Attacks on business email are notoriously tough to prevent.
Instead of using malware, the culprits use social engineering and impersonation to persuade individuals to act on the attacker’s request.
These attack tactics are frequently missed by traditional threat detection technologies that examine email headers, links, and metadata.
How Serious is Business Email Compromise (BEC)?
Business email compromise is one of the most financially destructive cyber crimes. These are emails that appear to be sent by known or trusted sources asking for something legitimate. A BEC scheme may be a payment request from a business or supplier. It may also be a gift card request from seemingly high-ranking executives.
Business email compromise attackers use many tricky techniques to lure you into taking action. We’ll take them up later in this post.
BEC attacks are often well-researched. Cybercriminals target C-suite and finance employees who have the power to authorize payments or have access to financial and data systems. Scams involving business email compromise are frequently successful and lucrative.
What the Numbers Say
To understand the gravity of business email compromise (BEC) attacks, let’s look at the numbers. They usually don’t lie.
Leading cloud email
- Spoofed email accounted for 71% of all business email compromise attacks
- 35% of organizations surveyed said that BEC and phishing attacks accounted for more than 50% of
security breaches - 43% of businesses experienced a
security breach in the last 12 months - 65% of IT
security officers experienced spear phishing in 2021 - 25% of organizations said 76%-100% of malware came in through email
- 34% of respondents said finance employees were the most targeted victims
spear phishing attacks
Other cybersecurity centers tell a similar story:
- The FBI’s Internet Crimes Complaints Center (IC3) reported that business email compromise attacks were the costliest in 2020 with net losses of $1.8 billion at $75,000 per incident
- The Canadian Anti-Fraud Center (CAFC) reported $30 million losses from BEC crimes in 2020
- The CAFC reported $26 million losses from BEC attacks during the first half of 2021 alone
- BEC accounted for 50% of the total financial losses of $3.5 billion from Internet crimes in 2019.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
What Does BEC Do to your Business?
BEC has serious business ramifications. BEC assaults pose a significant financial danger to enterprises, in addition to the possibility of data theft. Most BEC attacks target suppliers, vendors, and contractors requesting fund transfers. The wire transfers go straight to their fraudulent bank accounts.
In the case of invoices for example, attackers do their assignment well. They know that there are legitimate payments to be made by the company. They then impersonate suppliers requesting fund transfers.
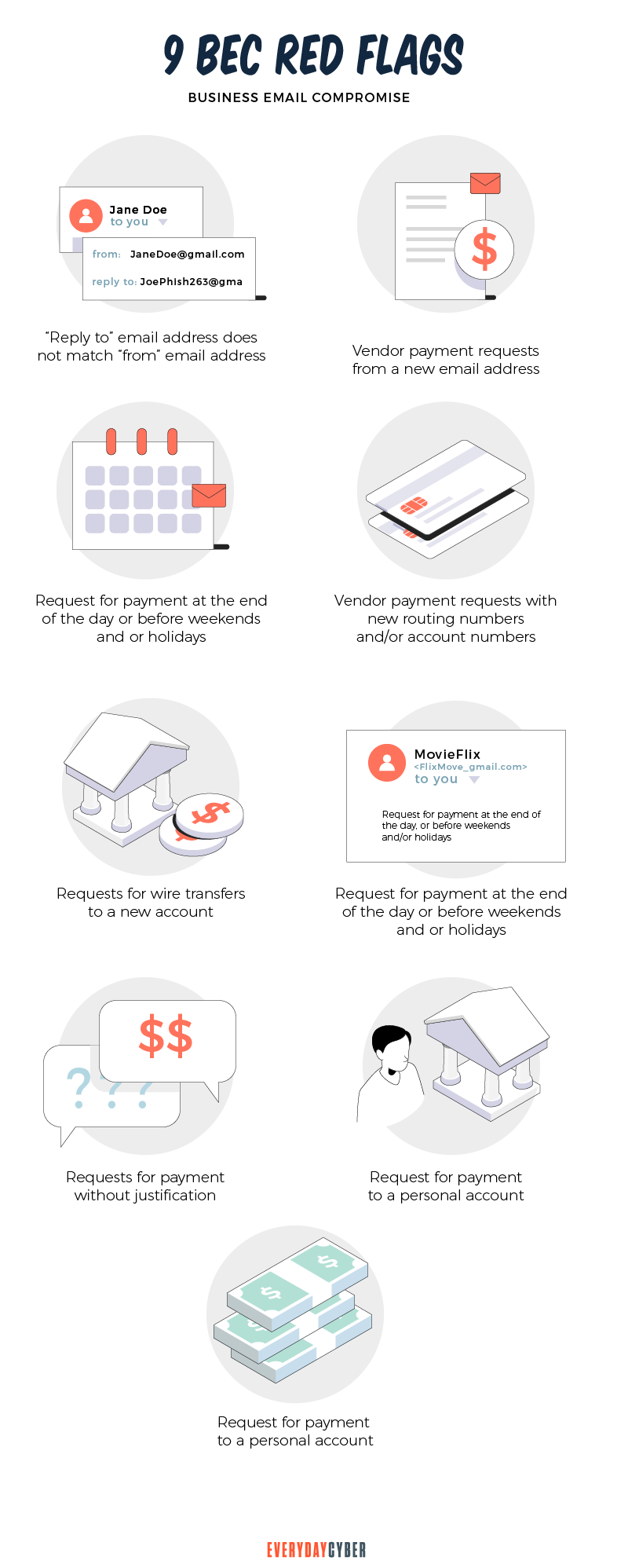
If the sender is familiar, overworked finance employees often don’t check out the little details. A missing letter or character, or a subtle misspelling in the domain name can elude the human eye. A missing letter that your employee fails to check, such as in “joe.doe@compny.com” instead of “joe.doe@company.com”, could hand over your hard earned profits to a criminal.
Furthermore, if attackers gain access to information about your company’s suppliers, customers, or partners, your company’s reputation and brand value could suffer. As a natural consequence, you could lose current and potential customers. The attackers can also come back for future attacks.
So What is Business Email Compromise?
Business email compromise is a type of cybercrime in which an attacker defrauds an organization by using email. BEC attacks are aimed at businesses of all sizes in every industry around the world. Many organizations have been exposed to billions of dollars in potential losses as a result of BEC schemes.
A BEC attack is a cyber crime that involves the hacking, spoofing, or impersonation of a company’s email address and assuming an authoritative identity. A BEC victim receives an email that appears to come from a reputable company. The email appears to be authentic. However, it usually includes a phishing link, malicious attachment, or secure attachment containing fake invoices.
Account takeover (ATO) is a related threat that’s associated with BEC. ATO happens when hackers gain access and control over online accounts using stolen credentials. ATO is a helpful tool for BEC attacks because cybercriminals can use legitimate addresses to send illegitimate requests for payment and purchase requests.
Common Types of BEC Attacks
The FBI has identified five common types of BEC attacks. Here they are:
CEO fraud
CEO fraud attackers impersonate a company CEO by compromising his email address. Using this
The attacker poses as a company executive and sends an email to a member of the finance department. He then requests funds to be moved to an account controlled by the attacker.
Data theft
This type of BEC attack usually targets HR employees in order to obtain personal or sensitive information about company executives and CEOs. This information can then be used in future attacks on CEOs.
Email account compromise (EAC)
A hacker gains access to an employee’s email address, which is then used to make payment requests to fake vendors. Payments are subsequently transmitted to the attacker’s fake accounts.
False invoice scheme
The cyber thief infiltrates the company’s email system using malware,
The cyber criminal sends an email to the hacked account instructing the recipient to transfer money to a specified account in payment for the fake invoice. Often, the email has some sense of urgency. Because the targeted employee believes the email sender, he or she sends money to a phony account linked to the cyber criminal.
Lawyer impersonation
A cyber criminal poses as a lawyer representing a client and approaches an executive of the company. The culprit makes it clear that this communication is time-sensitive or highly confidential. The BEC victim provides the requested funds under pressure and in the belief that he or she is doing the right thing.
BEC criminals usually launch their attacks during busy days and hours, such as during the late hours on Fridays or the last day before a holiday.
We might add a sixth type, which is a third party email compromise. Third parties include vendors, suppliers, contractors, partners, and other external stakeholders.
For example, a BEC attacker may take over a recognized vendor’s legitimate email account. The attacker uses this account to trick a finance executive or employee into wiring funds for payment of an invoice. Of course, the funds will land into the criminal’s fraudulent bank account.
How Business Email Compromise (BEC) Works
It’s vital to note that BEC schemes rely on social engineering and the human aspect of trust. For this reason, a BEC attack requires a deliberate and strategic approach.
Impersonation tactics such as domain spoofing and look-alike domains are used in BEC frauds. Domain misuse is a common tactic that makes these attacks effective.
It’s difficult enough to stop domain spoofing. It’s even more difficult to anticipate every possible look-alike domain. And the challenge grows with each domain of an external partner that could be used in a BEC assault to take advantage of customers’ confidence.
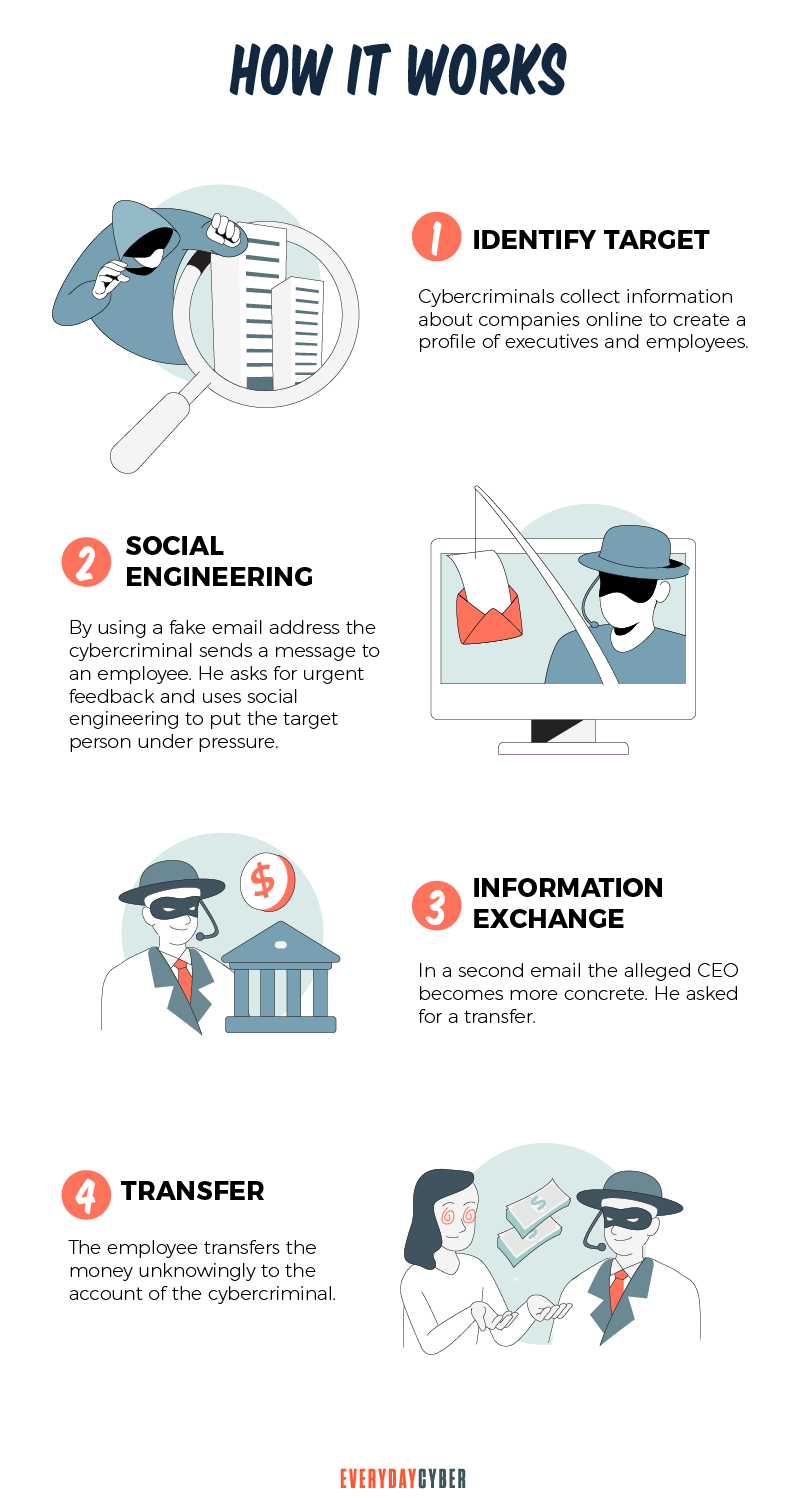
Here are the basic steps attackers do when launching a BEC attack:
1. Identify and research the target victim
The cyber criminal spends time investigating the company that will be targeted. To gather the names and titles of important company workers, the criminal leverages publicly available information such as news announcements, LinkedIn profiles, website content, and social media posts.
The ideal target is someone in a position of power. Because employees are prone to believe and react fast to emails of executives, BEC scams are easier to pull off.
2. Set up the BEC attack
After gathering relevant information, the cyber criminal either uses phishing to breach the company’s email system or spoofs a key executive’s email account.
Once inside the organization, the cyber criminal uses the compromised or spoofed email to intercept communications and monitor transactions. The criminal’s goal now is to watch legitimate behavior without being seen or heard. They may set up a monitoring and forwarding tool to observe the target invisibly. They will also keep an eye on messages from vendors or partners, particularly those involving financial transactions.
3. Launch the BEC attack
With the CEO or executive’s spoofed email account, the cyber criminal then sends targeted and urgent emails to specific employees. The cyber criminal will pose as a CEO, executive, colleague, lawyer, or business partner, asking for money transfers or secret information.
Because the email address is familiar and the request is not unusual, unsuspecting employees don’t hesitate to follow the cyber criminal’s instructions. Typically, employees believe that by paying an outstanding invoice or moving funds to a new firm partner, they are acting in the best interests of the company. Unknowingly, they’re transferring funds to fraudulent accounts.
4. Take the money or steal the data quickly
If the funds transfer or data breach is successful, the criminal takes the money or steals the data immediately and moves on to the next victim.
Common BEC Attack Techniques
Since BEC focuses primarily on social engineering, it’s simple to carry them out with only a few tools and know-how. BEC is becoming increasingly popular among attackers due to its ease of use and repeatability.
The following are five common forms of BEC attack techniques:
Leverage established relationships
Attackers make a coordinated attempt to leverage an existing trusted relationship to enable them to request urgent responses. They may masquerade as a vendor asking for invoice payments, an executive requesting gift cards, or an employee providing new payroll direct deposit data.
Use socially engineered messages
Subject lines in BEC emails frequently show urgency, familiarity, obligation, or even fear, with the goal of prompting immediate action.
BEC criminals don’t have to launch phishing attack attempts. All they have to do is use tricky but persuasive language to con their victims into giving in to their demands. BEC email content uses deceptive, manipulative language that pulls threads to make specific, seemingly legit requests.
The following are examples of common terms found in subject lines:
- Payment is due today – urgency
- Hello (First Name) – familiarity
- Overdue invoice – obligation
- This is highly confidential – fear or secrecy

Add seemingly authentic (but suspicious) attachments
Malware is frequently associated with suspicious attachments in email attacks. In BEC scams, attackers do away with malware. Instead, they attach documents that contain false invoices as a basis for their payment requests. These add-ons are lures designed to entice targets even more.
Simulate routine workflows
Every day, employees do a lot of work procedures, many of which are automated and handled by email. The more workflows are repeated, the faster staff can execute tasks without much thought.
BEC scam attempts mimic these day-to-day workflows in order to fool victims to act before thinking. For example, requests for payments on invoices is a regular part of doing business. Attackers can spoof vendor emails or launch man-in-the-middle attacks to divert the funds to the thieves’ own accounts.
Use free software for legitimacy
Attackers use publicly available software to give BEC scam attacks a sense of legitimacy. Free software also enables them to get emails past
For example, attackers can set up phishing pages with Google Sites. They can use Google Forms and Docs to harvest personal data from victims. Attackers can also use Box and Google Drive to store zero-day phishing links and bogus invoices.
Why are BEC Attacks Often Successful
To succeed, BEC attacks rely greatly on the human factor.
By nature, people will trust email senders they know and with whom they have a long standing relationship. This is why they will often execute an action even if they do not verify account information, the request’s legality or the email sender’s legitimacy.
BEC attackers take time and care building a detailed attack plan that is difficult to detect even by the most alert executives. They study their target’s email habits, including the language they use and the usual time they open their emails.
BEC criminals patiently research who a CEO will normally email for payment of invoices, gift card requests, or confidential information.
In short, among others, social engineering attacks make most BEC attempts successful.
Real Examples of BEC Crimes
No organization is immune from BEC attacks, be it government, big enterprise, small business, and even non-profits. And the threat is increasing in sophistication and frequency. Take the case of the following incidents that have cost corporate victims time, reputation, and money in the millions:
Government of Puerto Rico, $2.6 million, 2019-2020
The finance director of the Industrial Development Company of Puerto Rico mistakenly transferred almost $2.6 million to a bogus bank account. He received an email informing him that the bank account for remittance payments had changed. The email was sent from a compromised email account of the Puerto Rico Employment Retirement System. After the discovery, the FBI was able to freeze the funds.
Toyota, $37 million, 2019
In 2019, Toyota Boshoku Corporation, a Japanese auto parts supplier, was the victim of a $37 million BEC fraud. An executive in the company’s financial department was duped and persuaded to execute a wire transfer by hackers. Foreign suppliers are common BEC targets.
Save the Children, $1 million, 2018
In 2018, BEC assaults targeted Save the Children, a non-profit organization. Cybercriminals hacked an employee account at the non-profit and sent out bogus invoices and documents related to a project in Asia.
Ubiquiti Networks, $46 million, 2015
In 2015, Ubiquiti Networks, a network technology business based in the United States, was hit by a BEC attack and lost USD 46 million. The fraudsters pretended to be company employees and targeted the finance department. This demonstrates that even technology corporations are vulnerable to cyber-attacks.
Facebook and Google, $121 million, 2013-2015
The criminals created a fictitious corporation called “Quanta Computer,” which is the same name as a legitimate hardware supplier. The group then provided bogus invoices to Facebook and Google, which were dutifully paid to the criminals’ bank accounts.
Lesson learned: If two giant tech companies were victims of BEC fraud, it could happen to any business.
How can you defend against BEC
Antivirus, spam filters, and email whitelisting are ineffective against many BEC attempts that rely on social engineering techniques. However, making your employees aware of the warning signs and training them on email best practices is one of the most effective things you can do.
Here are some self-defense methods your company can use:
1. Refrain from using free web-based email accounts
Generate your own company domain and use it to create an individual company email account for each employee instead of using free web-based accounts.
2. Educate your people
Educating your staff about the scam is one of the most effective strategies to avoid a BEC attack. They must recognize the telltale indicators of a phishing email, such as messages that:
- Contain grammatical and spelling errors
- Include links and attachments that were not requested
- Include header information that differs from the email address
- Convey a sense of urgency, secrecy, or fear
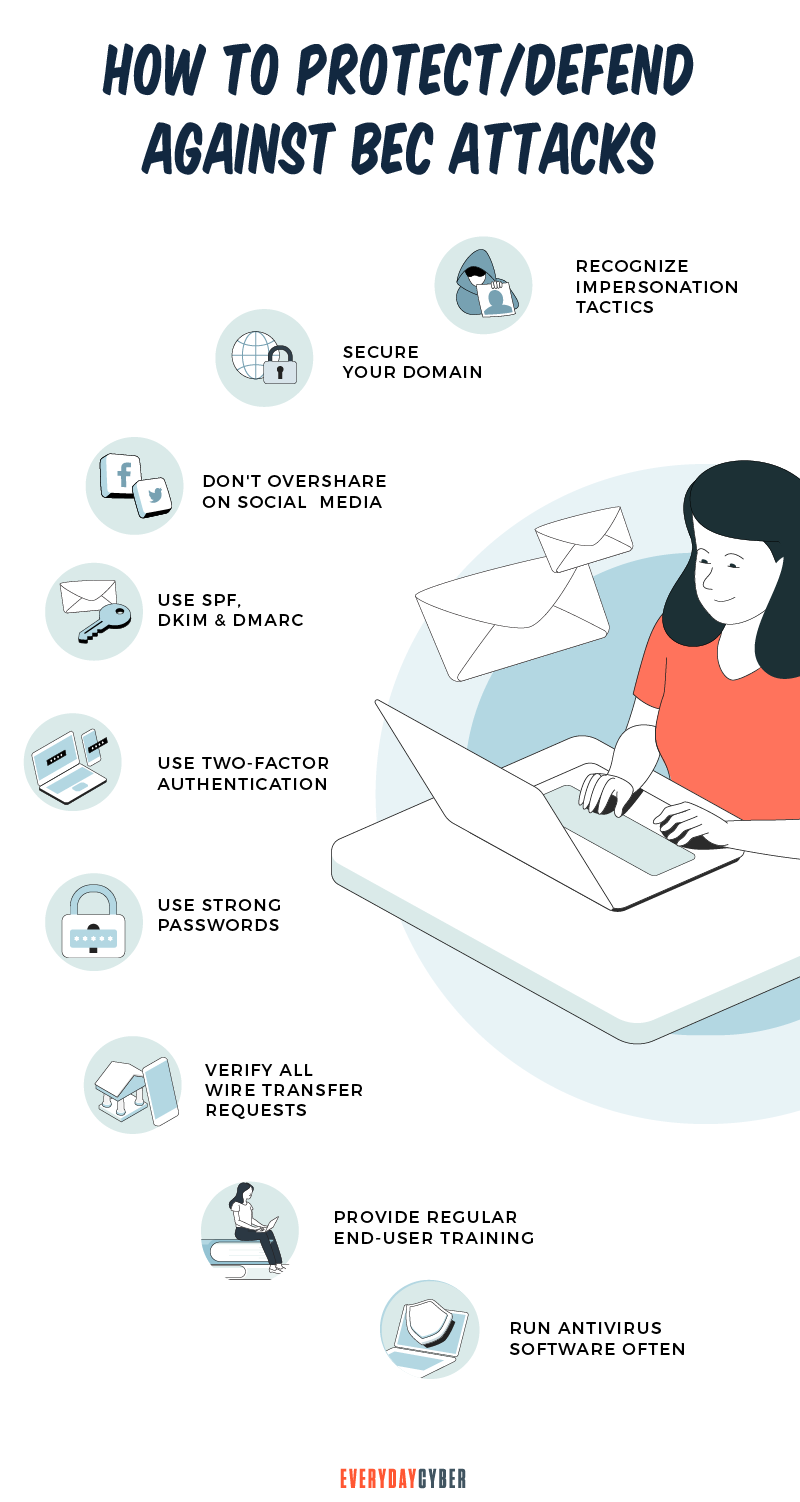
3. Never open emails from unknown senders
If you do, avoid clicking on links or opening attachments since they may include malware that can infect your computer.
4. For corporate email accounts, enable multi-factor authentication
To log in, you’ll need more than one piece of information, such as a password and a dynamic pin, code, or biometric feature. Multi-factor authentication makes it tougher for a cybercriminal to gain access to an employee’s email, making a BEC attack more difficult.
5. Verify the sender’s email address
The extension of a faked email address is subtly the same as the authentic email address. For example, an email recipient may mistake the fake “joe.doe@compny.com” for the authentic “joe.doe@company.com”.
You should also check the email headers. An email message’s headers may contain information that can assist you in determining if it is valid or not. For example, the email could have a different Internet Protocol (IP) address than the one your organization usually uses.
6. Always double-check before sending money or sensitive information
Employees should be required to validate email requests for a wire transfer or secret information as routine operating procedure. Confirm in person or use the company’s
7. Protect your brand by implementing email security measures
Setting up email
- Framework for sender policy (SPF) – SPF enables you to create a domain name system (DNS) record that indicates which IP addresses are authorized to send emails on your behalf.
- Mail was recognized by domainkeys (DKIM) – DKIM adds a “signature” to your outgoing email that informs your recipient’s email servers that the message is genuine and came from your domain.
- Authentication, reporting, and conformance for domain messages (DMARC) – DMARC takes advantage of both SPF and DKIM to improve email
security . You can create rules that flag email communications that are suspicious. An email will be rejected if it does not match specific verification criteria.
8. Install malware protection on all devices
Malware protection should be installed on your business’s devices to guard against malware and phishing attacks.
Our final thoughts. You can lower your risk of being a victim by learning how BEC scams work and taking the necessary precautions to protect yourself. We hope you’ll find the measures we’ve highlighted to keep your firm safe against corporate email compromise scams.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is a Website Security Certificate?
A website security certificate is a digital certificate that asserts the identity of a website. It’s a virtual file approved by an industry-trusted third-party called a certificate authority (CA)
The #1 Cyber Threat Small Businesses are Facing
Phishing attacks are the most widespread and most damaging threat to small businesses, accounting for 90% of all cyber security breaches.
Do You need to Conduct a Cyber Security Risk Assessment
Small businesses experience cyber security risks in varying forms and sophistication every day. Being complacent about the risks and ignoring the importance of a cybersecurity risk assessment can damage the health of their businesses.
What is a Remote Access Trojan (RAT)?
A remote access Trojan is a software used by hackers to gain unauthorized access and remote control on a user’s computer or mobile device, including mouse and keyboard manipulation.
What is Hacking?
Hacking is an old game in the cyberworld with ever changing players and techniques. It may be done with good intentions or malicious motives. It is growing rapidly because of the proliferation of devices.
What is Digital Identity?
Your digital identity is your set of unique features and characteristics identifiable to you. It is all data that can be traced back to you.

