Viruses are evolving every day. Their creators are often sophisticated businesses with big budgets and infrastructure and are smart enough to hide the viruses in your computer. If you have ever downloaded applications or programs, chances are you may have unknowingly cluttered your device with PUPs or potentially unwanted programs.
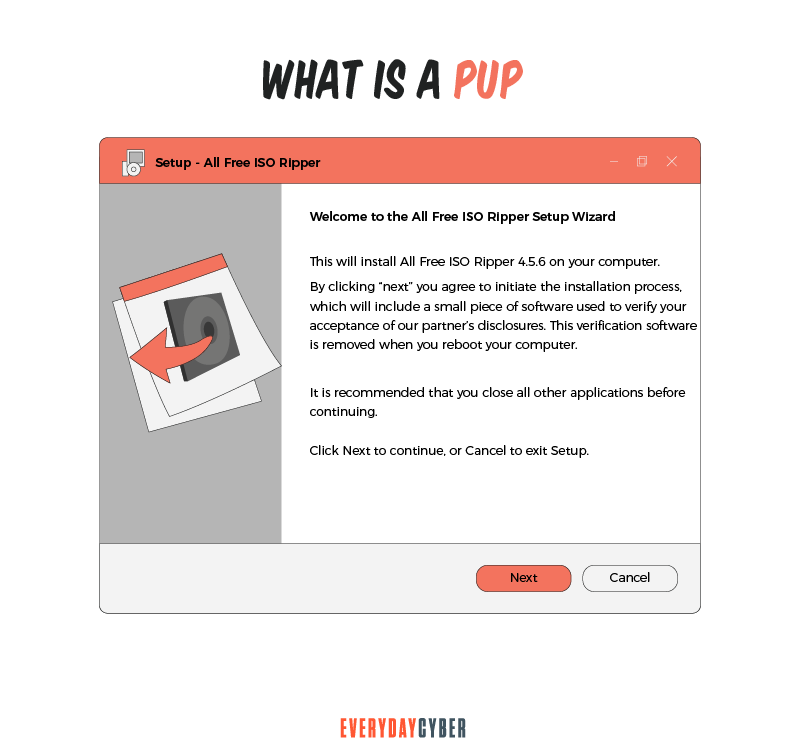
What is a PUP?
PUPs refer to programs, applications and other software downloaded onto computers or
People call PUP by other names, such as adware, crapware, PUA (potentially unwanted application), bundleware and junkware. PUPs are usually bundled with legitimate programs with a EULA or End User License Agreement, a legal contract that is standard with a download. EULAs are lengthy documents and full of legalese. This is why people skip past them and go straight to the “I accept” button.
Is a PUP different from malware?
PUP is different from malware in that malware arrives as a malicious software without the user’s permission. PUP comes with a EULA which requires users’ explicit permission or acceptance before it is downloaded to their computer.
Both PUP and malware are unwanted and may inflict similar harmful effects on computers. But Norton differentiates PUP from malware in this way. PUP includes spyware, adware and dialers that are loaded into legitimate programs that users choose and agree to download.
 On the other hand, malware includes viruses, Trojans and worms that invade computers by tricking users into clicking links or installing programs that they should not. When the click or installation occurs, the malicious software executes code that may render a device inoperable, block files, applications or even the system itself or install applications that steal data. Users have no idea all these things are happening.
On the other hand, malware includes viruses, Trojans and worms that invade computers by tricking users into clicking links or installing programs that they should not. When the click or installation occurs, the malicious software executes code that may render a device inoperable, block files, applications or even the system itself or install applications that steal data. Users have no idea all these things are happening.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
How do I know if my computer is infected with a PUP?
PUP intrusion can be triggered by user action, mostly by a click on a pop-up or link. The messages are mostly provocative but deceptive to dupe users into clicking on the pop-up or link. The pop-ups often say:
- “Your account has been compromised”
- “Claim your prize”
- “Please log in and verify recent charges”
- “Click here to run a scan”
- “Get your discount”
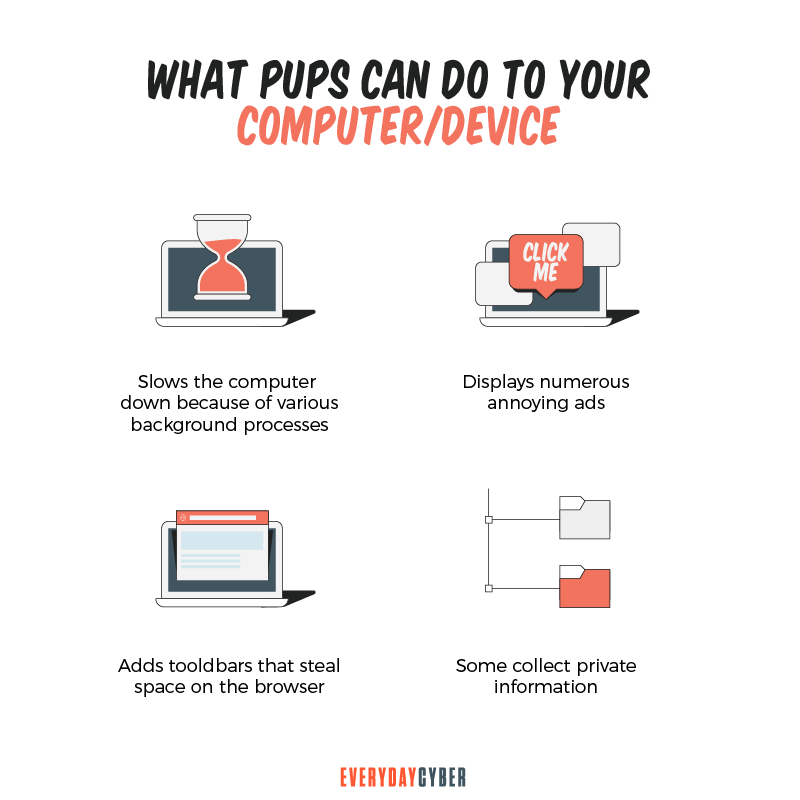
Other signs your device may have been infected are:
- Pop-ups appearing with increased frequency
- Ads appearing in unusual places
- Ads appearing seconds after a page loads
- System slowing down
- Web pages not displaying properly
- Website links leading to sites other than what you expected
- Pop-ups for fake updates showing up
- Unwanted applications you never needed and downloaded are running
- Your email or social media contacts receive strange messages from you that you did not send
How to avoid PUPs?
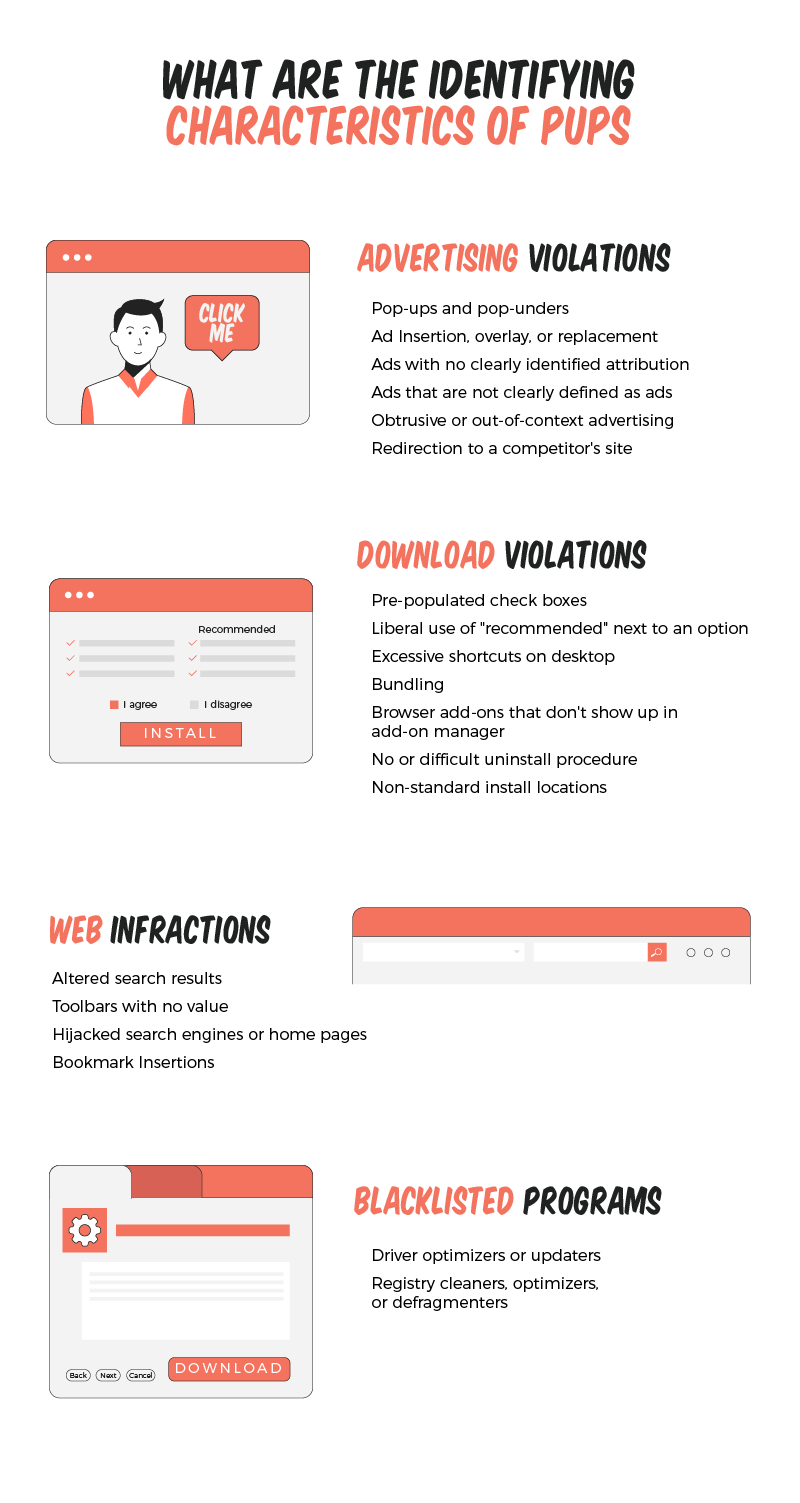
Watch out for sketchy patterns
PUPs installations use sketchy and deceiving interfaces that are deliberately designed to trick people. A marketing email makes it difficult to find the unsubscribe button or a website whose customer service contact information is obfuscated is a sketchy pattern. Other patterns to look out for:
- Incorporating some type of official insignia or an unofficial “seal” to imply credibility
- On installation dialogs, pre-populating checkboxes for options that cause PUPs to be installed
- Using highlighting and implied emphasis to drive users to a desired path – example: gray out the “skip” button and use highlighted color for “continue” button
- User behavior misdirection such as hiding free or cheaper options
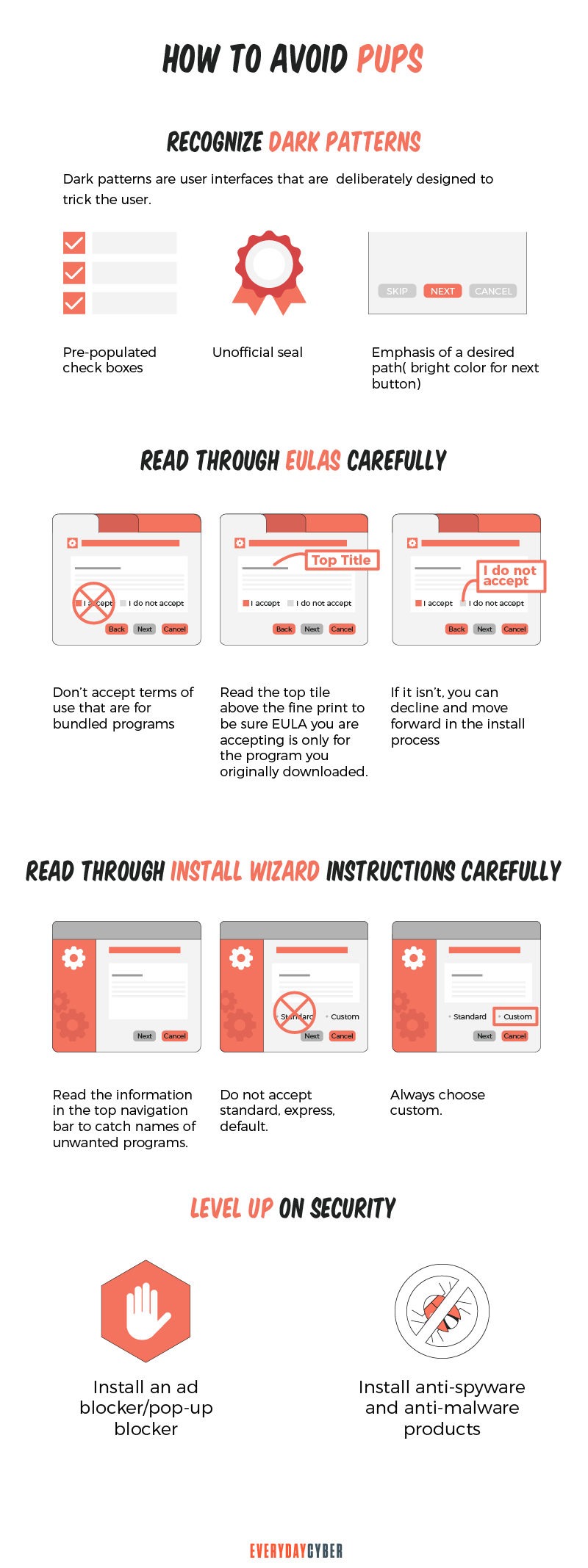
Carefully read the installation instructions when navigating the install wizard
PUPs are often intentionally hidden or obfuscated in the installation wizard dialogs of the downloaded piece of software. Their PUP designers recognize that most users tend to move quickly through the install wizard’s steps in order to quickly launch their intended program. This means users often ignore the steps or selected options that enable the installation of PUPs.
To eliminate the installation of PUPs, you should:
- Be diligent and read the information in the navigation bar of the install wizard, watching for names of unwanted programs.
- Always choose the “CUSTOM” method when installing software. Don’t accept express, default, or other installation settings that are typically recommended. Many install wizards use the term “advanced” in parentheses next to “express” to influence users to choose this method, but recognize it as a sketchy pattern and don’t choose it.
Review the End User Licenses carefully
Sketchy software developers use End User License Agreements (EULAs) as a way to mitigate liability and effectively commit the end user to whatever rules they write. Often this means you are accepting the installation of PUPs. But they are full of legalese and so virtually everyone just accepts them and moves on. So blindly accepting these agreements puts the legal burden on the end user and not the software developer for any issues or consequences of the PUP.
To avoid issue with PUPs:
- Read the main heading above the fine print to make sure the EULA you are choosing to accept is only for the program you originally downloaded. Most of the software publishers enable you to decline certain EULAs and still move forward in the install process of only the desired software and not the PUPs.
- Best option is to not accept “terms of use” for any of the bundled programs.
Level up on security
The best protection against having PUPs installed on your device is to scrutinize any installation process and be vigilant when installing downloaded software. You can also assist yourself in this process by utilizing cybersecurity software designed to identify and protect against the installation of PUPs along with malware and other questionable software.
You should consider the use of:
- Anti-virus
- Anti-spyware
- Anti-malware
- Ad blocker/pop-up blocker
Ultimately, staying vigilant and critically reviewing any software you look to install, particularly any that are downloaded from the internet, will be your best protection.
How to remove a PUP
For PUPs that keep coming, do the following steps:
Step # 1 – Scan with antimalware software
This software will scan your device for Trojans, rootkits, spyware, adware, keyloggers, ransomware and PUPs.
Step # 2 – Remove unnecessary programs
You will need to remove infected programs from your computer to eradicate the virus. Go to your Control Panel. Under the Programs section, you will see all the programs installed. Review all of them and click Uninstall on all untrusted or unwanted applications.
Step # 3 – Change all browser settings
Most PUPs and malware modify your browser settings by installing add-ons on them. Resetting your browsers will remove the modifications. Your browsers may include Google Chrome, Mozilla Firefox, Internet Explorer and Microsoft Edge. There are helpful online tutorials on how to reset browsers.
Step # 4 – Use a junkware removal tool
Junkware is not malware. They are programs that may have been pre-installed or accidentally installed on devices without malicious intent. What they can do is bloat your system by taking up space in your hard drive or memory.
A junkware removal tool scans your devices to look for unneeded programs. Once you get the list of the programs, use a cybersecurity tool from a trusted provider. Manually removing junkware is tricky so ask an IT expert for help.
After removing junkware, activate your cybersecurity software 24/7 to alert you of potential PUP and malware threats when downloading software online.
Step # 5 – Rescan browser settings
A PUP or malware changes browser settings. The removal tool removes the PUP or malware and fixes the browser settings. But when the sync option has been running during the removal process, the settings will reverse. To solve this issue:
- choose Chrome Menu and click on Settings.
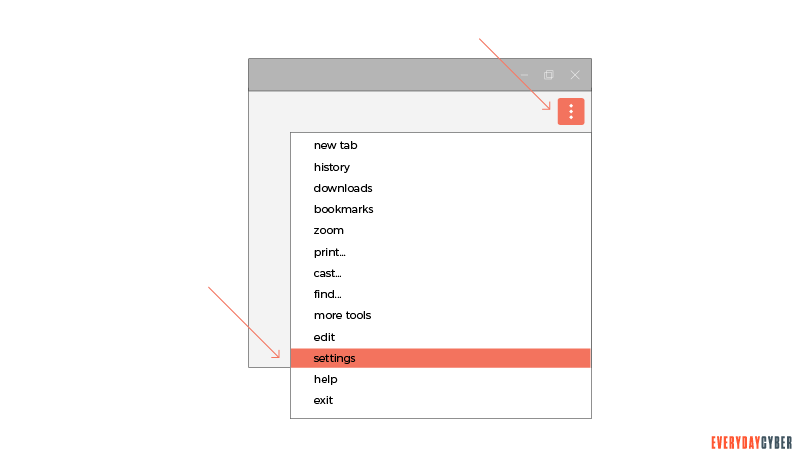
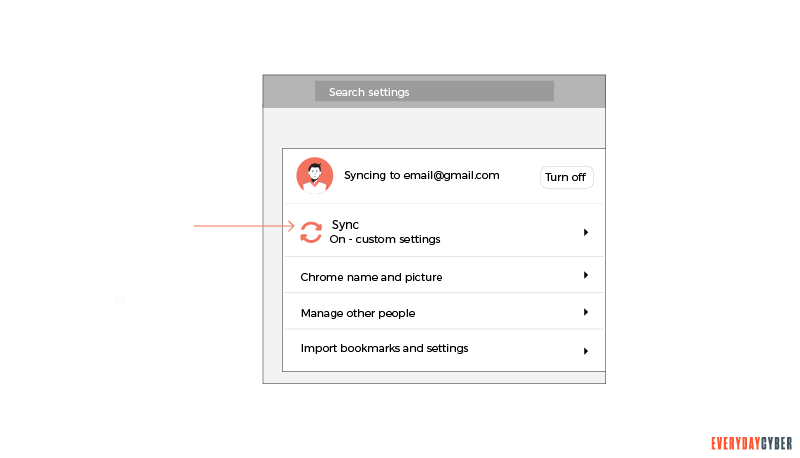
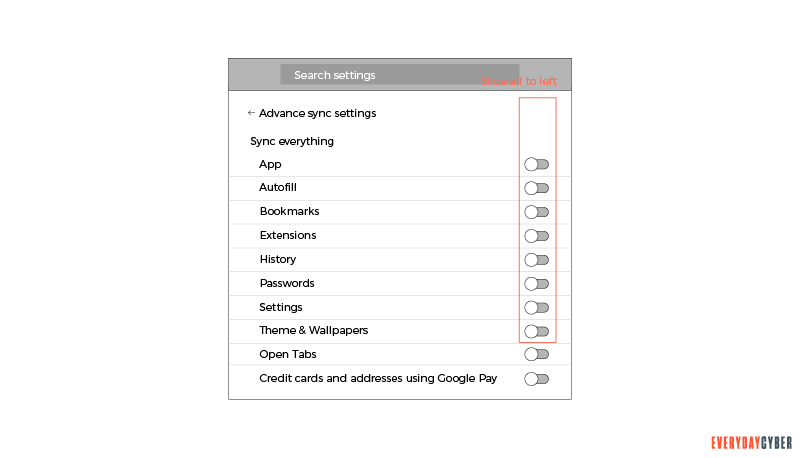
- Go to the People section and click on Sync or enter chrome://settings/syncSetup in a new tab. Disable all the options that appear.
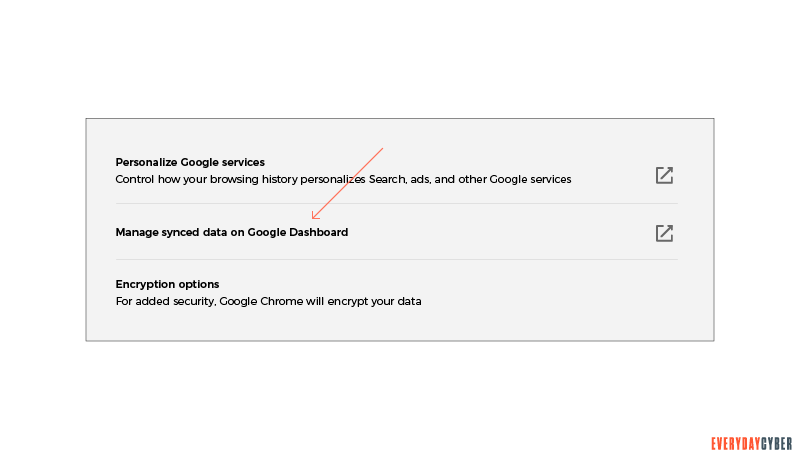
- Scroll down and click Manage synced data on Google Dashboard.
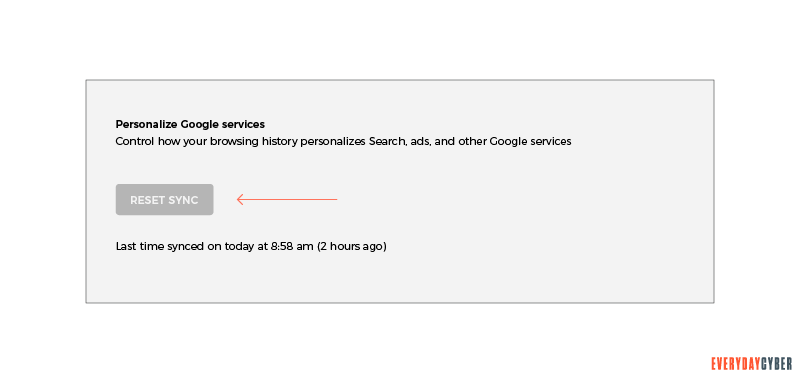
- When a new tab opens, scroll down and click on RESET SYNC. All the synced data will disappear.
- Next rerun your
antimalware scanner and remove any threats left. - Finally, restart your computer and enable the Sync.
Step # 6 – Reboot your computer with a boot time scanner
A boot time scan detects hidden viruses such as those originating in Windows files. The boot time scan should be done before the operating system runs to stop the rogue viruses from being activated and doing any damage to your computer.
Viruses from PUPs and malware are unrelenting once they are inside your computer. The good news is that there are several tools from trusted cybersecurity providers to avoid or remove stubborn viruses. What you need is an
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
14 Ways to Secure Your Home Wireless Network
Many homeowners are just unaware of the security threats that a wireless network might provide if not adequately safeguarded by a secure Wi-Fi network. We would never leave our house's front door unlocked. So you should do the same and never leave your Wi-Fi networks unprotected since it exposes you to the same or even worse threats.
What is Spear Phishing and How to Protect Yourself from It?
Spear phishing activities are becoming more sophisticated and rampant. The best defense against it is to maintain a vigilant mindset.
A 10 Step Plan for Small Business Cyber Security
An effective cyber security plan outlines in simple language the best cybersecurity practices your organization needs to stay safe. It doesn't have to be complicated, but it should be pragmatic.
Do You need to Conduct a Cyber Security Risk Assessment
Small businesses experience cyber security risks in varying forms and sophistication every day. Being complacent about the risks and ignoring the importance of a cybersecurity risk assessment can damage the health of their businesses.
How to Build a Cyber Security Awareness Program for Your SMB Business
Building a cyber security awareness culture should be a top priority for your organization. Every manager, department, and individual in your firm must commit to this on a long-term basis.
What is a Firewall?
A firewall blocks outsiders from gaining unauthorized access to your computer and helps stop malicious software from infecting your computer.

