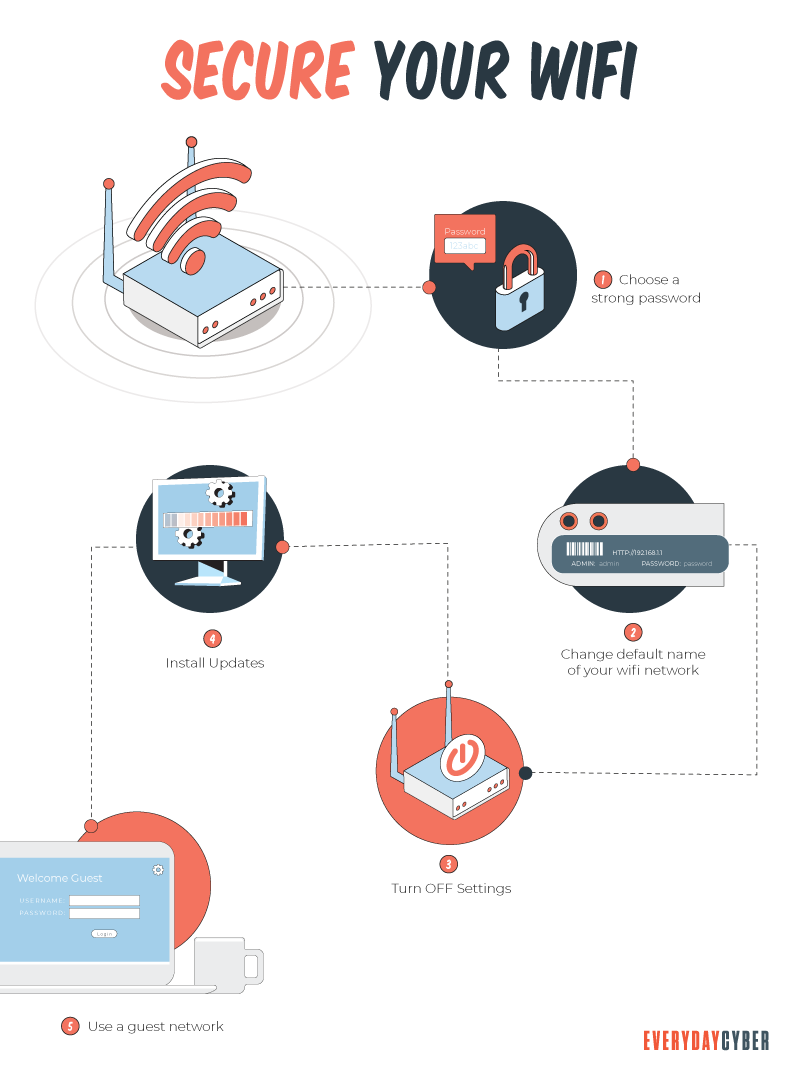
Many people use the router provided by their internet service provider (ISP) and in most cases that is fine. But it is recommended, whether the ISP supplied router or one of the many you can acquire in the marketplace, the default settings should be reviewed and change where necessary. A secure router is the basis of a sound and secure smart home.
You can take many other steps to ensure your devices and home network are secure and protected against the evil intentions of cybercriminals.
We have collated the 10 BEST tips for securing your home’s smart devices and building a genuinely secure smart home.
- Modify the wi-fi router name & turn off broadcasting it
Most routers are configured with default names that indicate their make/model; leaving it as the manufacturer’s default can allow a potential attacker to identify the type of your router and possibly exploit any known weaknesses to gain access to your network. All wi-fi routers enable their name to be changed and disable the public broadcasting of that name. It is possible that if you are using an ISP-supplied router, they may lock down such changes. If that is the case, you may have to ask them to make the change on your behalf.
At a minimum change your router’s name (known as the SSID) to something unique and consider disabling the public broadcasting of the SSID. A unique name will limit exposure of personal info about you or the router details. Disabling SSID broadcasting will make it more challenging for attackers to find your network.
- Change the Router’s Default Username & Password
Most routers are configured from the manufacturer, or supplied from an Internet Service Provider (ISP), with a default username and password for the router’s admin user.
In the case of a router from a router manufacturer, the default usernames and passwords are published on the internet or known to cybercriminals because it’s been mentioned in a forum. Default values are also documented in the manufacturer’s install guide. Bottom line … hackers know the default values, and they also know that most people don’t change the defaults. It makes these routers and the users who have them and didn’t change the defaults. Easy targets for them to exploit.
Don’t be a victim. Change the router admin user’s username and the admin password to something strong.
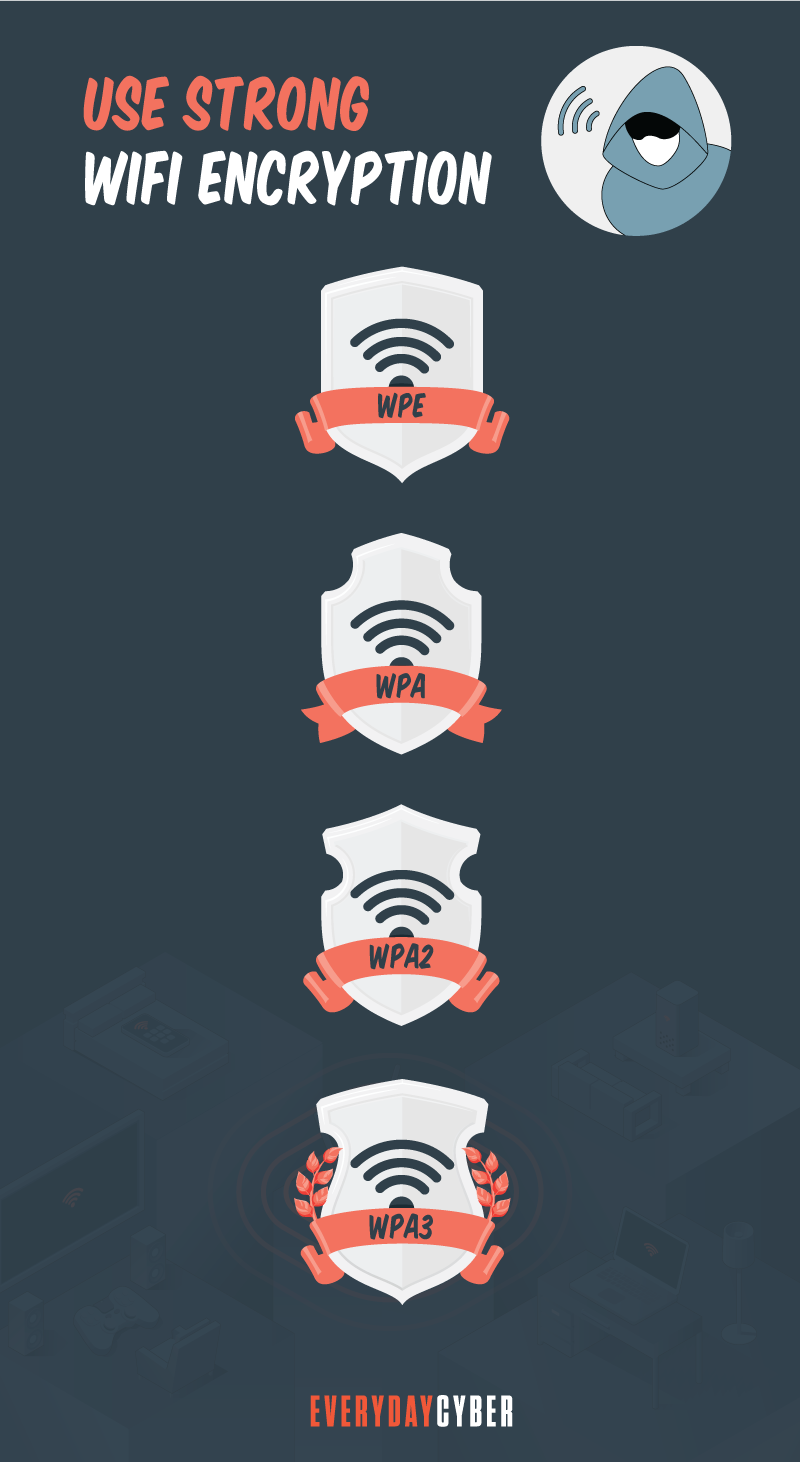
- Configure your router to use wi-fi encryption
Modern wi-fi routers support encrypting all traffic between it and the devices that connect to it. Ensure that your router and the devices connected to it are using (wi-fi Protected Access) WPA2 or preferably WPA3. It is a configuration option on all modern routers and wi-fi enabled devices.
- Set up a separate network for your IoT and smart devices
Separation and containment strategies are the gold standard in cybersecurity for creating secure networks. Most modern wi-fi routers support creating multiple networks, and we would highly recommend that you have a minimum two (2) separate networks. One is for your home IoT/smart devices and one that you use for connecting devices (laptops, smartphones) that may contain sensitive data or connect to confidential sites like banks.
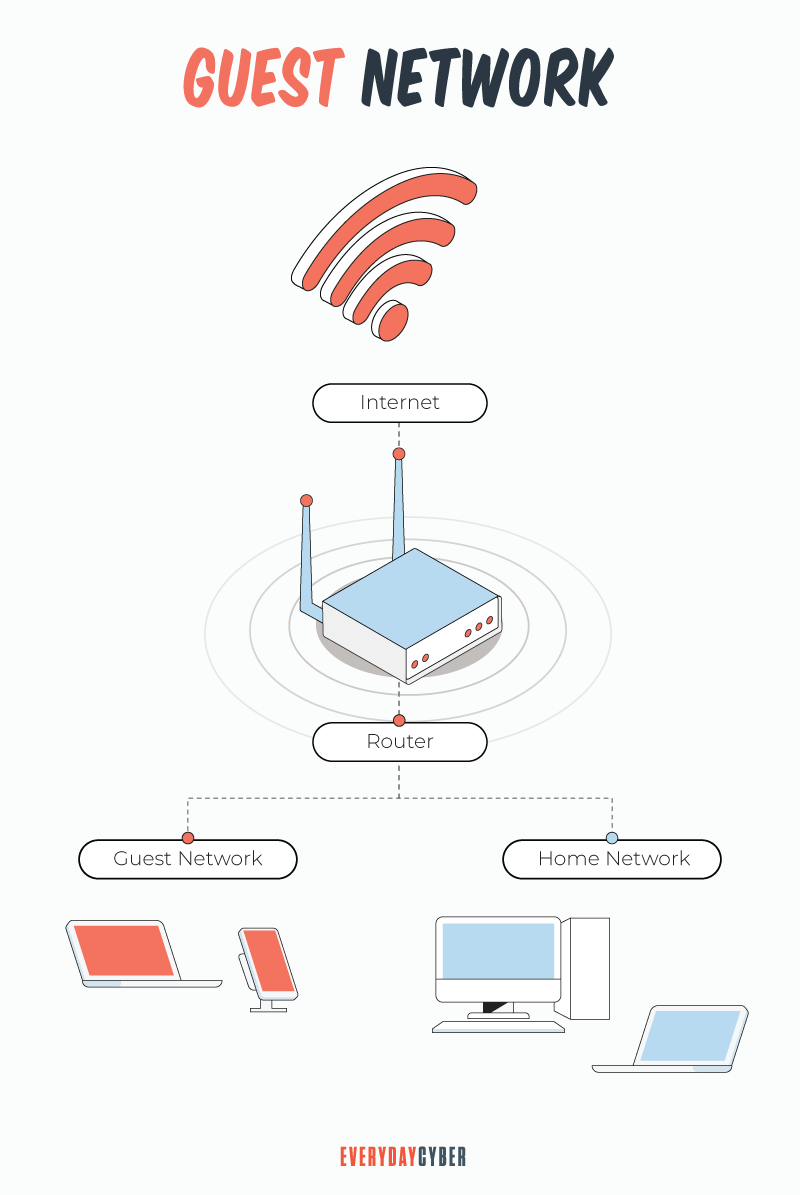
Creating separate networks means that if one of your home’s IoT or smart devices is somehow compromised, the hackers still won’t be able to access your sensitive data on your computer or
- Use Firewalls
In any home network, you can have multiple firewalls enabled. Firewalls can block malicious traffic from entering your home network or entering a specific device. They also will alert you to potentially dangerous activity. Most newer wi-fi routers have firewalls built-in, as do many smart devices. Most smartphones, tablets, and computers also have built-in firewalls. Where a device doesn’t have a built-in firewall, most antivirus/antimalware software suites you should install on your devices will include a firewall.
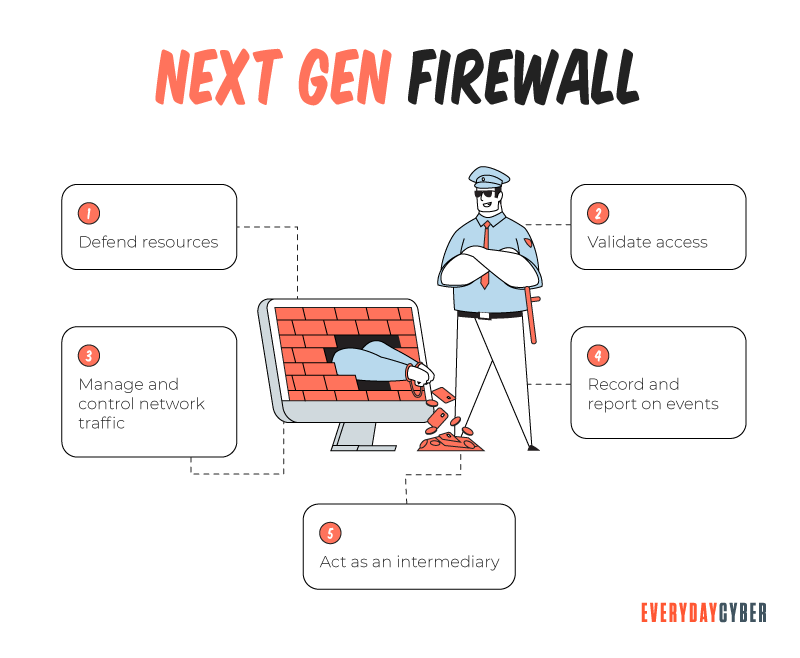
Firewalls control the doors that you open or close to let data flow in and out of your network and your devices. Even the default settings increase your
- Use a strong and unique password on each device
Every IoT/smart device is shipped with default usernames and passwords from the manufacturer. Cybercriminals know these defaults and exploit them because many users never change them.
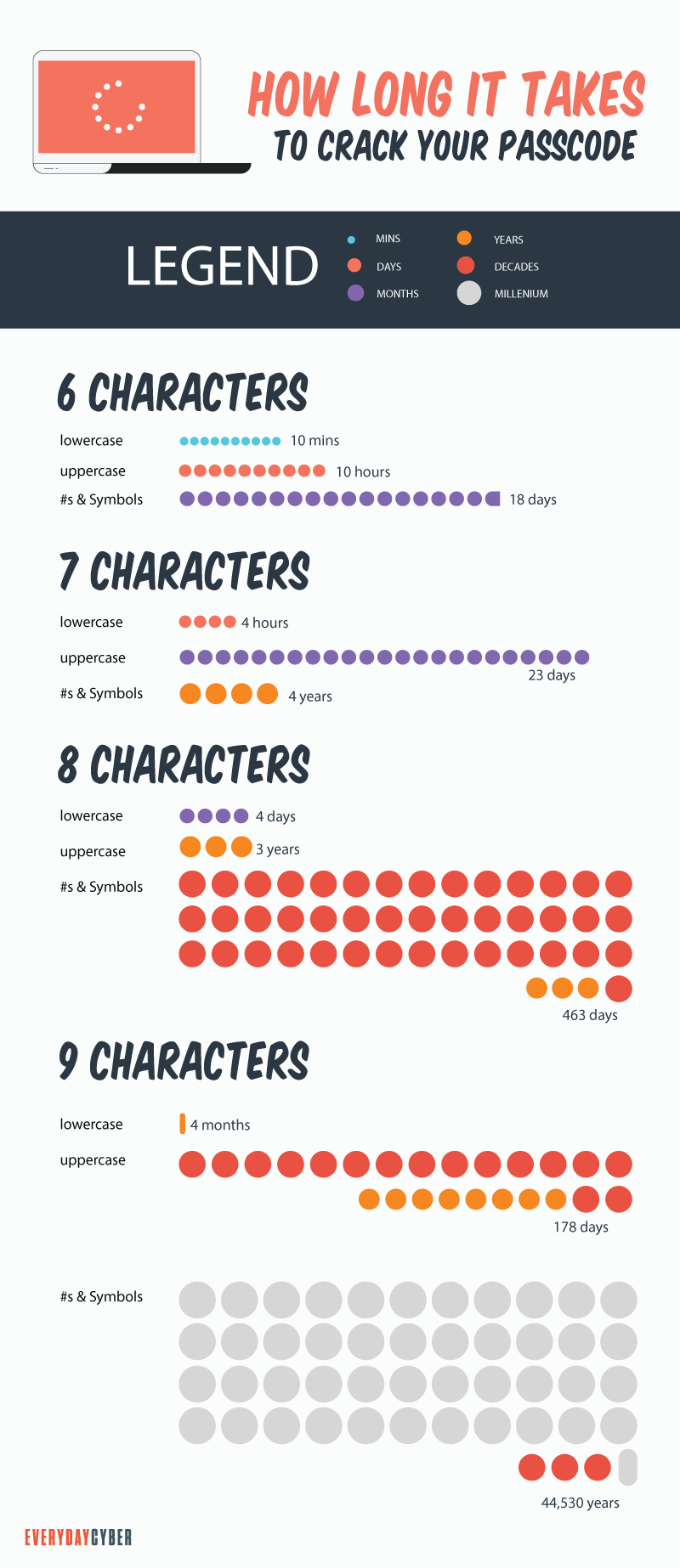
Don’t be a victim. Change every device to have a unique username and password. Use strong passwords– alphanumeric and special characters, twelve (12) characters or longer. Make sure NOT to use the same password twice because if one device password is cracked, the first thing hackers do is use that same password to break into other devices. You increase your
- Use Multi-Factor Authentication when its available
Cybercriminals have gotten pretty good at figuring out and breaking passwords. To combat that multi-factor authentication (MFA) was developed to make it more difficult for them to access devices and apps. The most common MFA is two-factor (2FA) authentication.
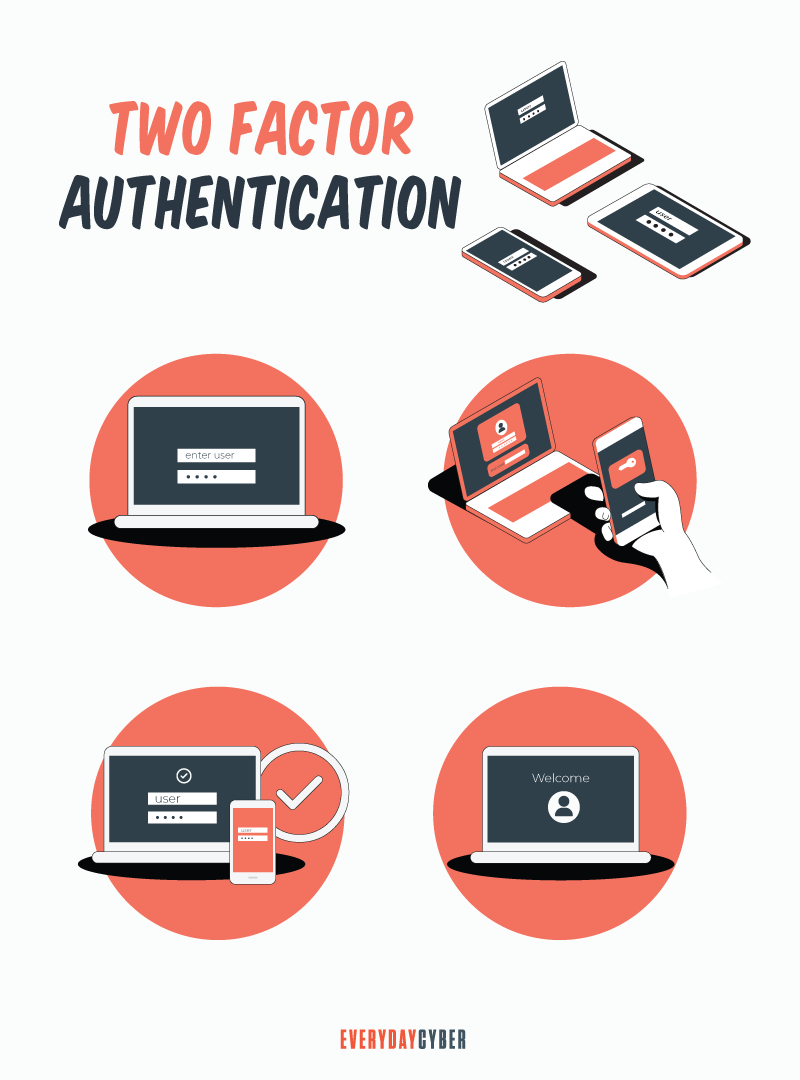
2FA has an additional step – for example, having a one-time pin (OTP) – sent to your
- Always keep your devices updated
One of the primary threats we all face from cybercriminals is them exploiting old vulnerabilities in our devices and applications. They know many users do not keep their devices or their software current with the latest patches. Users forget, get busy, don’t know they should be updating regularly, or maybe just lazy. Regardless of why hackers know this is happening. They focus their attacks on devices and apps they know have not been updated.
Many of the updates or patches that device and app makers release are to fix
When your device or app maker notifies you of an update or a patch, don’t put it off. If your device allows automated updates – turn that feature on. If your device maker doesn’t notify you of updates or patches or if the device or app does not automatically download and apply them, check their websites regularly to see if they have any available.
Apply updates and patches regularly to stay safe.
- Avoid using Public wi-fi for accessing your home network or devices
Public wi-fi networks like those in airports and cafes are cybercriminals’ favorite hangouts. These are some of the least secured networks and can be a treasure trove for hackers and bad actors to accumulate enormous amounts of information about users connecting to and through those networks.
Always assume a Public wi-fi network is unsafe and that any data you send over it can be collected. Do not connect to your smart home through it unless you are using an encrypted link such as one you can get by using a virtual private network (VPN).
- Turn off smart device features you don’t need
There is a concept in cybersecurity called ZERO-TRUST. Its premise is that when configuring a network, an app, or a device, you set it up with the most
By default most IoT/smart devices are configured to send all types of data. A key recommendation is to configure your smart devices only to do the actions you want them to do and turn off everything else. This strategy lets you use these devices the way you want and limits your exposure to cybercriminals that compromise your device through features you don’t even use.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is a Keylogger?
Keylogger is a digital surveillance tool. They can track every click, touch, key stroke, download and conversation carried out on the device they are installed on
What is a Rogue Certificate?
A rogue certificate is a valid certificate issued by a legitimate certificate authority. However, it’s untrustworthy because either it was compromised or was issued to the wrong party.
Things About Ryuk Ransomware You Need to Know Right Now
Ryuk ransomware is one of the most dreaded malware to date. It encrypts or steals corporate data to extort millions of dollars from its victims. The Covid-19 crisis greatly influenced the recent rise in ransomware. The remote work response to the pandemic created huge gaps in the worlds cyber defenses. Threat actors saw these vulnerabilities as opportunities to spread large-scale ransomware attacks.
What is Malware?
Malware or “malicious software” is a cybersecurity term used to describe software that steals your data, spies on you, damages your devices, and generally causes chaos and destruction.
What is Shoulder Surfing?
Shoulder surfing is a form of social engineering that enables cybercriminals to gather information just by looking over their victims’ shoulders. The aim of shoulder surfing is to obtain personal data, such as usernames, passwords or personal identification numbers (PINs), bank account numbers or credit card numbers.
What to Do if You’ve Fallen Victim to a Phishing Attack
Cybercriminals target phishing scam attempts on fatigued workers in the hopes of catching them off guard with an attention-getting email. They also launch phishing schemes against unsuspecting individual users by using fear and intimidation. And it sometimes works.


