Did you know that 79% of American home W-Fi networks use weak passwords? Cybersecurity multinational company Avast’s research indicates so. Weak passwords make home Wi-Fi networks vulnerable to cyber attacks.
According to Avast’s research, the great majority of home routers in the United States are insecure. Cybercriminals can quickly obtain an individual’s sensitive information if a router isn’t properly secured. They may include personal information, financial information, usernames and passwords, photographs, and browser history.
Can a Hacker Crack Your Wireless Network Security ?
You might be amazed at how simple it is nowadays to get into your home Wi-Fi network if you have a weak password. A hacker can rent a cloud computer for relatively little money, and in most cases guess your network’s password in mere minutes via a brute force attack.
In many cases your router might have been hacked and you are completely unaware of it. Hackers can compromise the safety of your home Wi-Fi by using a technique known as DNS (Domain Name Server) hijacking, potentially causing you great harm. They can send your traffic to a website they control, tricking you to unintentionally give criminals your credit card number or Facebook login details.
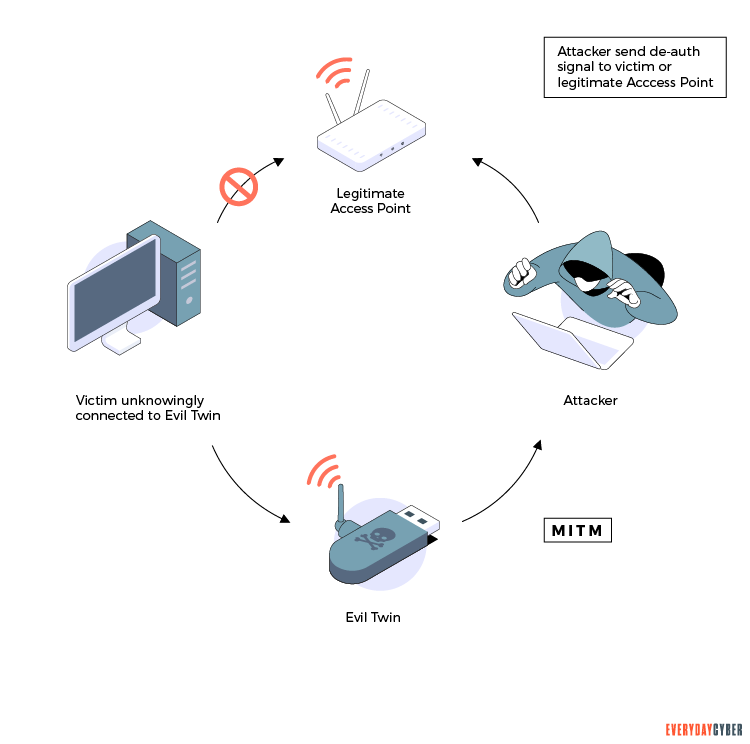
For the more tech savvy, you can find more detailed methods of how your wireless network
Thankfully, there are secure ways you can protect your wireless home network. One of the top methods it use WPA2 passwords.
What is a WPA2 Password?
Your Wi-Fi password is the network
WPA2 is a member of the Wi-Fi Protected Access (WPA) protocol for network safety. Before we can fully understand what a WPA2 password is, let’s digress a bit on how wireless
WEP or Wired Equivalent Privacy
WEP is an old type of wireless network key introduced in 1977. It encrypts data between your router and computer using a 40-bit key.
WEP’s primary purpose was to prevent man-in-the-middle attacks, which it accomplished during its time. However, despite updates to the protocol and increased key size, new vulnerabilities were discovered in the WEP standard over time making it problematic.
Within minutes, the encryption can be broken, exposing your network to the intruder. WEP is no longer supported by most current access points and routers. WEP keys should no longer be used.
WPA or WiFi Protected Access
The increasing vulnerabilities of the WEP standard necessitated a replacement of the WEP protocol. In 2003, WPA was created with
Despite WPA’s significant improvement over WEP, the ghost of WEP haunted WPA. Like its predecessor WEP, WPA was still vulnerable to intrusions.
Surprisingly, the most common method of WPA breach is not a direct attack on the protocol itself. Typically attackers targeted a WPA-enabled supplementary system. When WPA was rolled out it retained some elements of WEP that were still open to attack. This gave birth to WPA2, which we’ll discuss more extensively later in the article.
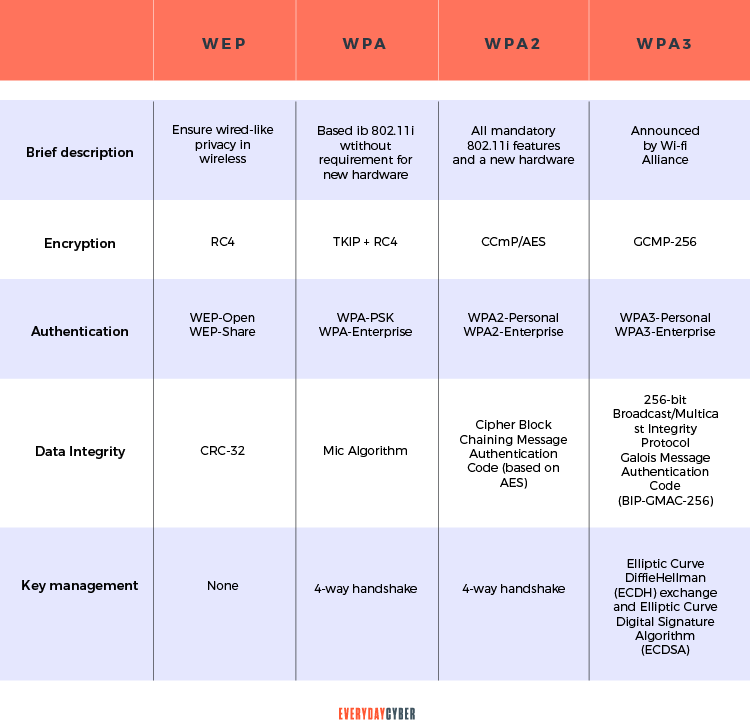
So, what is a WPA2 password?
WPA2 was introduced in 2004 to replace WPA with all its vulnerabilities. It operates in two modes: the personal mode and the enterprise mode.
A WPA2 password uses Counter Mode Cipher Block Chaining Message Authentication Code Protocol (CCMP).
A WPA2 password can be between eight and 63 characters with a random mix of uppercase and lowercase letters, numbers, and symbols. A good WPA2 password is a combination of random and uncommon character sequence to prevent dictionary attacks. A good tip in creating a strong WPA2 password is to use a unique combination that no human has ever used before.
A WPA2 password uses the Advanced Encryption Standard (AES) algorithm based on the CCMP protocol. AES is a stronger encryption method that ensures message authenticity and integrity. CCMP is more secure and reliable than WPA’s initial Temporal Key Integrity Protocol (TKIP), making pattern detection more difficult.
WPA3 or Wi-Fi Protected Access 3
WPA3 is the third generation in the WPA family introduced in 2018. It came with new features for both personal and enterprise use, including:
- Individualized data encryption
- Simultaneous authentication of access points and devices
- Stronger protection against brute force attacks
WPA3 is starting to emerge as a standard protocol for newer devices.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
How Does WPA2 Work?
WPA2 operates in two modes: the personal mode and the enterprise mode.
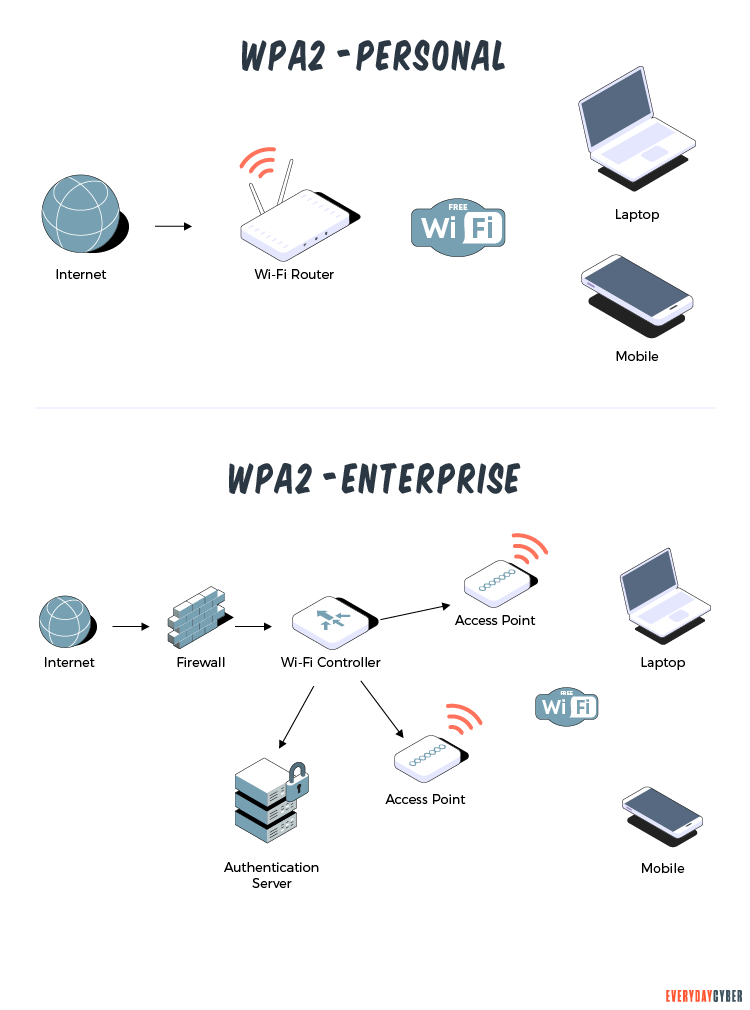
Personal mode or WPA2-PSK
WPA2-PSK offers an optional feature called pre-shared key. It requires a shared password for access and is not suitable for use in a business setting. It’s most commonly used in home networks, where the password is set in the router’s access point.
To connect to the wireless network, all client devices must use the same password. The encryption passphrase is stored on the individual endpoint devices and can be recovered quickly.
One of its downsides is that if a user leaves the network or if the passphrase is compromised in any way, the passphrase must be changed individually on all access points and all attaching devices.
Enterprise mode or WPA2-EAP
The enterprise mode offers multiple options for Extensible Authentication Protocol (EAP) which frequently used in wireless networks. EAP is an authentication framework, not an authentication method. Common use of the EAP framework are password-based authentication and certificate-based authentication, among others.
While WPA2 is a secure protocol, key reinstallation attacks are still possible (KRACK). KRACK exploits a flaw in WPA2’s four-way handshake protocol. An attacker might impersonate a cloned network and force the user to join the malicious network. This allows the hacker to decrypt a little amount of data, which can then be combined to crack the encryption key.
One methods to minimize this from happening is to ensure client devices are are patched and always kept up to date.
How to Know the Security Type of Your Wi-Fi
Knowing your Wi-Fi
Earlier protocols were designed before it was completely understood how hackers attacked routers. These exploits have been patched in more modern protocols, which are now considered to provide the best Wi-Fi
On Windows 10
- Select and click the Wi-Fi Connection icon in the taskbar
- Underneath it, click Properties
- Scroll down and look for Security Type, which shows your Wi-Fi protocol
On a Mac
- Press the Option Key
- Click on the Wi-Fi icon on the toolbar, where you’ll see your
security protocol
In Android
- Go to Settings
- Open the Wi-Fi category
- Find the router you’re connected to
- View the details and find your Wi-Fi
security type
On an iPhone
You may check your Wi-Fi safety protocol using a computing device or by logging into the router with your
Each router is unique, so you may need to refer to the documentation that comes with it. You could also call your Internet service provider that installed the router.
How Do You Create A WPA2 Wi-Fi Password?
To set up a WPA2 password for Wi-Fi, follow the steps below:
- Open a browser on your computer
- Enter the IP address of your Wi-Fi router
- Login as the administrator
- Fill up your username and password
- On the left, select the
Security tab - WPA2 should be selected
- Create and enter the WPA2 Wi-Fi password
- Save by using the save button
Tips on How to Enhance Wi-Fi Security
It’s not enough that you have set up your WPA2 password. WPA2
1. Change all default credentials
This includes usernames and passwords provided by the manufacturer.
2. Patch and update your device
To improve WPA2
3. Use strong passwords
A WPA2 password can range from eight to 63 characters. Longer is better and a mix of uppercase and lowercase letters, numbers, and symbols adds to the complexity. Avoid using single dictionary words and instead create memorable passphrases or pass sentences.
4. Upgrade your router
Check your router for any available updates on a regular basis. Also, if your router’s manufacturer stops supporting it and the device is discontinued, you should consider replacing it. Automatic upgrades are available in modern Wi-Fi solutions such as Google Wi-Fi.
5. Turn off remote access to your router
Ideally, you should log into the router from inside your own network, such as when you’re at home. Remote administration opens your login screen to the world. If cyber criminals find it on the Internet, they could brute force your login credentials and potentially access your router.
They would then have complete access to your Internet connection from the outside. That would be a real bad problem to have!!
Our final thoughts. WPA2 is by far the safest
Keep up with the trends and consider upgrading your Wi-Fi devices to stay stage.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is a Rogue Certificate?
A rogue certificate is a valid certificate issued by a legitimate certificate authority. However, it’s untrustworthy because either it was compromised or was issued to the wrong party.
What is Smishing?
Smishing is a texting scam. Texts appear to come from reputable companies inducing you to reveal personal information, such as passwords or credit card numbers.
What is Scareware?
Scareware is rogue malware that preys on people’s emotions and fears, pressuring them to download unwanted software or click a link to avoid a catastrophe.
What is Two Factor Authentication
Two-factor authentication is a security mechanism in which individuals provide two authentication factors to log on to their account. Using a username and a password to log in to an account is in itself a 2FA. So is withdrawing cash from an ATM using your ATM card and a PIN.
What is a Website Security Certificate?
A website security certificate is a digital certificate that asserts the identity of a website. It’s a virtual file approved by an industry-trusted third-party called a certificate authority (CA)
What is Typosquatting?
Cybercriminals target visitors that accidentally mistype website addresses directly into their browsers. They use typosquatting, also called URL hijacking, to deceive visitors and lead them to malicious sites they themselves have set up.


