The days of having to click on something to get infected with malware are long gone. Now just going to a website can result in your device getting infected.

Cybercriminals, bad actors, black hat hackers—whatever term you want to use—are nasty folks. But they are sophisticated, cunning, and innovative. And they’re constantly finding new ways to cause chaos, scam us, and get into our devices and our digital lives. Drive by downloads is just one of many techniques they use. It is one that many folks like you and me could get burned with if we’re not careful.
What is a Drive By Download?
A drive by download occurs when you visit bad actor websites or open apps that were specifically built to do “drive by” infections. In some cases, it happens on legitimate sites or in well-known apps where bad actors have injected their malicious code to cause a hidden download to occur. All of this without your knowledge and definitely without your permission.
The simple act of visiting a website or app that you thought was safe but wasn’t can result in a drive by download. Typically, the malware that is downloaded as part of the drive by process is small so it is difficult to notice. Once it’s on your device, it then executes its primary role. And that is to download the really bad stuff—viruses, worms, trojan horses, bots, etc.
In most instances, the drive-by is a two-step process. But regardless of the number of steps, the results are all the same—bad news.
When compared to other forms of malware, drive-bys are truly challenging because the bad actors didn’t have to entice you to act. Often the decision to visit a website or use an app is your choice. This makes it even more difficult to avoid because humans like to venture to new websites and apps.
Unfortunately, in many ways, we are doing a lot of the leg work for the cybercriminals.
How is this possible?
Hackers spend a lot of time looking for vulnerabilities in apps, operating systems, and web browsers. When they find
They particularly take advantage of these types of vulnerabilities in tools that we all use every day, such as web browsers. Because everyone browses the internet, web browsers are a prime target. They are constantly being hacked because the bad actors know everyone uses them.
How do they actually work?
Drive by downloads are typically designed to exploit vulnerabilities in apps, operating systems, and web browsers that have not been patched by users. Often there are patches available, but users tend to be lazy about keeping their software updated. And bad actors know this, so they build drive-bys to attack those who don’t patch their devices.
In those instances, the drive-bys are typically designed to breach your device in the following ways:
- Hijacking — to build a botnet, infect other devices, or breach your device further.
- Spying – to steal your online credentials, financial info, or
identity . - Trash your device – to simply cause trouble or intentionally harm you.
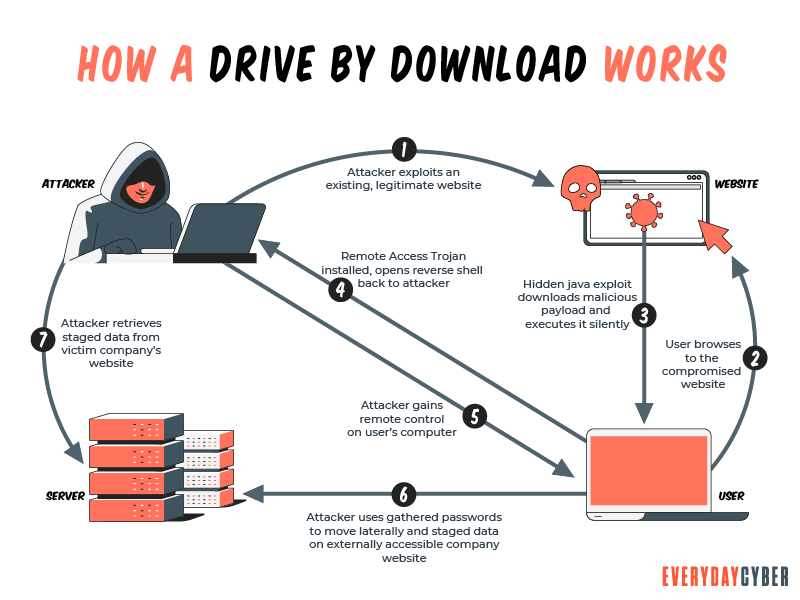
Drive by downloads occur in one of two ways:
- Unknowingly Authorized: You take an action leading to infection, such as clicking a link on a deceptive fake
security alert or downloading a Trojan that is part of an app you believed to be legitimate. - Totally Unauthorized: You visit a site and get infected simply by opening the site. These downloads can be anywhere, even legitimate sites.
Knowing exactly what the types of drive-bys is as important as knowing how the enticements work for such an attack.
Here are some methods to help you see possible red flags.
Unknowingly authorized
Authorized drive by downloads are streamlined and may even be spotted before the attack:
- Hacker builds a vehicle for malware delivery – phishing/smishing message, online ads, legitimate program downloads
- You engage delivery mechanism – downloading software, clicking a deceptive link, etc.
- Malware loads onto your device – by NOT opting out of extra software or arriving at a malware-infested site
- Bad Actor successfully accesses your device – malware takes unwanted control of your device & data.
Software (particularly those presented as free) or websites may seem innocuous, but they can be corrupted by malware.
Totally unauthorized
Unauthorized drive-bys are fairly basic despite having multiple phases:
- Bad actor compromises a web page – deploys malicious element via a
security flaw - You trigger the malicious element – visiting the page and it finds your device’s
security gaps - The element downloads malware to your device – via the
security vulnerability - Malware executes – enabling the bad actor to disrupt, control, or steal from your device
Unauthorized malicious code is delivered directly by compromised websites. The code is placed there by bad actors. They rely on flaws of digital technology and unsafe
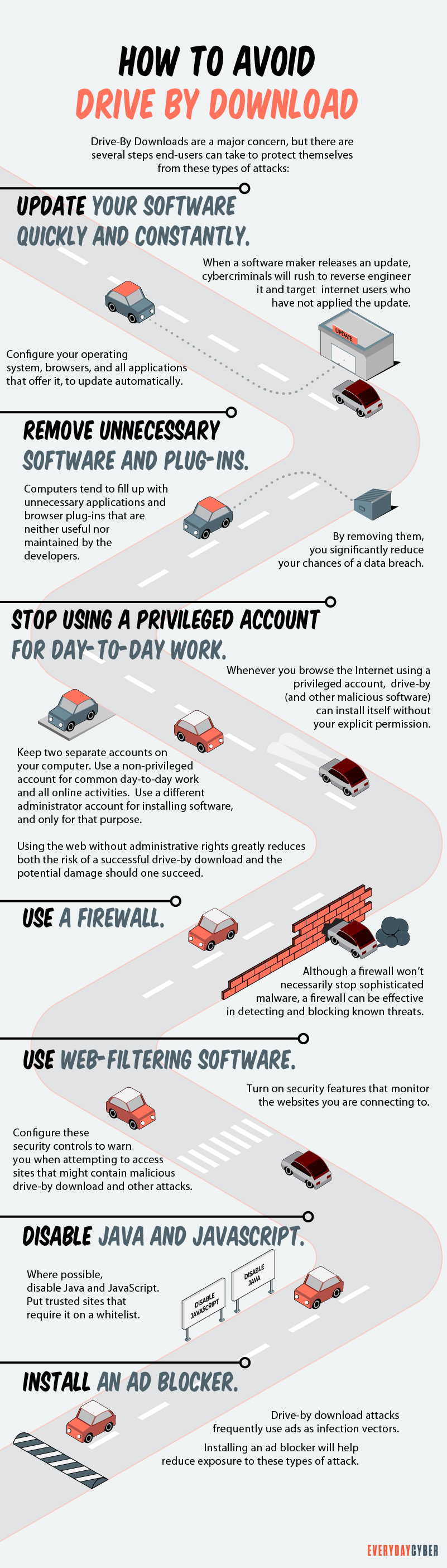
How to Avoid a Drive By Download
As with many aspects of cyber safety, the best defense is common sense, active cyber hygiene, and never taking your digital
1. Make sure your web browser and operating system are up to date.
Many patches seal gaps where drive-by-download code could burrow in. Do not delay and install these updates as soon as they are released.
2. Use your device’s admin account for software installs.
Since Admin privileges are necessary for “drive-by” downloads to install without your consent. Use a secondary non-admin account for daily use like browsing, this will restrict the possibility of an unwanted download/install.
3. Keep your programs and apps to only those necessary.
Only keep the software you trust and use regularly. Eliminate older apps that no longer receive updates. The more apps and plug-ins you have on your device, the more susceptible you are to infection.
4. Use highly quality antivirus/antimalware solutions on all your devices.
Quality tools automatically keep your malware definitions up-to-date to spot the latest threats. They scan websites proactively to block all known compromised sites.
5. Avoid sites known for malicious code.
File-sharing or Adult content sites are common points of infection. Only use well-established sites to improve your chances of staying clean.
6. Review and double-check security popups before clicking.
“Check twice, click one” – bad actors use deceptive popup ads on browsers that look like legitimate alerts. Look for typos, odd grammar, and grainy images – these are indicators of a scam.
7. Get an ad-blocker.
Drive-by attackers use online ads to upload infections. An ad blocker can help reduce your exposure to this type of attack.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is DNS Hijacking?
DNS hijacking is no laughing matter. It is a serious security threat that is consuming the cyber world. The critical role of DNS for network security has made a primary target for facilitating mass data theft.
What is Phishing?
Phishing is a cyberattack that attempts to trick people using email, text messages, phone calls, or even fake websites into giving away sensitive and confidential information.
Things About Ryuk Ransomware You Need to Know Right Now
Ryuk ransomware is one of the most dreaded malware to date. It encrypts or steals corporate data to extort millions of dollars from its victims. The Covid-19 crisis greatly influenced the recent rise in ransomware. The remote work response to the pandemic created huge gaps in the worlds cyber defenses. Threat actors saw these vulnerabilities as opportunities to spread large-scale ransomware attacks.
What you should know about Chatbots And cybersecurity
Chatbots are conversational assistants that automate repetitive chores. We like them because they assist them in completing jobs swiftly and without the need for human interaction. But an unprotected chatbot can be a security problem. Hackers can use defenseless AI chatbots to carry out nefarious activities. Read to learn more.
What is a Hacker?
A hacker is someone who challenges technology to see if it can be compromised. A hacker can black hat or white hat.
What is Bloatware?
Preinstalled and unwelcome. Bloatware is unwanted software installed on your digital device; slowing it down, reducing battery life, consuming space and just destabilizing it.

