Identity theft is big business for cyber criminals, but a devastating experience for victims. It’s out of control and worse than you think.
Millions of Americans and people all over the world are affected, resulting in billions of dollars in losses each year.
Identity fraud is everywhere. Almost every day, we see news reports describing new techniques for crooks to steal your personal information, as well as warnings about big data breaches that expose your sensitive data to hackers on the Dark Web.
The Sad Reality
Yes, it’s happening.
According to a Debt.com research from 2021, four out of ten people had been victims of
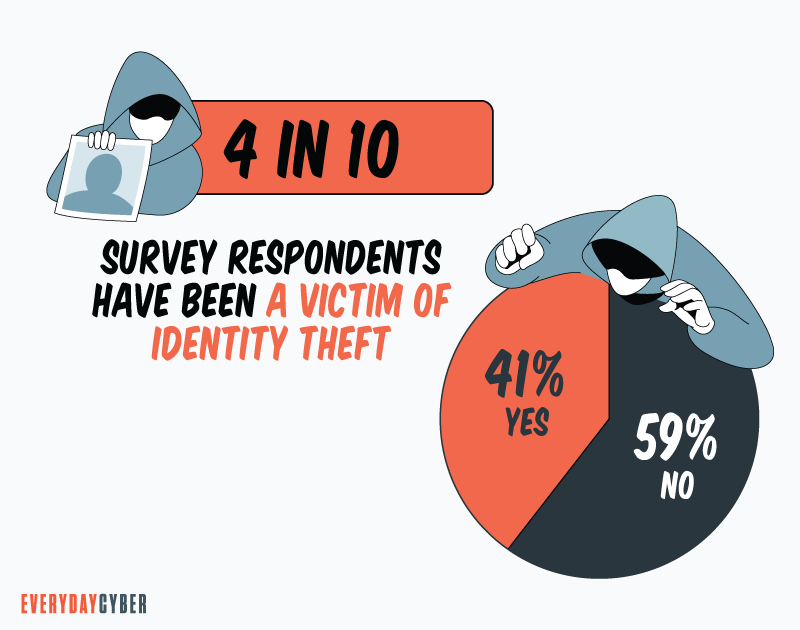
A report released by the Federal Trade Commission in February 2021 revealed that Americans lost $3.3 billion to fraud in 2020, up from $1.8 billion in 2019. The proportion of Americans reporting losing money to fraud is also rising, with 34% of 2020 fraud report incidents involved financial loss, up from 23% in 2019.
Here are some other shocking realities that everyone should be wary of:
Every 14 seconds, someone falls victim to identity theft
Tactics used in stealing identities are evolving and becoming more sophisticated . Because of this,
Experts believe that due to the increasing frequency of thefts, someone becomes a victim every 14 seconds. According to most research, this rate will rise in 2022, making it an even bigger problem for Americans.
In the United States, identity theft cost $56 billion in 2020
In 2020, about 49 million people were victims of

One of the most revealing facts is that direct-interaction scams, such as phishing emails, resulted in a significantly larger loss of $43 billion. This means that bad actors are becoming more daring and willing to steal from individuals directly.
33% of Americans have been victims of identity theft
According to Proof Point, 33% of Americans have experienced
40% of account takeovers occurred in a single day
Fraudsters are quick in their attempts to take over accounts, according to Javelin Research. The company’s 2020 research on
The pandemic provoked cyber crooks to intensify their stealing campaigns. In fact, account takeovers increased by 307% since its start in 2020.
2.2 Million fraud reports were filed with the FTC in 2020
According to the Federal Trade Commission (FTC), the victims also lost $3.3 billion in fraud in the same year. That’s nearly double the money lost to
The most common type is credit card fraud
According to the FTC, credit card fraud is the most common form of attempted
These and many more statistics show that
While “malicious outsiders” continue to steal data, users still bear a large portion of the responsibility for their lost data. Current patterns indicate users still tend to be less concerned about managing their own data
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
So what is Identity Theft?
Identity theft happens when someone steals your personal information and uses it to commit fraud and leverage it to commit other crimes.
Personally identifiable information (PII)
Personally identifiable information is information that can identify an individual when used alone or with other relevant data.
Personally identifiable information include:
- Name, date of birth, home address
- Social
Security Number - Financial information, such as bank, credit card, loan, and crypto accounts
- Passport
- Driver’s license number and other valid IDs
- Usernames and passwords
- Health ID
- Employment ID
- Tax identifications number
How criminals steal identity
Consumers cane become victims of
Increasing in frequency is online
- Fall for phishing schemes
- Unwittingly download malware that steals their information from their computers or devices
- Use insecure public Wi-Fi
- Use ATMs that are equipped with a skimming device that captures login credentials and personal information
- Share passwords with untrustworthy people
- Become victims of data breaches
- Fall for phone scams that ask for personal, banking, or credit card information
Types of Identity Theft
The first step in protecting yourself from

Identity theft has evolved from isolated cases to epidemic levels, courtesy of cyber thieves who are relentlessly looking for new ways to steal other people’s information and money. There are as many types of
1. Financial identity theft
This happens when criminals gain illegal access to your bank, credit, or loan accounts. Once criminals acquire enough personally identifiable information about you, they can cause a lot of financial harm.
Thieves can engage in the fraudulent creation of new accounts. They can open new banking, credit, or credit card accounts in your name. They can make fake charges using your good credit history.
A burglar can take your home equity through a bogus line of credit (HELOC) or refinanced mortgage using your information.
Your financial information can also be used by criminals to get bogus loans or lines of credit in your name.
A thief can make fraudulent transactions online even if they don’t have your physical credit card. They can also use your credit card details to produce a “cloned” version.
Financial fraud caused by
The red flags:
- Being unable to access your online banking account
- Discrepancies in your bank account balances
- Calls from debt collectors about unpaid mortgage or loan amortizations
- Debits on your credit card for purchases you didn’t make
- Charges on your credit card that are unusual or unexpected
- Unidentified queries on your credit report
- Your credit score has drops unexpectedly
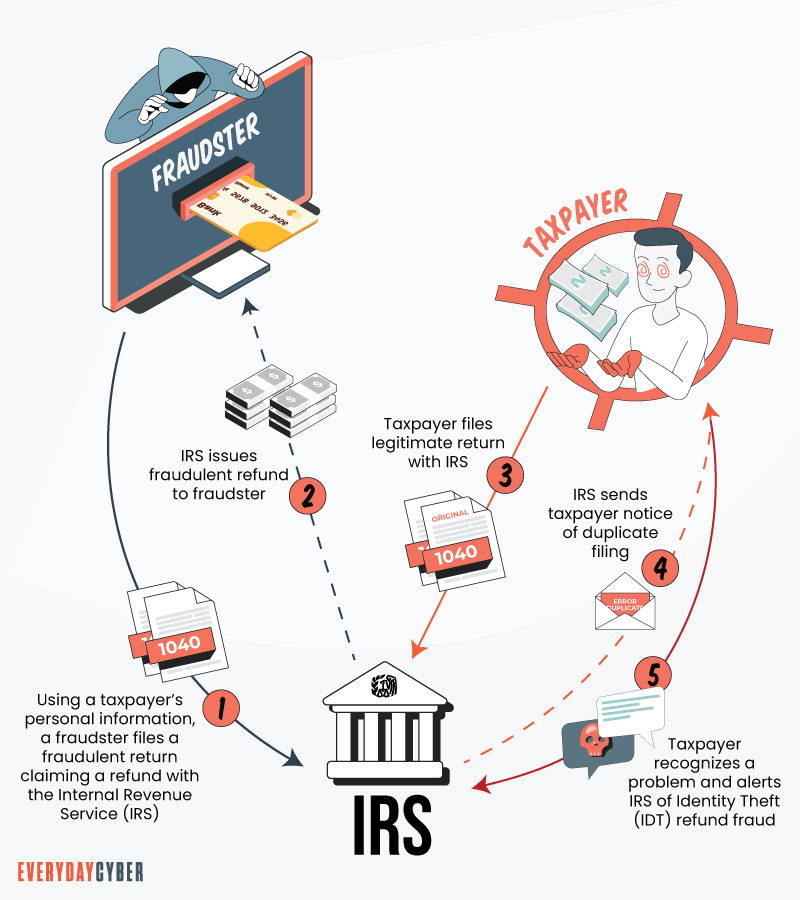
2. Tax identity theft
A tax
The red flags:
- Receiving tax records, forms, or transcripts that are unfamiliar
- Scammers posing as IRS agents calling you about tax issues
- Your tax preparer is unable to explain inconsistencies.
- You’re unable to file your tax return because someone else filed one using your Social
Security Number - You receive an IRS notice or letter citing some information you know nothing about
3. Medical identity theft
Medical
For example, a thief may impersonate you and obtain surgery or other medical treatments using your stolen health plan information. You won’t find out about it until you receive a bill in the mail. Worse, the phony treatments are permanently recorded in your medical records. This could lead to a misdiagnosis or the loss of critical medical treatment.
The red flags:
- Medical expenses for treatments or procedures you didn’t receive
- Incorrect medical record entries
- Your insurance company sending you a change-of-address notice
- Insurance claims being denied because your benefits have been exhausted
4. Child identity theft
Children have been prime targets for
The red flags:
If your child is receiving credit card offers or
5. Employment identity theft
Some criminals use your
This may appear to be less harmful. However, having confusing employment records might pose problems with your credit, Social
The red flags:
- Your Social
Security statement suggests you made more money than you actually did - You’re required to submit W-2 0r 1099 tax forms for jobs other than what you do
- You’re refused unemployment benefits because you made more money aside from your regular employment
6. Criminal identity theft
You may be arrested if someone took your driver’s license and used it to commit a crime. As a result, you may be held liable for the crimes of that thief.
The red flags:
You may be detained by a police officer for a crime you didn’t commit. Or you may be denied employment or a promotion because of some negative thing found in your background check.
Other types of
- Elder
identity theft - “Friendly” or familial
identity theft - Unemployment
identity theft - Government benefits
identity theft - Synthetic
identity theft - SSN
identity theft - Account takeover fraud
Who are Most Vulnerable to Identity Theft
Consumers of all ages have reported criminal events at similar rates in previous years. The figures today present a different situation. Consumers aged 40 to 69 are reporting increasing rates of
Here’s a look at the prime targets of
Seniors
Seniors are more vulnerable to online phishing and telephone frauds than younger people because they are often less tech-savvy.
While the figures for seniors are likely to be substantially higher, an AARP poll indicated that victims 55 and above were significantly less likely to admit to being scammed. Tax
Children
Thieves often have a bad credit history. This is why they particularly target children because they can use their Social
College students
Students are particularly vulnerable to
Military personnel
Active-duty military personnel are less likely to detect any discrepancies in their credit reports while deployed. Because they move frequently, the chances of their personal information being exposed is greater.
How to Protect Yourself from Identity Theft
It’s crucial to be aware of how

Here are 10 things you can do to make it much harder for thieves to steal your
1. Be aware of the most common ways identity crooks steal your identity
We’ve discussed this topic earlier in this post but we want to emphasize its importance. Criminals need access to your PII in order to steal your
Identity burglars use other tactics to get hold of your
You could also be at risk when you respond to unsolicited messages or calls, lose a piece of mail, use your devices in public, or visit the Internet.
2. Heed the warning signs
This especially applies to phishing attempts. Scammers use phishing techniques to deceive you into handing over your personal information. Texts and
Scammers frequently try to spoof their contact information to make it appear to be coming from a legitimate
Phishing emails don’t mention your name, may contain grammar mistakes, and frequently use threat, urgency, or enticing promises for you to act. They may also contain links or attachments with compelling reasons to click or scan them.
If you have any suspicions, do not respond or click on any links or attachments. Instead, use the information on the company’s official website to contact them directly.
3. Keep your personal and financial information safe offline and online
Ensure that your personal and financial information are kept physically secure in a safe place, especially if you have roommates, coworkers, or house help. This includes your wallet or purse that carries your IDs. Here are some safekeeping tips you should consider:
- Make sure your bank account statements, credit card statements, and sensitive information on other financial accounts are kept away if you have employees working in your home.
- Shred sensitive materials, such as credit applications or credit offers, insurance forms, medical statements, charge receipts, checks, and bank statements, and canceled or expired credit and ATM cards.
- Never leave your credit, debit, or ATM card receipts in public, such as at a bank or a store.
- Outgoing mail should be deposited at the post office or in a PO collection box, not in an insecure mailbox, while incoming mail should be collected quickly. Rather than having new checks mailed, pick them up at the bank.
To protect your personal information online, refrain from posting them on social media and elsewhere online. Make sure your social network privacy settings limit who may view your information, such as your birth date, home address, workplace, and photos. Examine your friends or connection lists and restrict people you don’t know.
Whether you’re buying at a retail store, joining an online club, or receiving a phishing email, asking for your information is a common technique to collect your information.
You have the right to say no, especially if it’s unclear how the information is needed for the service or transaction. To buy a pair of jeans, for example, you don’t have to give your complete address. Also, never give out personal information to strangers over the phone or by email.
4. Use strong passwords
Identity thieves love weak passwords, especially if you use the same password everywhere. Once the criminal has your password, they can get into your accounts and cause havoc.
Use passwords with more than 10 characters, upper and lower case letters, digits, and symbols. Never include personal information such as your name, age, birthdate, or the name of your pet. Best practices for password management include password managers, two-factor authentication (2FA), and changing passwords regularly.
5. Avoid using public Wi-Fi
It’s convenient to have free wireless Internet at an airport or a local coffee shop. However, it also provides the ideal chance for scammers to steal your personal information.
Hacking public Wi-Fi networks is common. If your connection is intercepted, an
6. Monitor your accounts
This involves examining your bank and credit card accounts, mortgage or loan accounts, health insurance, and credit report, among others. Look for any suspicious activity and contact your bank, credit card company, or health insurance provider to verify.
You’re also entitled to a free copy of your credit report from each of the three main credit agencies once a year under federal law: TransUnion, Experian, or Equifax.
Note that a credit report is different from a credit score. A credit report contains a detailed list of your credit account activity, while a credit score is a number that indicates your creditworthiness.
For added protection, you can use two tools on your credit report:
Before giving credit, a fraud alert requires lenders to verify your identification. A one-year credit freeze with the three credit reporting agencies is standard, but you can extend it for another seven years.
A credit freeze stops your credit files and reports from being shared with others. If you strongly believe that you have been the victim of
7. Reduce your online presence
Your online footprint includes everything you do online, including Google searches, social media posts, and purchasing habits. Bad actors use this data to create phishing emails, guess your passwords, and even name-drop your friends to convince you to act.
You won’t be able to completely delete your online trail, but you can minimize the information that scammers have access to. Here’s some advice:
- Make changes to your
security and privacy settings. - Limit social media sharing.
- Remove old or inactive accounts.
- Set up a Google Alert for yourself.
- Use privacy browsers like Brave and non tracking search engines like Duckduckgo.
8. Protect your mobile devices
Check mobile app permissions because personal data is also affected by mobile apps. To download the app, many require you to approve certain permissions, such as access to your contacts, images, and GPS position. In many instances, some permissions aren’t relevant to the service you need.
For your protection, review the permissions settings for each up and turn off those that are inapplicable.
9. Invest in security software
Antivirus and
Other
Make sure any operating system upgrades are updated as well.
10. Know who you’re dealing with
When someone calls you and asks for personal or financial information, find out who they are, name of the company they represent, and why they are calling. If you believe the request is valid, call the company directly and double-check what you were told before disclosing any personal information.
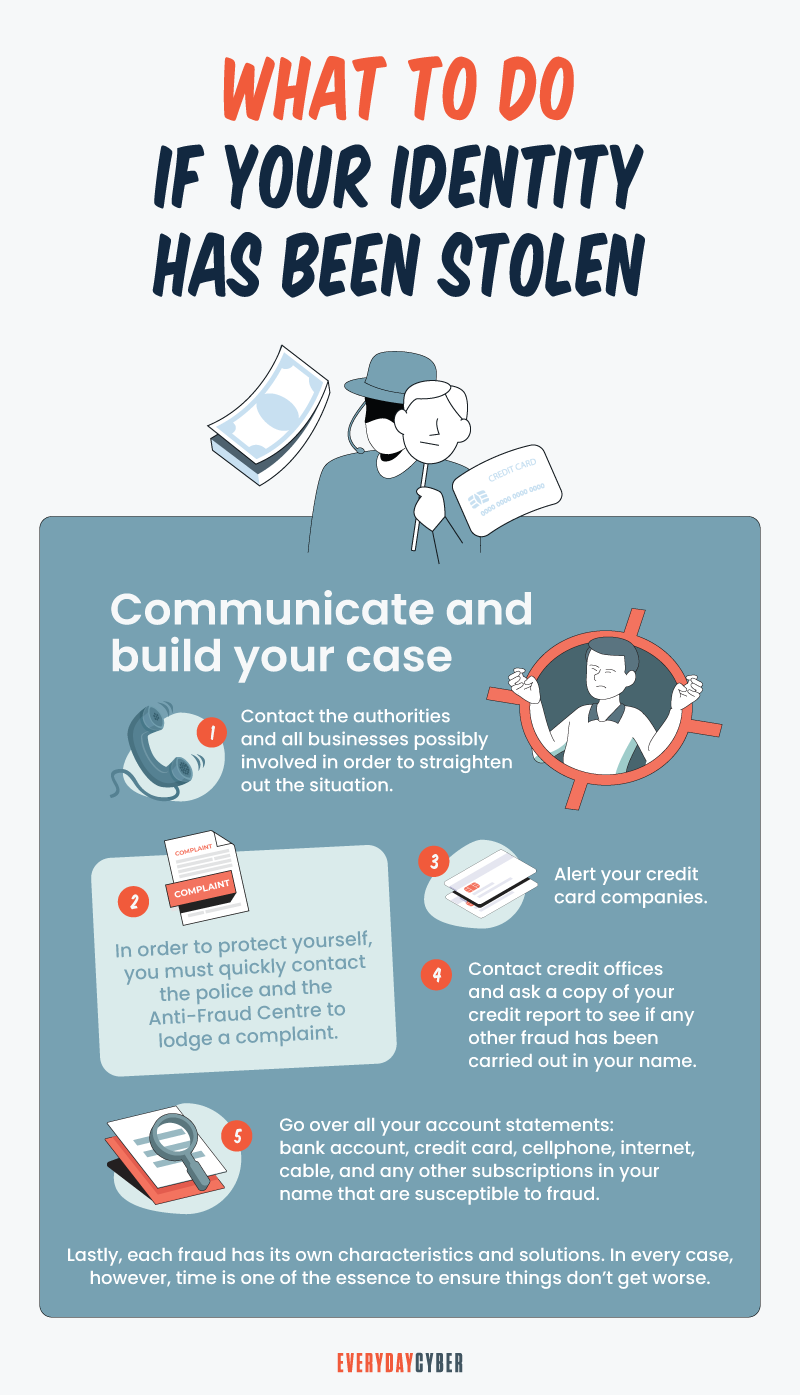
What to Do If You’ve Fallen Victim to Identity Theft
As soon as you realize you’ve been victimized, here’s what you should do immediately:
- Inform your bank, lenders, and other affected companies.
- Notify the three major credit bureaus so they can place a fraud alert on your account.
- Report the
identity theft to the FTC. - Report the
identity theft to the police and other appropriate federal agencies. - Dispute fraudulent transactions with the companies where fraud took place.
- If you have
identity theft insurance, inform your provider who can help you through the steps to recovery.
Our final thoughts. Identity theft is a nightmare nobody wants to experience. But a lot of vigilance can help you avoid the fallout. To do that, you should adopt proactive and preventative measures to keep your information secure.
If you’ve been victimized, don’t lose hope. Many credit card providers and banks offer zero-liability fraud protection as long as the fraud is reported promptly. Check their policies regarding reporting deadlines and reimbursement restrictions.
Investigations into fraud might take weeks or months to complete. Some companies may instantly refund your money for fraudulent transactions. Others may withhold reimbursements until a settlement is reached.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is a Computer Worm?
A computer worm is not a cute, squiggly little creature. It is an evil, malicious piece of software destined to wreak chaos and disaster on many devices.
Piggybacking in Plain English: 6 Ways to Keep Your Neighbors from Stealing Your Wi-Fi
Stopping piggybacking all boils down to vigilance and protecting your Wi-Fi with a good VPN, antivirus software, firewall, and security patches.
What is a Password Manager?
A password manager is an encrypted storage system for keeping and managing passwords usually protected by a master password. Some password managers use biometric data to protect the vaults instead of master passwords. Still others support the use of two factor authentication for higher security.
What is an Ad Blocker?
An Ad Blocker is an app or browser extension that stops ads (popup, banner, inline) from displaying on your desktop or mobile device.
What to do if your phone is lost or stolen
When your phone is lost or stolen, it is more than just a pricey handheld that is lost. Our phones keep track of our lives. If you’ve lost your phone, there are things you can do to track, locate, and recover it depending on the type of phone you have. Read this to get tips on how.
Strong Passwords. One giant step to protect our digital lives
Here's how to create long, complex, and unique passwords to protect your accounts and keep your sensitive info safe from hackers.