Wi-Fi changed how we communicate. And then came the smartphones and other intelligent devices. You shouldn’t worry too much about your neighbors using your Wi-Fi because the Internet is now so ubiquitous. They most likely have their own Wi-Fi or 4G on their phones as well so they don’t need to search for free internet access.
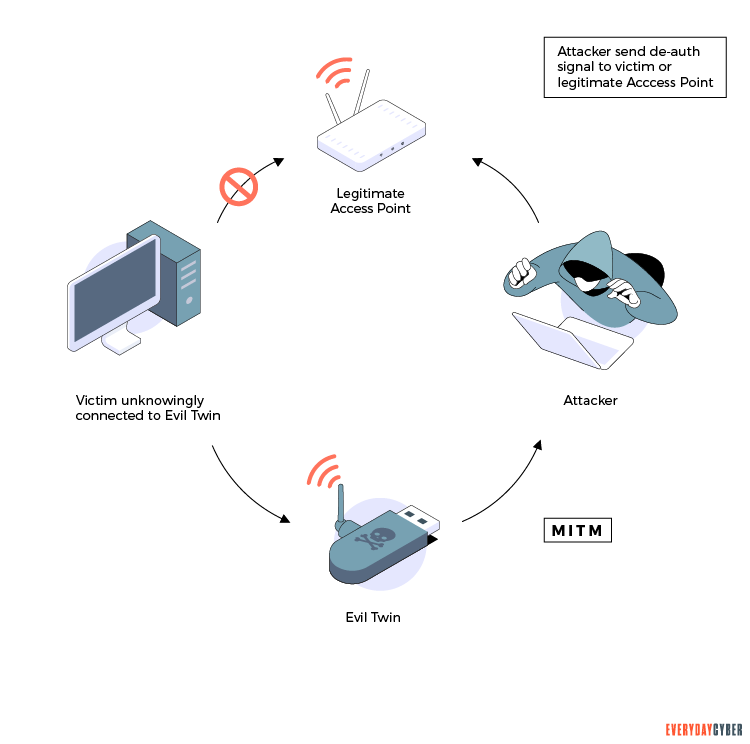
Still stealing Wi-Fi access still happens. It’s call piggybacking. Often criminals park outside private homes, hack into your wi-fi network and starting using your internet connection. Often consuming most of your your bandwidth. Worse, they might eavesdrop on you or download illegal files on your network.
So What is Wi-Fi Piggybacking?
Wi-Fi piggybacking is using a nearby neighbor’s or other unprotected Wi-Fi as their own personal hotspot. Wireless routers coming straight from manufacturers are typically unlocked with out even a default password. Inexperienced users, many homeowners for example, often leave their routers unprotected by not setting a password or not changing the default password. If you live in multi-family housing, such as apartment complexes or townhouses, often the wi-fi is open. Cybercriminals know this and steal the facilities Wi-Fi bandwidth and use it to hack into each individuals devices.
A rainbow Wi-Fi icon may appear when you open your
When the padlock icon is missing, this means the network is open and access isn’t protected. This means you can access it to check your email, get into social media, or stream videos without having to enter a password and so can the bad guys.
It is important to know that, that piggybacking or using another person’s wireless network without that person’s permission is prohibited in many US states and other jurisdictions. So be careful which networks you connect to.
Cases in point
Research done by Sophos showed that more than a majority of computer users admitted to have engaged in Wi-Fi piggybacking. While this this study was conducted in the 2010’s, it is clear that with the rise in global Internet user. which is estimated to be 4.95 billion in 2022, the frequency and commonality of piggybacking has increased comparatively .
According to the Sophos study, many Internet-enabled homes neglect to adequately safeguard their wireless connection with passwords and encryption. This allows neighbors and freeloaders passing by to steal Internet access instead of paying an Internet Service Provider (ISP) for their own.
While piggybacking may be a victimless crime, some states have adopted their own laws to protect Wi-Fi owners and ISPs. Take the cases of the following piggybacking offenders:
- 2007 – A Michigan man was arrested for using a cafe’s free Wi-Fi from his car.
- 2007 – An Alaskan guy was detained for playing video games from his parked automobile while accessing the public library’s Wi-Fi network after hours.
- 2006 – An Illinois man was taken into custody for using an unsecured Wi-Fi network from his car.
- 2006 – A man from Washington was also detained for parking in front of a coffee shop and accessing the free Wi-Fi without making a purchase.
- 2005 – A Florida man was charged with a third-degree felony for surfing an open Wi-Fi network from his SUV.
Why Piggybacking is Unwelcome
The ethics of Wi-Fi piggybacking is a sticky issue, but certainly, no piggybacker is welcome. Some might treat piggybacking as a harmless act, but owners paying for their plan are quick to disagree.
First, piggybacking can lead to increased financial costs for paying Wi-Fi users. The cost of Internet connection differs from state to state, and from country to country. The cost covers bandwidth use, equipment rentals, and installation. The price tag for bandwidth use depends on the cap applied for. ISPs may need to impose additional charges on clients who go beyond their cap as a result of piggybacking.
Second, Wi-Fi piggybacking culprits hijack a substantial portion of your bandwidth. This leaves less for your own gadgets, causing speed slowdowns.
Third, Wi-Fi freeloaders might use your internet connection for criminal purposes. Piggybacking can be used by some to hide their illegal activities like downloading child pornography. They can also infect your network with malware to steal your
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
How to Detect if Someone’s Stealing Your Wi-Fi
Check the settings pages for your wireless network to see if someone is stealing your Wi-Fi. You can keep track of all the equipment connected to your network by checking the list of individual IP addresses and media access control (MAC) addresses.
Devices also broadcast an ID because they have been given names by their owners, such as “Jane’s iPhone”. So if you discover one device that’s connected but is unfamiliar, someone may be stealing your Wi-Fi.
You can also count the number of connected gadgets and compare them to the number of devices you know should be there to determine if they match.
Another practical detection technique is to turn off all the Wi-Fi connected devices in your home or small office. Then watch the signal light on your router. If the light keeps flickering, then someone else is using your Wi-Fi connection.
If you want a more in-depth method to check if someone is stealing your Wi-Fi, use an app that automatically searches for unrecognizable devices connected to your Wi-Fi network. Do this during odd times of the day or when no friends are over. Some examples are:
How to Stop Wi-Fi Piggybacking
(Image idea source: https://atlasvpn.com/blog/how-to-stop-wi-fi-piggybacking)
You really do want to stop W-Fi piggybacking from happening on your network. After all, you’re paying the bill. Here are 6 tips you can use to protect your network from Wi-Fi leachers:
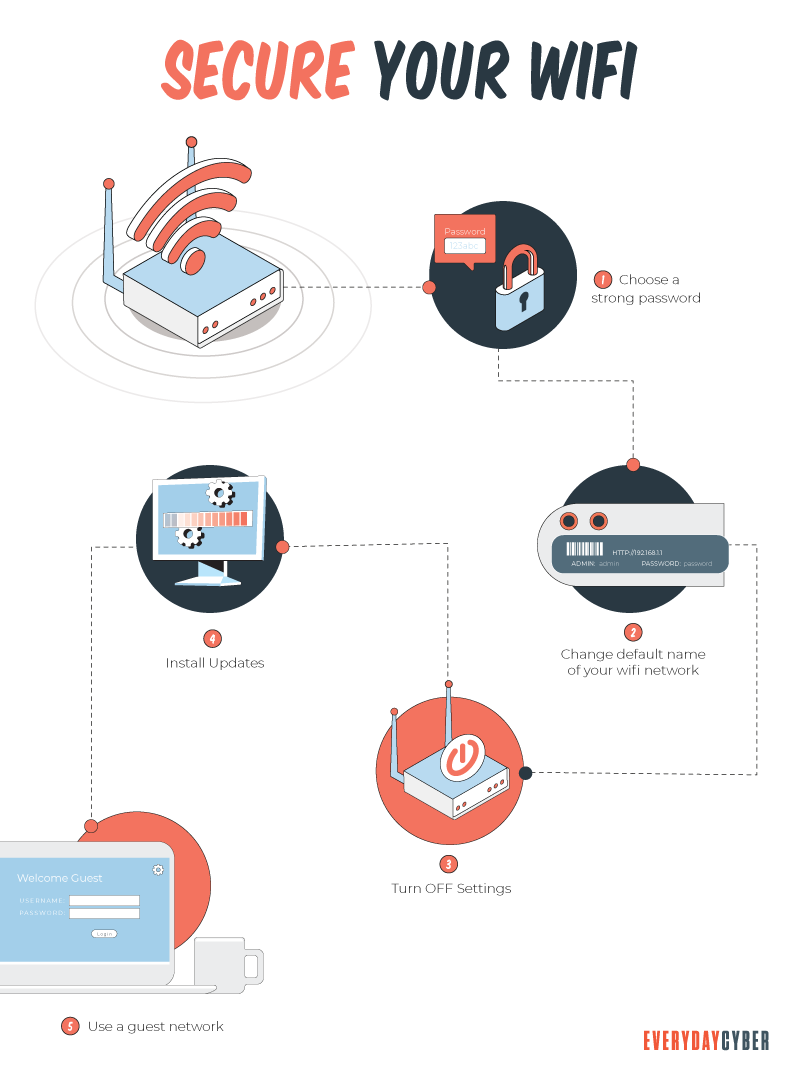
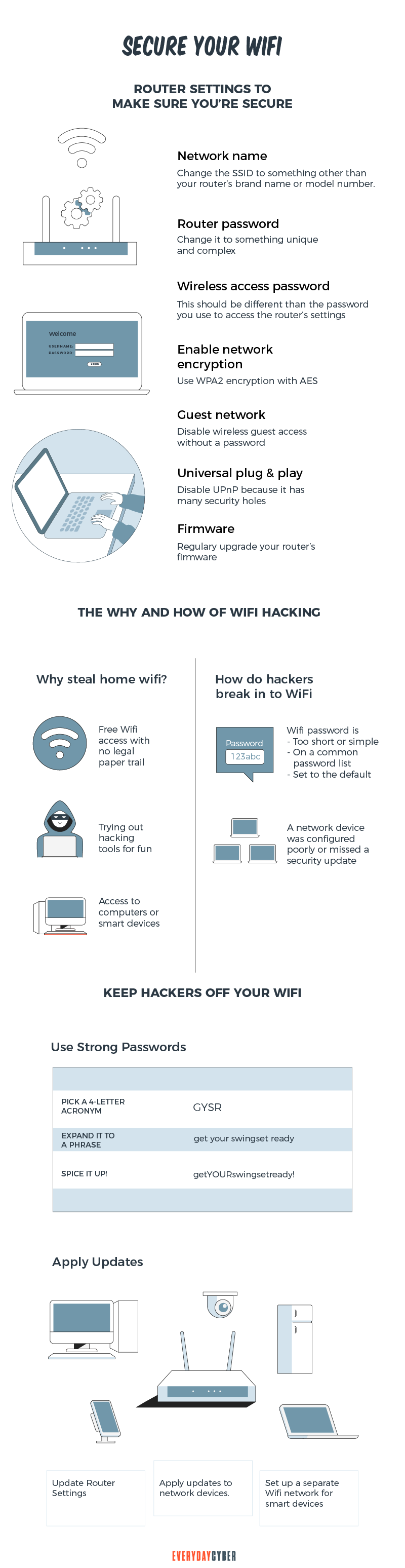
1. Change your Wi-Fi password
Network devices typically come with a default password that is easy to figure out. Many hackers have a database of all manufactures default passwords. This is the first thing they try. So create a strong Wi-Fi password, use both uppercase and lowercase letters, special characters, and digits. Make it a minimum of 12 characters, preferably 20. It’s also recommended that you change your password regularly. You can accomplish this task with the aid of a
2. Give a name to your router
The name of your router is the service set identifier (SSID). Change it to something unique, but set it it to NOT be BROADCAST. If you set the SSID to not be broadcast your network won’t appear in the lists of connectable networks. While someone with technical know-how can monitor concealed networks, masking your SSID is a good method to eliminate average piggybackers and will deter even cyber criminals.
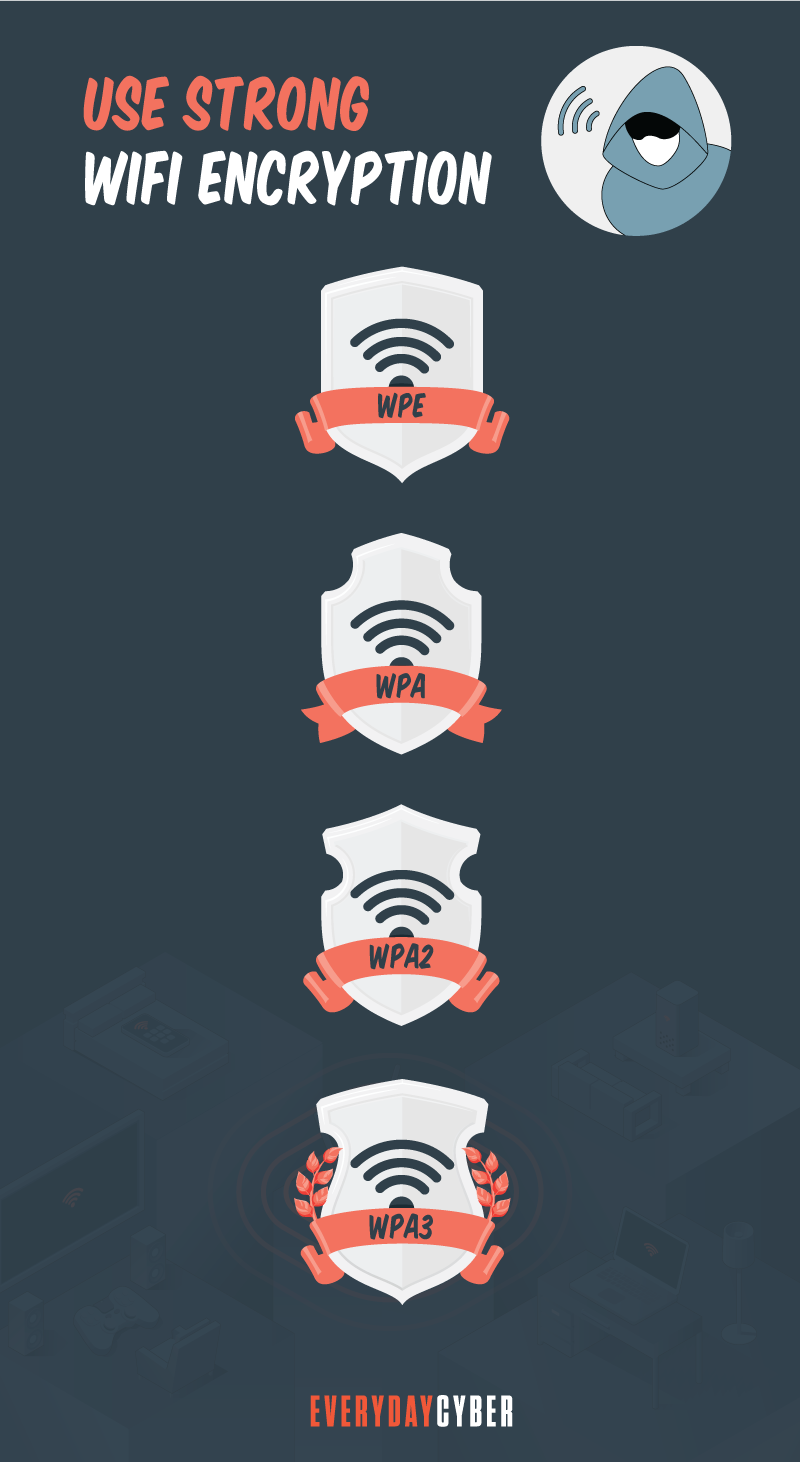
3. Use encryption
A Wi-Fi Protected Access 2 (WPA2)-compliant encryption protocol is the most basic component of wireless
4. Implement MAC address filtering
Configure your router to only allow specific devices to be able to access your network. You can do this by configuring your router to only allow devices whose MAC address has been added to the MAC filtering list. This option works because you whitelist the MAC address of each device.
While this method is very effective, it is not 100% fool proof because MAC addresses can be spoofed. This means that some sophisticated hackers might hide behind addresses you have already authorized but it will deter most amateur piggybackers.
5. Limit the number of connecting devices
Set a limit on the number of many devices you will allows on your Wi-Fi network at any one time. Identify the typical maximum number of connections you would expect on your network at any one time and set the limit accordingly.
6. Restrict Internet access to specific hours
Some wireless routers allow you to set Internet access to specific times of the day. For instance, you can turn off your router from 9-5 during work days when no one is expected to be left at home or over night when it would be unlikely that your devices would need access to the internet.
Our Final Thoughts
Stopping piggybacking all boils down to vigilance. Not every internet usage calls for a large amount of bandwidth. It can be challenging to spot anything unusual if a person is not downloading gigabytes of data every day. For this reason, you need a monitoring tool that automatically verifies all the logged-in devices.
Finally, protect your network with a
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is Hacking?
Hacking is an old game in the cyberworld with ever changing players and techniques. It may be done with good intentions or malicious motives. It is growing rapidly because of the proliferation of devices.
7 ways to secure your home office
People working from home perform most of their tasks online. They are now more exposed to cyber attacks than ever before. Cyber criminals see a great opportunity in the massive growth in working from home and the vulnerabilities of home office security.
What is Adware?
Adware, known as advertising supported software, makes money by displaying ads - popups, inline, banner. ANNOYING!!, but typically used to support free software.
Element Chat Review: How Secure Is It, Really?
Element is a secure messaging app for safer personal and corporate communication and other group chats.
What is HTTPS?
HTTPs enables web servers and web browsers to establish secure connections. It encrypts data being transmitted in both directions. This helps prevent thieves from stealing sensitive information along the way.
Strong Passwords. One giant step to protect our digital lives
Here's how to create long, complex, and unique passwords to protect your accounts and keep your sensitive info safe from hackers.


