
Have you noticed that you can’t move an inch without an internet connection? Think smart phones, smart fridges, smart cars. Almost everything we interact with now connects us to something, someone, somewhere.
It won’t be long before we all have to sign up to washmenow.com to wash our clothes. Think about it. Soon, your washing machine won’t work unless it can talk to the cloud. You’ll need an account on washmenow.com just to wash your underwear.
You need online accounts for everything. All these accounts need login credentials – typically a username and password. Guess what a hacker uses to steal our
Your kingdom for bad passwords
Bad passwords are the worst cyber
Threat actors are always after your devices and systems. They can easily break bad passwords and use them to cause havoc and steal your data. If you don’t want to get hacked, use complex passwords.
Using the same passwords for your email, bank account, and all other accounts is risky. It increases the chance of unauthorized access to your bank account to steal your money. Passwords leaked in data breaches are even more deadly.
The Shocking Stats
Are you familiar with “qwerty”? Studies show some mind-blowing statistics about the worst passwords. They are usually the most common passwords. And they inflict chaos and leave a negative effect on our digital lives.
- Over 80% of data breaches involve cracked or compromised passwords.
- 9 out of 10 users on the Internet worry their passwords will be hacked at some point.
- 44 million Microsoft users reuse the same password across various Microsoft accounts.
- Google reports that 65% of users use identical passwords across several sites.
- 10 minutes – that’s all it takes to break 6-character lowercase passwords.
- 2.5 hours for 8-character passwords
- Of 15 billion compromised passwords, over half had eight characters or less.
- Less than 50% of users in a Google survey stated they would change their passwords after a data breach. This is good news.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
How did they get my password?
Password robbers are an ingenious group. They use various methods, techniques, and strategies to get their victims’ passwords. They are also interested in login credentials (usernames, passwords, pins, etc.).
The bad guys steal your password through password cracking, dictionary attacks, and phishing
Password Cracking
Password cracking refers to the various methods used for discovering passwords. Password thieves steal passwords stored in or transported from a computer system. Hackers repeatedly guess the password until the password is discovered. They use a computer algorithm that tries all possible combinations.
The most malicious reason for stealing passwords is to hack computers. Cyber crooks intend to use them for fraudulent activities without the owners’ awareness.
Here are two techniques cyber criminals use to do password cracking:
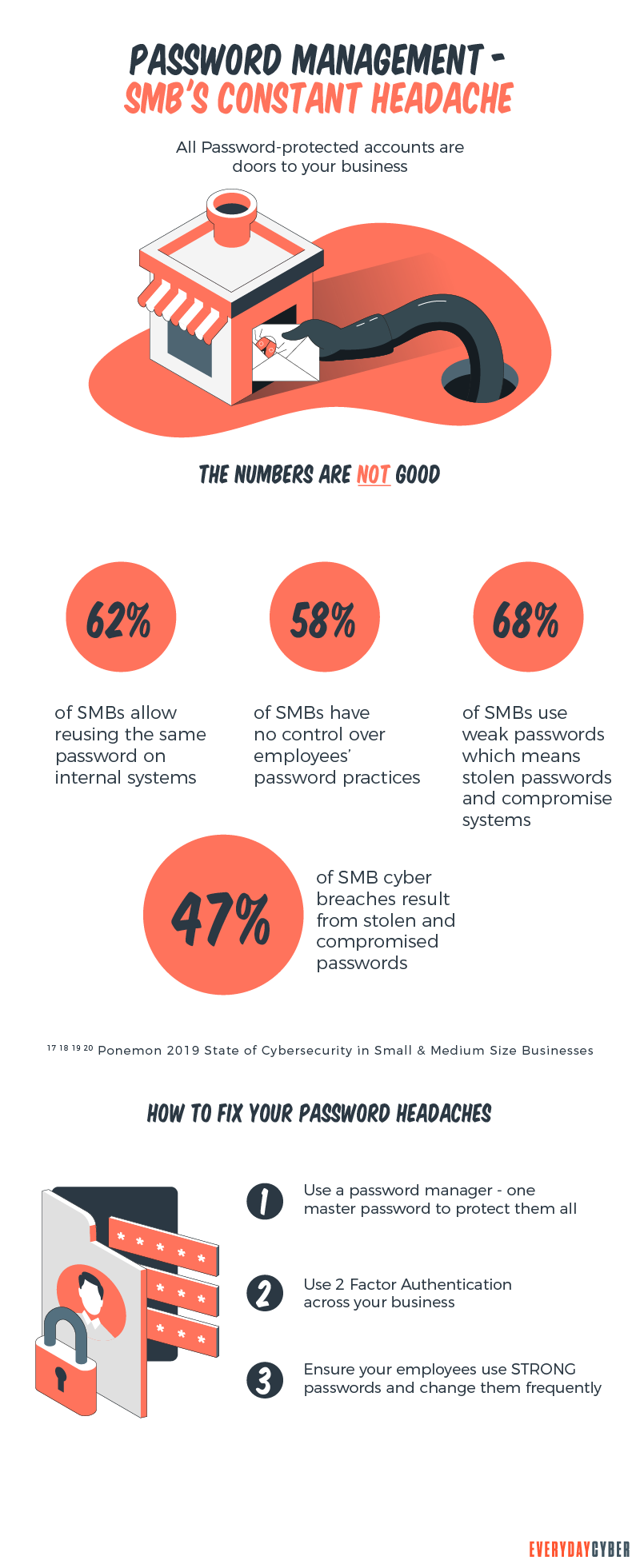
1. Brute force attack
A brute force attack uses excessively forceful attempts to break passwords. It uses the trial and error technique. Cyber criminals use powerful computers to test a wide range of password combinations.
Attackers try all possible combinations of characters until they guess the correct mix. They automate the process with clusters of computers to achieve their goal faster. Powerful computers can try 300 billion+ guesses a second. So passwords under 12 characters don’t stand much of a chance.
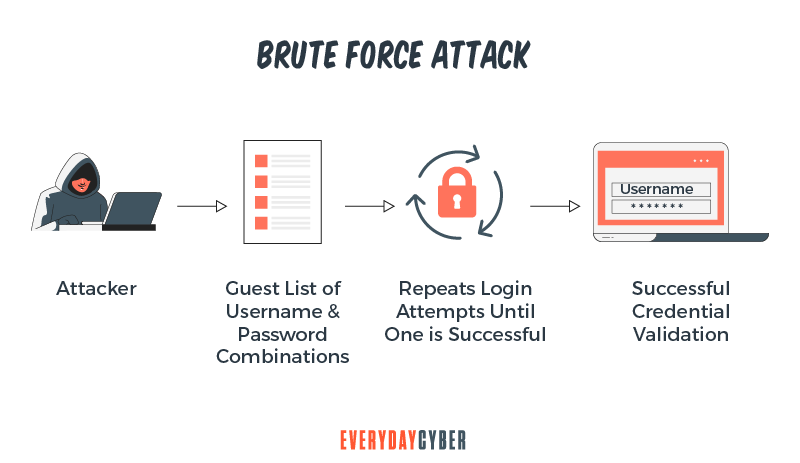
2. Dictionary attack
A dictionary attack is like what it sounds. Password crackers look for common words and phrases. They can also try to search for old passwords for future attacks.
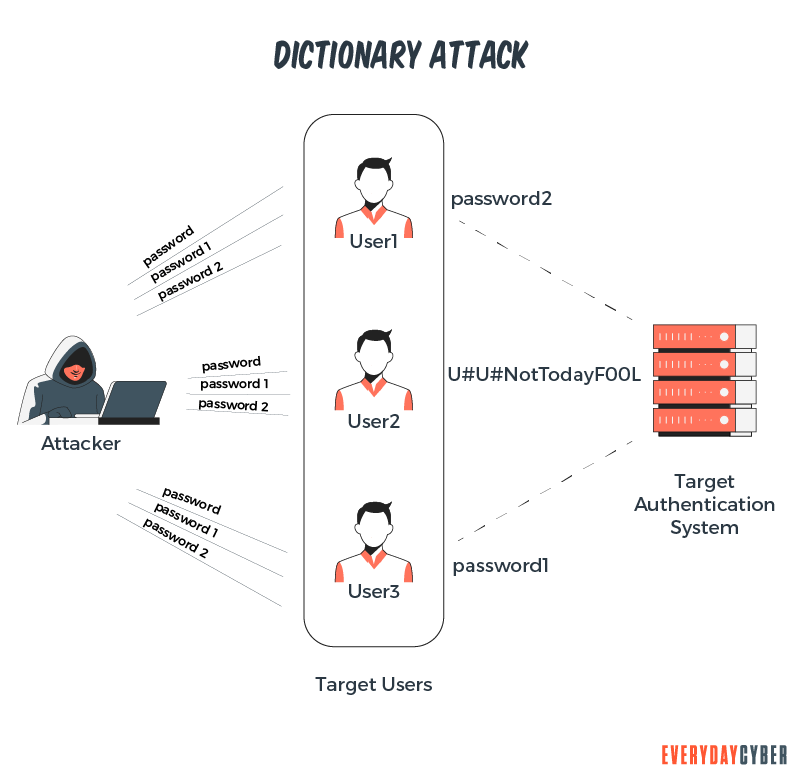
Phishing and social engineering
“Your bank account is locked, please change your password.” This is a common tricky message. It’s social engineering at its best. It uses fear, urgency, or threats to trick people into providing their passwords.
Phishing is also one of the most successful ways of stealing passwords. So it’s not surprising it occurs a ton. Phishing can occur through texts (smishing) and voice calls (vishing). But the most common is through emails.
Phishers use all types of emotional and stress-inducing methods. Their aim is to intimidate, convince and con you into taking actions you shouldn’t.
In many instances, they induce you to click a link that will take you to a fake site they have impersonated. While there, you’re asked to provide your password or other credentials. Once you do that, they will capture your credentials for future attacks.
Types of password hackers
There are three types of password burglars in password cyber crime. They are the password crackers, password sellers, and password users. A cyber criminal can be one, two, or all three of these types of hackers.
Password crackers
These are the bad actors that use various methods to break and steal passwords. They do their task with the methods we discussed earlier. They build inventories of stolen or hacked passwords and credentials. Then they sell them to password wholesalers.
Password wholesalers
These guys are the middlemen in password cyber crime. They create online markets on the dark web and act as a reseller to other cyber criminals. They buy stolen credentials by the boat load and sell them to the highest bidder. They create online dark web e-commerce sites to transact anonymous deals.
Password buyers
These criminals are the ones purchasing and using the stolen credentials. They could be individual bad actors or organized syndicates of cyber criminals. They greed for the worst passwords leaked to the online world to launch all kinds of cyber attacks.
These password criminals form the ecosystem for acquiring and using stolen credentials. It starts with the password crackers. They focus on stealing or cracking credentials, primarily passwords.
The password buyers next come into the picture. The easiest method to build a database of passwords and login credentials is to buy them. Then the password users use the stolen credentials to launch cyber attacks.
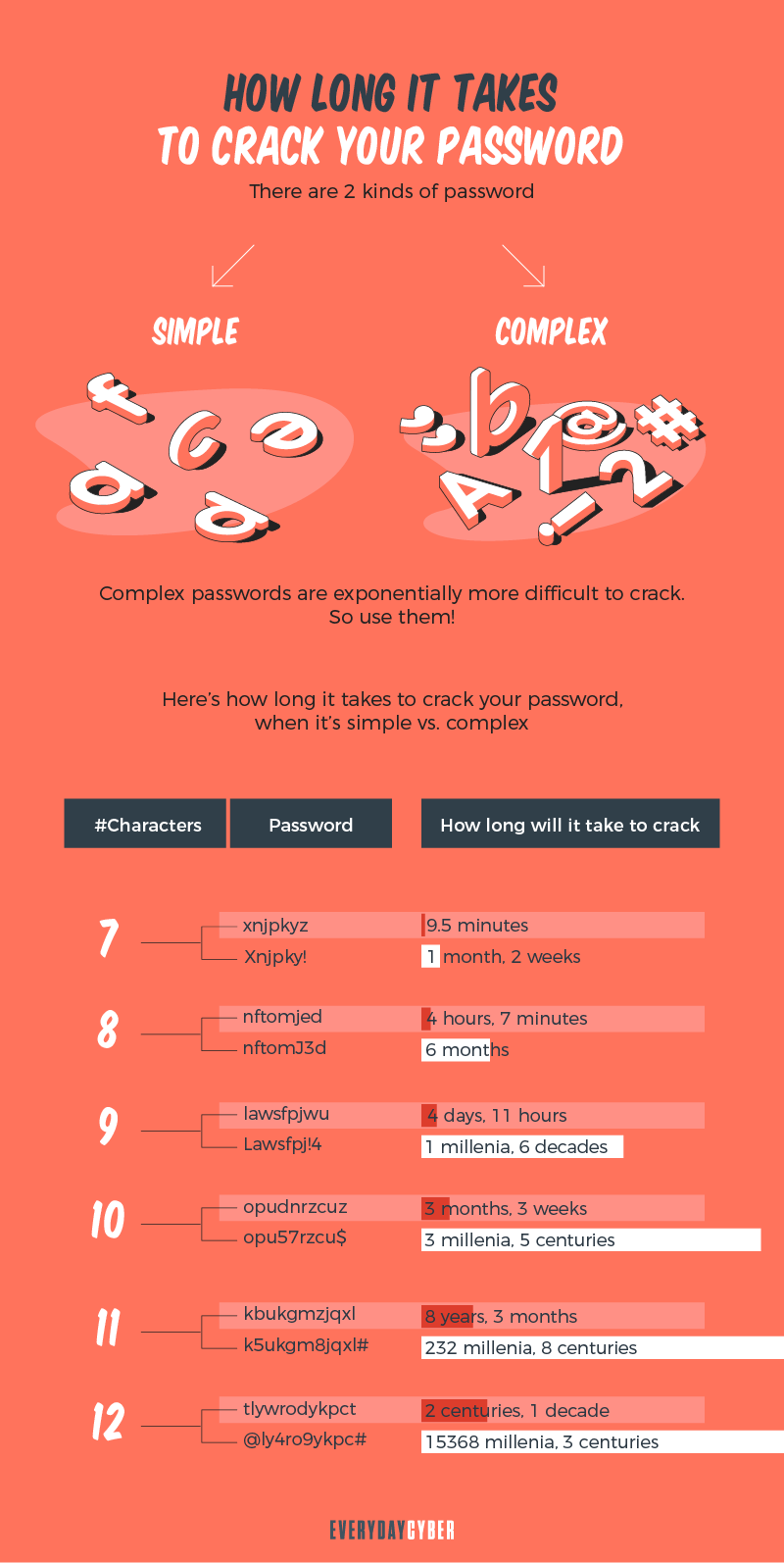
Weak passwords are bad, strong passwords are good, multi-factor protection is great
Lots of bad password practices are going around. Many users are failing at good password and login credential management. The exponential increase in cyber crime makes now, more than ever, the time to up your password game.
In today’s connected world, we all need digital accounts. We need them for the websites we visit, online services, email, and the list goes on. With so many accounts, managing login credentials becomes daunting.
We get lazy about our passwords. We use short, simple, and the most common passwords on multiple accounts. Cyber criminals love this because it makes their lives so much easier.
Remember the stats. It takes 10 minutes to hack a 6-character password. Within a couple of hours or less, criminals are able to crack an 8-character password. They use powerful computing power to breach even 12-character passwords. So make sure to create unique passwords with random alphanumeric and special characters.
How to achieve password security
We have a battle on our hands, but there are ways to defend ourselves. Here are the top six steps you should take for better password
1. Make your passwords 17 characters or longer
Longer passwords are much harder for cyber criminals to guess. Cyber crackers use clusters of computers for more speedy cracking. So if your passwords are short, they’re in for easy cracking.
2. Use random letters, numbers, special characters, or words
Common passwords are easy to break. Hackers are great at spotting and recognizing patterns, so avoid using them. Use a combination of random lowercase and uppercase letters, numbers, and special characters.
3. Consider using passphrases instead of passwords
Passphrases are a collection of common words combined randomly in a memorable phrase. A 7-word passphrase would take one (1) octillion (1+27 zeros) attempts to break.
4. Do not reuse passwords
Cyber criminals love users who recycle or reuse passwords on multiple sites. Once they crack one of your passwords, they can use this on all your accounts. Once one account is cracked, all of your accounts are cracked. So never ever give in to password reuse.
5. Always use multi-factor authentication (MFA) if it is available
Two-factor authentication (2FA) is currently the most popular. A Microsoft study found that enabling
6. Use a password manager
A
Our final thoughts. Strong, unique, and complex passwords make your accounts secure. Remember the worst passwords give you the worst digital nightmares
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
7 ways to secure your home office
People working from home perform most of their tasks online. They are now more exposed to cyber attacks than ever before. Cyber criminals see a great opportunity in the massive growth in working from home and the vulnerabilities of home office security.
What is Pharming?
Pharming is cybercriminals “slight of hand” cyber attack. Redirecting you to a fake website imitating a legitimate site so they can steal your login info, financial data, and more.
Why should you use a Password Manager?
How many passwords do you have? Did you know the average Internet user has 100 passwords. That's a lot of passwords to remember on a daily basis. How do manage all those password effectively - a password manager.
Why every small and medium business needs a cybersecurity strategy
A truck full of security studies show nearly every small businesses has exposed data and poor cybersecurity policies. Either build and execute a cybersecurity strategy or expect to be a victim of cyber crime. Be prepared, be proactive, and be safe.
Piggybacking in Plain English: 6 Ways to Keep Your Neighbors from Stealing Your Wi-Fi
Stopping piggybacking all boils down to vigilance and protecting your Wi-Fi with a good VPN, antivirus software, firewall, and security patches.
What is Digital Identity?
Your digital identity is your set of unique features and characteristics identifiable to you. It is all data that can be traced back to you.

