Did you leave the door open?
Bet you have had that “oh no” feeling once or twice in your life where you left for work or school or just to go visit a friend and you have this awful feeling in the back of your mind – “did I leave the door unlocked”. For most of us that is both a scary and stressful thought because it encourages even more worrisome thoughts about someone getting into our home and taking things, violating our private space and who knows what else.
There is a similar parallel in the digital world – something the cyber community refers to as a back door threat and they can be just as stressful and potentially just as life-affecting as they can be in the physical world.
What is a Back Door Threat?
A back door threat is a particular type of malware (malicious software) attack that bypass a device’s
With a backdoor opened, remote access to your device is enabled and the hackers are able to get onto your device whenever they want to. They can then access the device’s resources, such as files, control the camera and microphone, steal data, issue system commands and install additional malware.
Small and midsize businesses are particularly vulnerable for backdoor attacks because they tend to have fewer resources to close off entry points or identify successful attacks. Cybercriminals know that SMBs often lack the budget or
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
How is a Back Door threat created?
A back door threat in software, systems or devices can come in various forms and while there are many examples of backdoors being exploited for malicious activities, there are cases where backdoors do exist for non-malicious activities.
Non-malicious Backdoors
Software developers sometimes deliberately code backdoors into their applications as a legitimate point of access for remote administration, diagnostics, troubleshooting, or system tests.
These intentional backdoors can improve performance, make user experience better and are required by some software vendors. Unfortunately, they can also be exploited by hackers to gain unauthorized access. Hackers often look for administrator backdoors and those known only to the software vendors to break into systems.
Backdoors are not always evil, but they do add another layer of vulnerability that hackers can exploit to gain access to a device or system.
Malicious Backdoors
Hackers can also install their own backdoors into targeted systems with the help of a remote access Trojan, or RAT. A RAT is a piece of malware code that includes a backdoor for administrative control on a specific device.
RATs make their way into the system by tricking the user into downloading them through social engineering and disguising them as legitimate files. RATs can be masquerading as an email attachment sent by a co-worker, a social media link on a friend’s profile, or a free app to download. Once a RAT is installed, hackers can use the backdoor anytime they please to mess with your device or system.
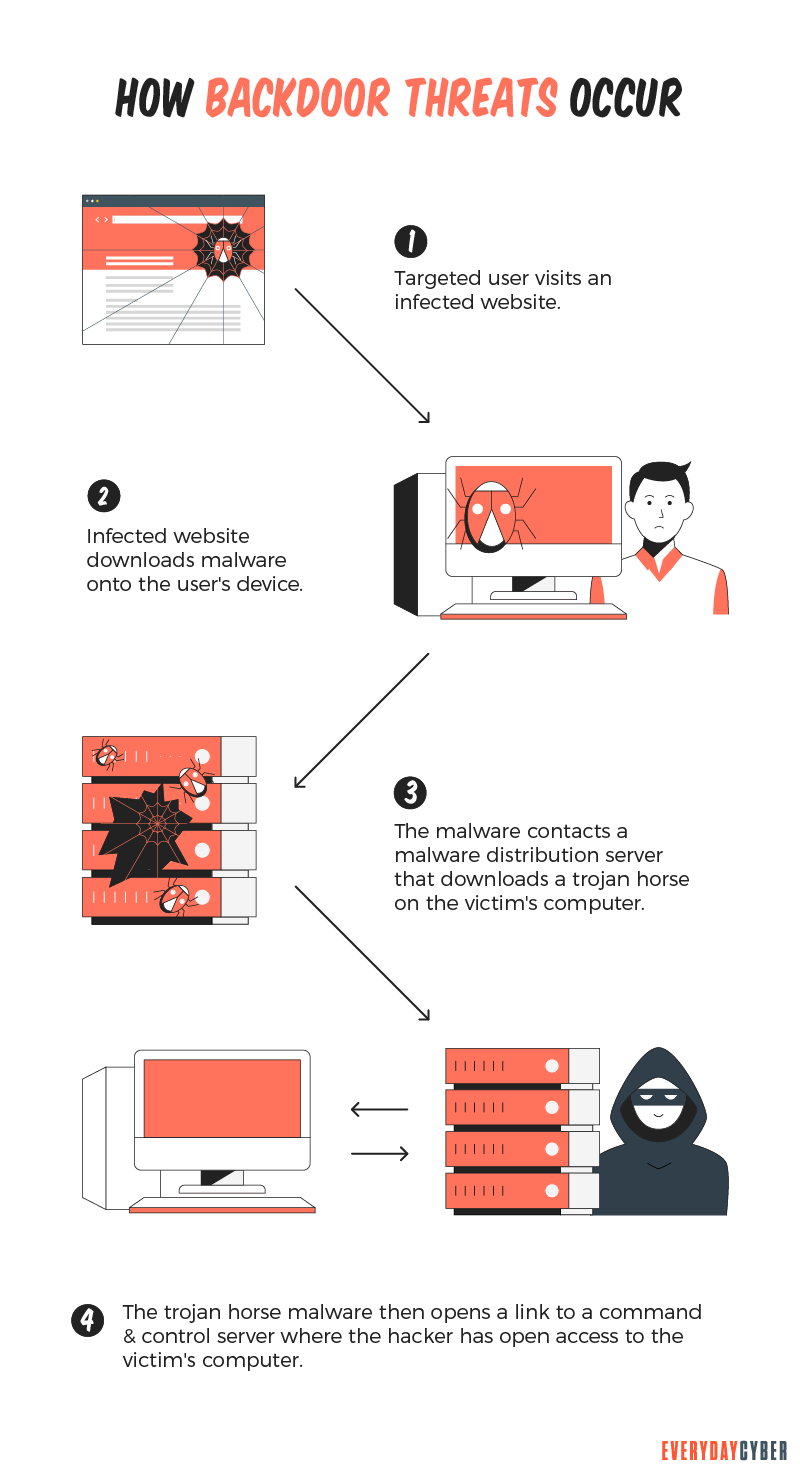
What makes Backdoors so dangerous?
Whether a backdoor is intended to be non-malicious or it results from unintended flaws in websites, operating systems or apps the
What happens when hackers gains access via backdoors?
- Install even worse malware on to your device
- Control the device remotely
- Steal confidential data
- Download additional files
- Download or upload files
- Run unwanted tasks and processes
- Perform DDoS attacks on other devices across the internet
- Change device settings, including passwords and user credentials
- Shut down, restart, or even “brick” your device
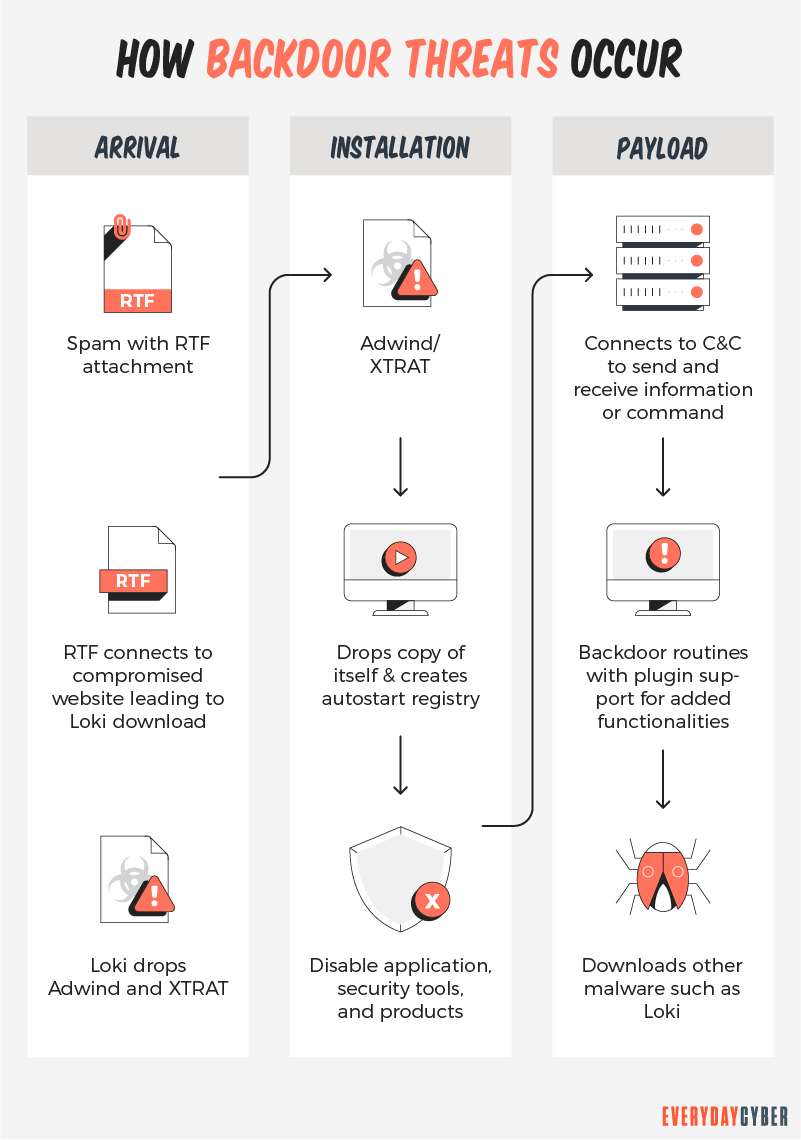
How to protect against Backdoors?
Unfortunately, backdoor attacks are extremely difficult to detect. Many users are unaware that backdoors exist on their device or in their systems. In fact, it may be an extended period of time (weeks, months, or even years) before the bad actors initiate an actual attack through the backdoor.
But there are strategies you can use to reduce the risk of a breach.
Empower your devices/systems with quality Antivirus /AntiMalware tools
Advanced
Use a Firewall and Network Monitoring tool
Use an antivirus/antimalware solution that includes a firewall and network monitoring as a part of the
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is a Hacker?
A hacker is someone who challenges technology to see if it can be compromised. A hacker can black hat or white hat.
A Step-by-Step Process for Creating an SMB Cybersecurity Plan
Failing to plan is a plan to fail. The vulnerability of your small business's digital infrastructure is dramatically increased without a sound cyber security plan. Business plans help achieve desirable outcomes. You don't want to be a cyber attack victim, so build a plan.
Why every small and medium business needs a cybersecurity strategy
A truck full of security studies show nearly every small businesses has exposed data and poor cybersecurity policies. Either build and execute a cybersecurity strategy or expect to be a victim of cyber crime. Be prepared, be proactive, and be safe.
What is a VPN?
A VPN is a virtual private connection to a VPN host server to hide your identity, address and online activity when using a public Internet connection. It does this by encrypting your data and turning them into “rubbish” so no one can make sense of it even if they get their hands on it.
What is Shoulder Surfing?
Shoulder surfing is a form of social engineering that enables cybercriminals to gather information just by looking over their victims’ shoulders. The aim of shoulder surfing is to obtain personal data, such as usernames, passwords or personal identification numbers (PINs), bank account numbers or credit card numbers.
What is 256 Bit Encryption?
256 bit encryption has quickly become the industry standard for ensuring security of your data, security of your communication and is really now minimum encryption level for securing your digital environment.


