The WannaCry epidemic in 2017 marked the beginning of the modern ransomware mania. This widespread and well reported cyber strike proved that ransomware attacks are both feasible and potentially lucrative. Many ransomware variations have since been created and used in several malware attacks.
The Covid-19 crisis greatly influenced the recent rise in ransomware. When organizations quickly shifted to remote work in response to the pandemic, gaps in their cyber defenses emerged. Threat actors saw these vulnerabilities as opportunities to spread large-scale ransomware attacks.
How Pervasive is Ransomware?
To understand how widespread ransomware is, let’s take a look at some of the shocking findings of the 2020 Check Point Research:
- Q3 2020 saw a 50% increase in the daily average of ransomware attacks
- US, India, Sri Lanka, Russia, and Turkey were the most affected by ransomware attacks in Q3.
- Maze and Ryuk were the two most popular ransomware variants in Q3.
- Ryuk ransomware now targets 20 businesses per week.
The year 2020 saw a massive wave of ransomware attacks. Ransomware has proven to be a profitable attack strategy for cybercriminals, claiming a new victim every 10 seconds.
As if the situation isn’t bad enough, ransomware operators have begun integrating double extortion into their ransomware strategy. This has become a pattern since Q1 2020. Before encrypting their victim’s databases, ransomware attackers remove large amounts of sensitive information and threaten to make this information public if their ransom demands are not met.
Some organizations prefer to pay the ransom to avoid having their sensitive data exposed. Recent ransomware attacks on health facilities have put patients’ lives in peril by using the pandemic as leverage to force hospitals and medical research institutions to pay the demanded ransom.
How the Ryuk Rasomware Emerged
Since August 2018, Ryuk has been among the most dangerous, destructive, and dreaded malware in use. Ryuk mostly targets medium to large as well as enterprise corporations to extort millions in ransoms.
According to experts, Ryuk is run by GRIM SPIDER, an apparent cell of the hacker group Wizard Spider gang. Others in the field of cybersecurity believe Ryuk is linked to the Lazarus Group of the North Korean Advanced Persistent Threat (APT). This cybercrime organization is also linked to the Hermes ransomware which in turn is linked to Wizard Spider.
During the Covid-19 epidemic in 2020, Ryuk became increasingly well-known and began targeting healthcare facilities.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
How the Ryuk Ransomware Operates
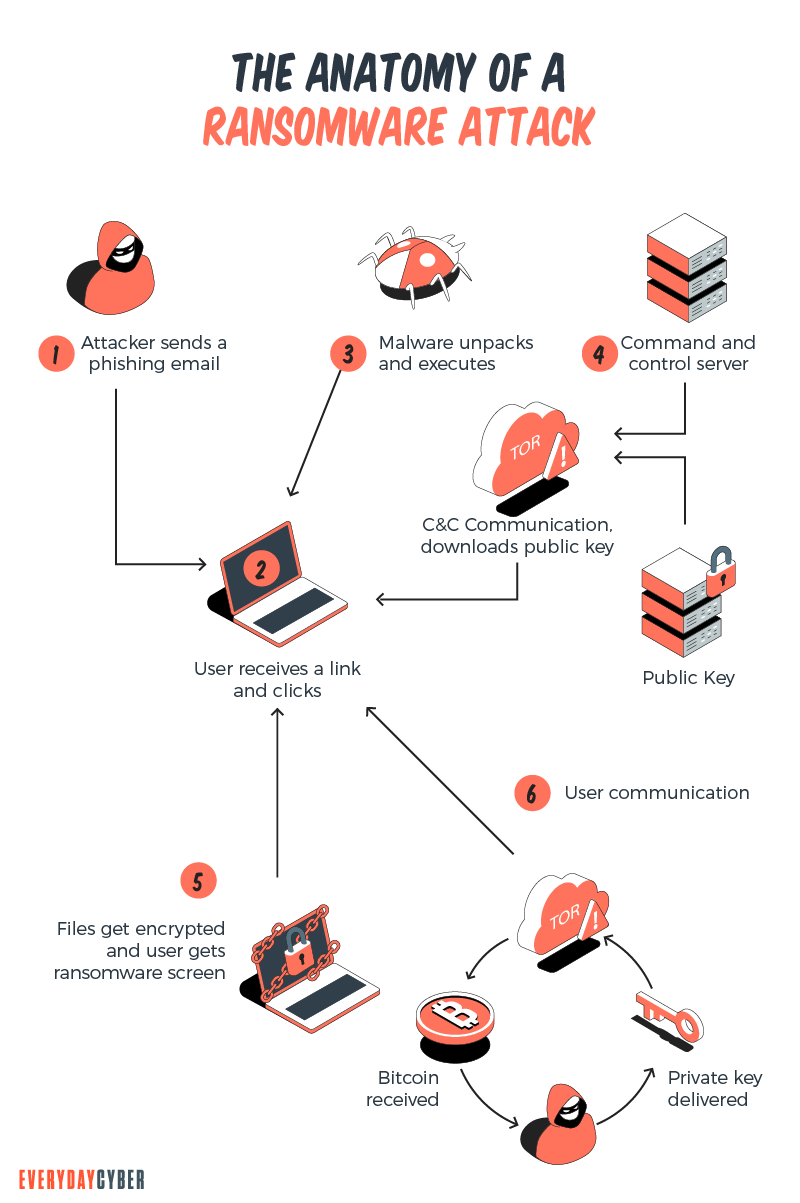
Ryuk criminals use a multi-stage technique to launch targeted attacks. The campaign typically starts with common attack vectors, such as phishing emails, dubious URLs, deceptive links, or Remote Desktop Services.
Emotet bot
An Emotet bot will automatically be downloaded and infect the computer when an unsuspecting user responds to a phishing email, clicks on the embedded malicious link, or accesses a poisoned website.
Trickbot
The second infection, known as Trickbot, is installed into the compromised system once the Emotet bot has gained access to the system. The Trickbot gives the cyber crooks complete network insight. The criminals may undertake a thorough mapping and identification of critical assets. They can now determine the value of the target.
What the criminals are looking for are large and high-profile companies capable of paying ransom. Attackers execute Ryuk ransomware to corrupt as many endpoints and servers as possible, by encrypting both the network drives and network shared folders, including their backups.
After encrypting all the files in the attack chain, Ryuk will send a ransom note in every folder. A typical Ryuk ransom demand requires payment in cryptocurrency in amounts of 15-50 Bitcoins, which is equivalent to $100,000-$500,000, according to Coveware.
Anti-recovery tools
Ryuk operators use sophisticated methods to delete backups and install anti-recovery tools. This is the reason why victims generally fail in their recovery of encrypted files, unless offline or external backups have been created.
How Big a Threat is the Ryuk Ransomware?
A new Ryuk variant discovered in 2021 is fanning fear among cyber
By replicating and executing at an uncontrollable scale, the Ryuk ransomware infects entire networks or completely takes over systems or infrastructure.
Experts from the National Agency for the
The big danger here lies in the new Ryuk’s ability to replicate and spread itself across a network. As such, it has the potential to more extensively infect an organization or network in a shorter amount of time.
Ryuk criminals can increase the ransom demands as a result of more sensitive information being encrypted before it is discovered and used. As the preferred target of this ransomware, those in the healthcare industry should be on high alert.
Indications of Compromise (IOC) by a Ryuk Malware
The following screenshot is often the first IOC of Ryuk. This indicates that Ryuk has infected the company network and has begun to encrypt files. Recovery is significantly quicker if the company is prepared with effective incident response teams, ransomware strategy, and offline data backups.
Detecting Ryuk infections may not be easy for the ordinary user because the process is quite technical. It’s the
Ryuk frequently enters through a dropper called BazarLoader. Malware that downloads additional malware is known as a dropper, or DaaS. Here are some BazarLoader IOCs to observe:
- The Windows registry shows a scheduled operation called “StartAd-Ad” followed by autorun entries.
- Dual-extension executable files, such as Report.DOC.exe
Trickbot’s IOC is an executable file with a file name consisting of 12 randomly generated characters. For example, mnfjdieks.exe would be in one of these directories once TrickBot creates the file:
- C:\Windows\
- C:\Windows\SysWOW64
- C:\Users\[Username]\AppData\Roaming
Please refer to the US Cybersecurity and Infrastructure
High-Profile Ryuk Ransomware Attacks
Attacks using the Ryuk ransomware have a pattern. Ryuk criminals target large government and private entities in a raid-like manner. Many targets in the US, UK, Germany, Spain, France, and Australia have been the subject of Ryuk ransomware attacks. Here are some of them:
Liege Ryuk ransomware
In June 2021, Belgium’s third-largest city, Liege experienced a Ryuk ransomware attack on its IT infrastructure. It caused delays in administrative procedures including the processing of passports, identification cards, and marriage, birth, and residency permits.
Baltimore County Public School Ryuk ransomware intrusion
In November 2020, Ryuk attackers hit the public school system, messing up their remote education services. The school serves more than 115,000 students with a $1.5 billion budget. No ransom was paid, but the school spent nearly $10 million for recovery.
Universal Health Services (UHS) Ryuk ransomware assault
In September 2020, more than 250 medical facilities of UHS were attacked. UHS is one of the major private healthcare organizations in the US. The infected system forced patients to be transferred to other emergency rooms and delayed medical test results and appointments. UHS reportedly spent $67 million on recovery after the attack.
Epiq Global Ryuk ransomware strike
In March 2020, a Ryuk attack on 80 offices of the law firm Epiq Global worldwide prevented clients from accessing crucial legal documents. It’s not known if the company made ransom payments.
New Orleans Ryuk Ransomware
In December 2019, Ryuk ransomware attacked the New Orleans network through a phishing email. The city had to declare a state of emergency as a result of the virus attack, which affected more than 450 servers and 3500 laptops. The city spent $3 million in mitigation and recovery expenses which was covered by the city’s cyber insurance policy.
Tribune Publishing Ryuk ransomware siege
In December 2018, the delivery of the LA Times and Tribune newspapers across the US was hampered after Tribune Publishing came under attack from the Ryuk malware. IT specialists were able to locate the problem and restore servers, but the virus soon began to re-infect the network after bypassing their
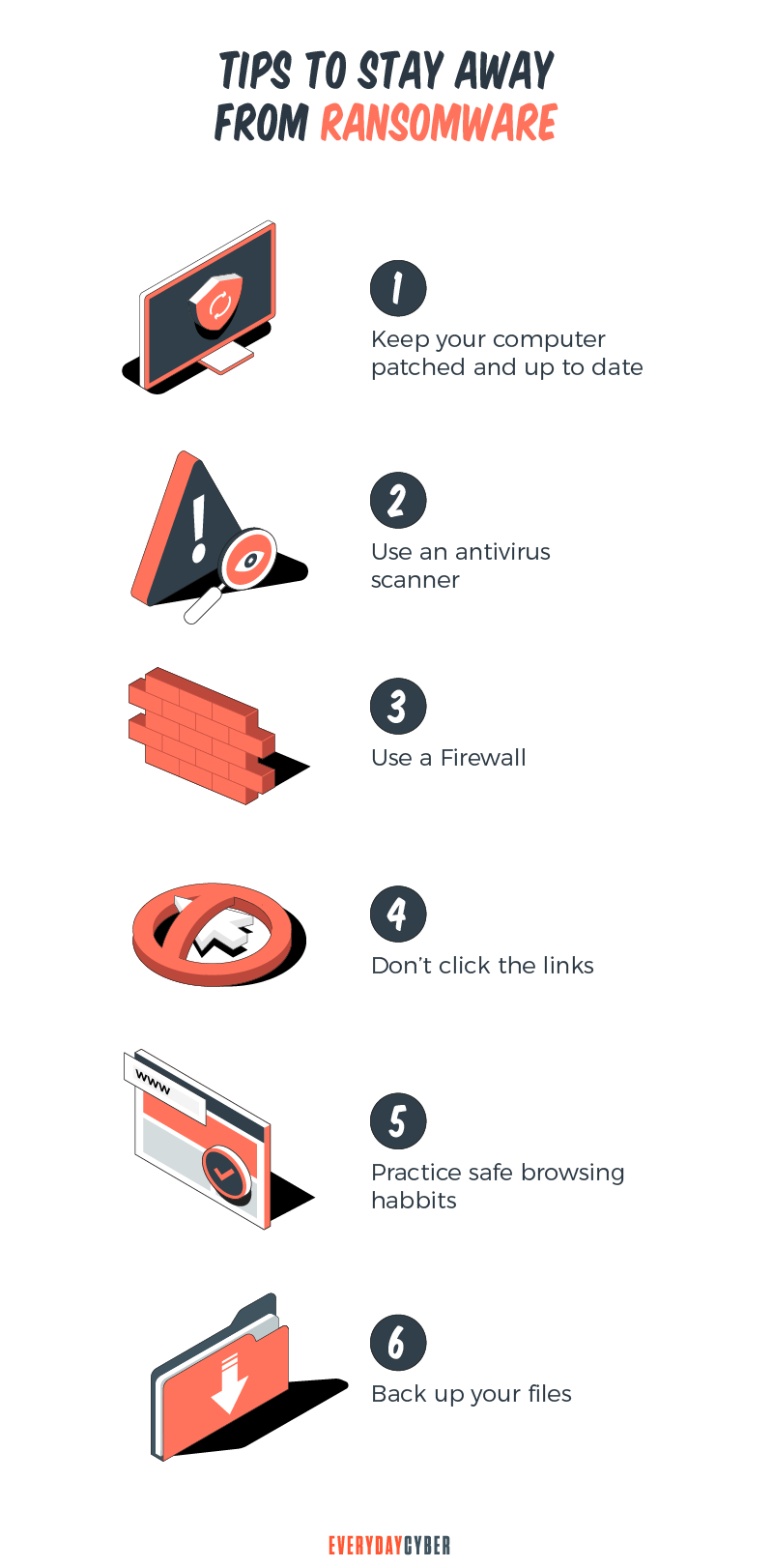
How to Stop a Ryuk Ransomware Attack
Just like most ransomware, Ryuk typically finds its way through networks because of inadequate IT practices, such as a lack of staff training, weak passwords, ineffective firewalls, responding to phishing emails or flimsy
The greatest defenses against ransomware attacks include fixing these problems, putting backups in place, managing permissions-level access, and deploying server
Human error cannot be avoided. An entire system can go down with only one mistake, such as opening an infected document or clicking on a malicious link. However, good digital hygiene and a ransomware prevention tool can thwart the Ryuk malware before it infects the entire network and shuts down vital services.
In other words, let’s go back to the basics:
- Authenticate users
- Use strong passwords and secure password management
- Enable multi factor authentication
- Implement redundant backup plans
- Keep your systems and IoT devices updated
- Do automated scans regularly
- Limit macro usage
- Educate and train your staff
- Have a ransomware detection strategy in place
Our final thoughts. The fallout from a Ryuk ransomware attack is not only painful. It’s devastating and no organization is immune. This is why IT administrators should take proactive steps to stop Ryuk from wreaking havoc to their systems, or at least limit damage. The best protection is prevention.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is a Password Manager?
A password manager is an encrypted storage system for keeping and managing passwords usually protected by a master password. Some password managers use biometric data to protect the vaults instead of master passwords. Still others support the use of two factor authentication for higher security.
What is a Remote Access Trojan (RAT)?
A remote access Trojan is a software used by hackers to gain unauthorized access and remote control on a user’s computer or mobile device, including mouse and keyboard manipulation.
10 Cybersecurity Trends for Small Businesses in 2022
Knowing the latest cybersecurity trends spells the difference between keeping your business safe and opening it up to cyber attackers.
SMBs 7 Deadly Cybersecurity Sins
How many of these seven deadly cybersecurity sins are you guilty of? Build a resilient cybersecurity strategy before it’s too late.
What is a Botnet and How to Protect Your Business from One?
A botnet is a network of computers that work as a collective to infiltrate your device. Here's how to protect your business from botnets.
What is Smishing?
Smishing is a texting scam. Texts appear to come from reputable companies inducing you to reveal personal information, such as passwords or credit card numbers.


