Do you recall the story of the trojan horse that the Greeks sent to Troy in the Trojan war. It was presented as a peace offering but in fact, hid the real intent – to bring Greek soldiers inside the walls of Troy for a surprise attack.
Trojan malware (malicious software) takes its name from that classical story because it imitates the technique to infect computers and other digital devices. A Trojan will hide within seemingly harmless programs or apps or will try to trick you into installing it.
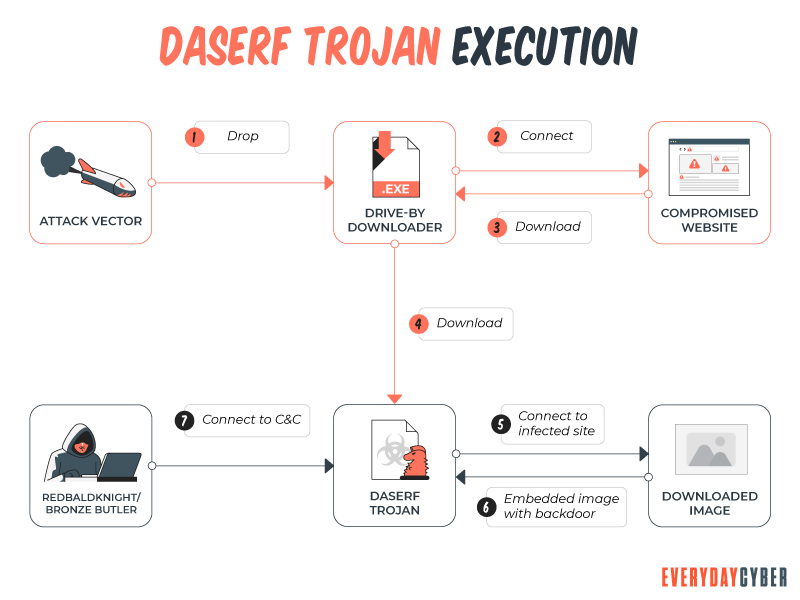
Bad actors and cyber thieves use Trojans to gain access to your devices. A Trojan is a malicious program that pretends to be harmless to trick people into downloading it. Once installed, Trojans enable bad actors to spy on you, steal your sensitive data, and gain backdoor access to your device. Some of the evil actions can include:
-
- Deleting data
- Blocking data
- Modifying data
- Copying data
- Disrupting the performance of computers or computer networks
But unlike malware such as viruses and worms, Trojans cannot self-replicate. Cybercriminals lure unsuspecting users into taking action to download the Trojan onto their devices.
How does a Trojan Horse work?
The best way to illustrate this is through an example. You might think you’ve received an email from someone you know and click on what looks like a legitimate attachment. But you’ve been fooled. The email is from a cybercriminal, and the file you clicked on — downloaded and opened — has gone on to install malware on your device.
When you execute the program, the malware can spread to other files and damage your computer.
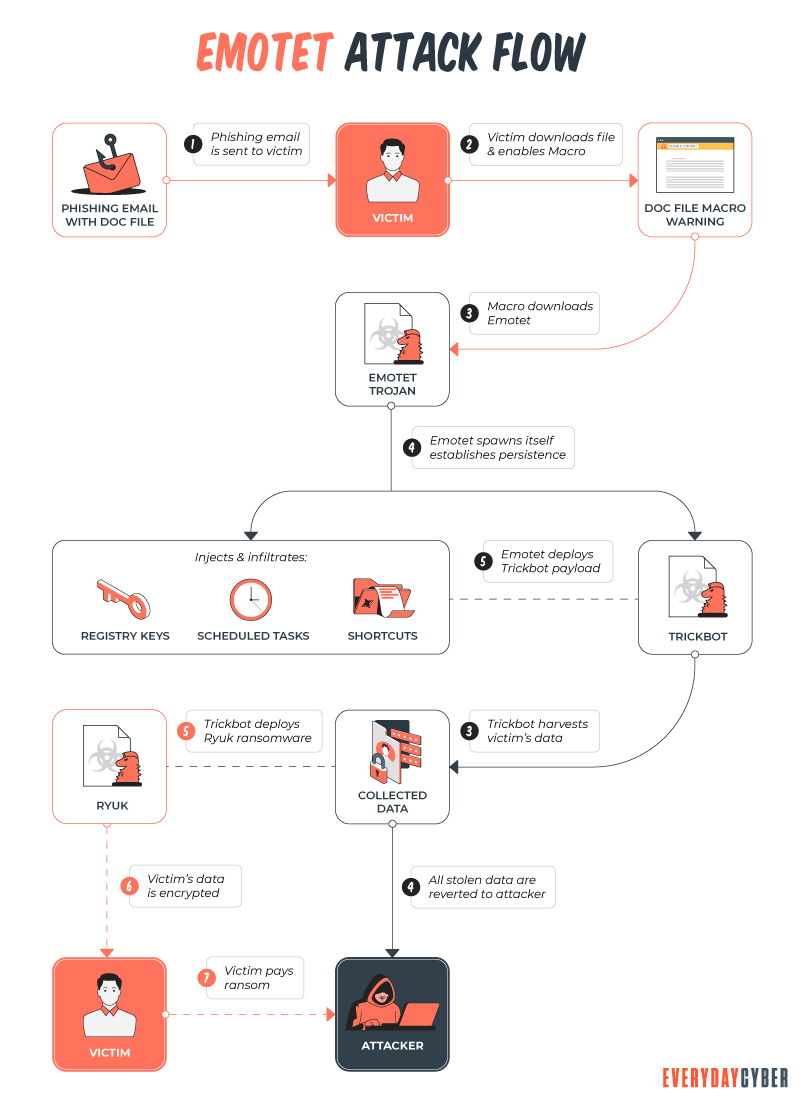
How? It varies. Trojans are designed to do different things. But you’ll probably wish they weren’t doing any of them on your device.
What can Trojans do?
Here is a list of the most common types of Trojan horse malware and what they do on your computer:
- Backdoor access – This Trojan creates a “backdoor” to access your device directly. It lets the attacker access your device (i.e. computer) and take control it. Often downloading your data to a third party, stealing your information directly, or just as often downloading more malware to your device.
- Distributed Denial of Service (DDoS) attacks – This Trojan participates in DDoS attacks. Making your device a bot in a coordinated DDos attack on some website or service. The idea behind DDos attacks is to take down a network or service by flooding it with traffic. That traffic comes from your infected devices and others.
- Downloader – This Trojan targets your already-infected computer. It downloads and installs new versions of malicious programs. These can include every other type of malware.
- Fake AV software – This Trojan looks like and kind of behaves like
antivirus software, but demands money from you to detect and remove threats, whether they’re real or fake.
- Game-thief – This is targeted at online gamers and looks to steal their account information.
- Infostealer – This one is specifically designed to steal data on your infected device.
- Mailfinder – This Trojan malware focuses on stealing your contact email addresses or anyone you have sent emails to. It then uses this list to sell to third parties or to use in some other form of an email scam.
- Ransom – This one is ransomware. It seeks a ransom payment to undo the damage it has done to your computer. This can include encrypting your device’s storage, blocking your data from being accessed, or impairing your computer’s performance.
- Remote Access – This Trojan gives an attacker control over your device via a remote network connection. It then can do a multitude of things including stealing your information or spying on you.
- Rootkit – Rootkits intentionally hide on your infected devices so that they can extend their time to run other malicious programs or software on your device.
- SMS Trojan – This type infects your
mobile devices and can send and intercept text messages on that device. In some instances, it will generate texts to premium-rate numbers to drive up yourphone costs.
- Banker – Banker Trojans target your financial accounts. It’s designed to steal your account and login information for all the things you do online. It specifically targets banking, credit card, and bill pay data.
- Instant Messaging – IM Trojans target your instant messaging apps – Snapchat, FB Messenger, WhatsApp, etc. It steals your logins and passwords on these IM platforms and may use them to create bogus IMs pretending to be you.
Unfortunately, this is just a sample list. As cybercriminals become more sophisticated, they will create many more different types of Trojan horses. So you need to be aware and be careful because they can cause a lot of harm.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
How do I spot a Trojan Horse?
Unfortunately, Trojans can look like just about anything. So, it can be challenging. It could be the computer game you downloaded from a strange website. A “free” MP3 by that band you happen to like. Through an online advertisement on a website, and intentionally or unintentionally clicked on. Untrusted links in emails can take you to a site that causes a trojan to be downloaded. Many Trojans are specifically designed to trick you into using them. They use misleading language or try to convince you they are a legitimate app.
Check your installed programs
It is always smart and worth your time to check what programs are running on your device. If you see something running that does not look familiar, investigate what it is. It could be a trojan. If you think it is a trojan, remove it – either manually or using an antivirus/antimalware tool.
Check your device’s startup software/programs
Most devices and particularly computers, have a list of startup programs/apps that get launch when you start your device. This is a favorite place for trojans to get activated. Check the startup list and if you see something there that doesn’t make sense, it could be a trojan. Modify your device start-up list and remove the unwanted software.

Keep tabs on your device performance
Many Trojan horses can be processing hogs and when operating can slow down your devices considerably. If you notice a change in your device’s performance it could very well be trojan malware. Crypto miners are a particularly notorious trojan that steals your device’s CPU to mine cryptocurrencies and that takes a lot of processing.
Install
Ultimately the best method for detecting and eradicating Trojans, like most malware, is to have quality antivirus/antimalware tools on your devices. These tools are designed to look for trojans and all other forms of malware infections. They can identify, prevent, inoculate and remove such infections before they impact your digital lives. It’s worth the investment.
Are there ways to avoid getting infected with a Trojan Horse?
As with all malware, your first line of defense is to avoid getting infected by using prudent cybersecurity practices like avoiding unsafe websites, checking every link you are thinking about clicking on before you click, don’t download anything from sites you do not trust, trust no website until you have confirmed it is safe to browse, do not download anything – from anywhere – that you do not know is 100% trusted. Finally, if you don’t already, get yourself a quality antivirus/antimalware tool for your devices.

By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is the Dark Web?
The dark web is the part of the world wide web that is hardest to reach because it lies at the center of the onion or the bottom portion of the proverbial submerged iceberg.
What is a Computer Worm?
A computer worm is not a cute, squiggly little creature. It is an evil, malicious piece of software destined to wreak chaos and disaster on many devices.
What is AD tracking?
Digital and online ad tracking is the process of gathering data and insights about the performance of online advertising campaigns. Digital systems use methods like cookies, unique tracking URLs, tracking pixels, and other tools
What is a Botnet and How to Protect Your Business from One?
A botnet is a network of computers that work as a collective to infiltrate your device. Here's how to protect your business from botnets.
What is Business Email Compromise (BEC)
Business email compromise is one of the most financially destructive cyber crimes. These are emails that appear to be sent by known or trusted sources asking for something legitimate.
What is Bloatware?
Preinstalled and unwelcome. Bloatware is unwanted software installed on your digital device; slowing it down, reducing battery life, consuming space and just destabilizing it.

