Phishing is a cyberattack that attempts to trick people using email, text messages,
Phishing scams extract information like social
The goal can be anything from trying to get you to send them money, hand over confidential information, or even download malware unwittingly. The scammers use lies, trickery, forgery, and outright manipulation to succeed.
Their goal is to obtain information about you to steal money from your accounts, use your credit card, perform identity theft, and a myriad of other crimes.
Phishing falls into a cybercrime category called “Social Engineering,” which refers to cyber-attacks that rely on human fallibility rather than hardware or software flaws to work.
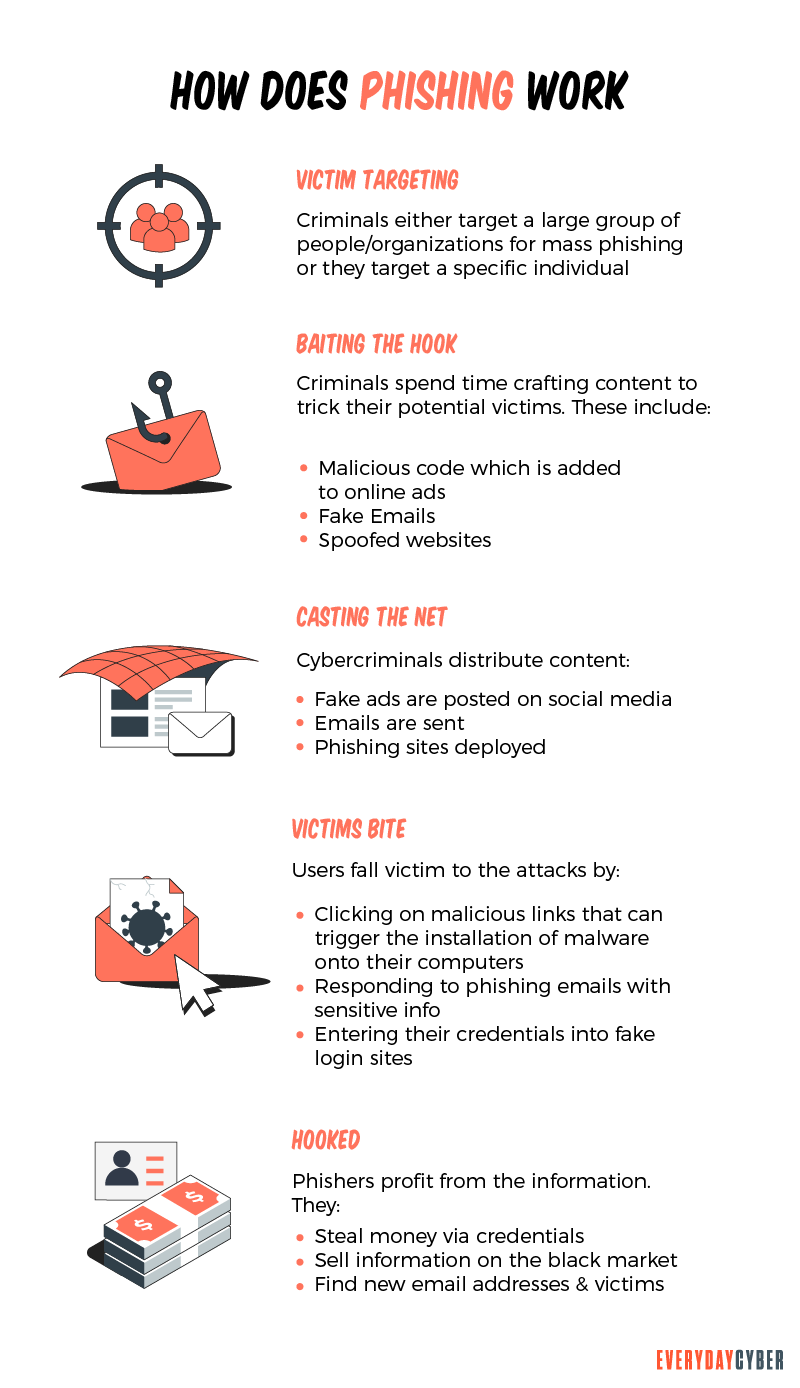
How does Phishing work?
- The bad actors start by determining who their targeted victims will be (will it be businesses or individuals) and builds strategies to determine how they will extract the information they want.
- Then they use methods like fake emails or bogus web pages to send messages via email, SMS, or even
phone calls that lure data from their victims. - They send messages that appear trustworthy to the victims, which fool you into taking action like clicking on a link.
- Once the phishing attack is in motion, the bad actors will monitor and collect the data that victims provide on the bogus web pages.
- Once they have collected the victim’s information, the bad actors use the data for illegal purchases, sell the information on the dark web for others to use, or commit other fraudulent acts like identity theft.
Phishing attacks do not all look or operate the same, and the bad actors are a very creative group. Phishing scams will take many forms and have different goals in executing them.
What are the types of phishing attacks?
There are many different Phishing attacks, but far and away, email is the primary delivery system. Phishing emails will use various techniques to entice, encourage, even scare you into clicking the link. They convince you that if you don’t, you may lose out on an opportunity, or something terrible might happen like having an account closed, or service stopped if you don’t respond. The use of fear, uncertainty, excitement, fear of missing out – exploiting human emotion – is part of the “Social Engineering” methods the bad actors use to cause victims to click when they should not.
Some example attacks include emails that lure you into clicking on a link to verify that a credit card or bank account is yours. Others might scare you to take action because if you don’t, something terrible could happen, such as losing access to your email if you don’t click the link. If you click the link, a fraudulent website is presented. The bad actors ask for personal or financial information. The information is captured and then used for bad things. The other common scenario is when you click the link, malware or adware installs onto your device, which creates a whole new set of issues.
There are 5 primary types of phishing attacks.
- Basic Phishing emails
The most common form of phishing is through emails that lure, entice or scare you into action – typically to click a link in the email that takes you to a fake website to extract sensitive info.
- Spear phishing
Spear-phishing is email targeted toward a specific individual, business, or organization. Unlike standard phishing emails, the bad actors who send them spend time researching their victims. The technique uses even more in-depth social engineering methods and designs the emails to look like they’re from legitimate sources.
A classic example of spear-phishing target specific employees and make the email appear to come from their boss requesting the employee access sensitive company information or take some action – like paying a bogus invoice or sharing confidential information. Given the email’s apparent source, the employee may follow the instructions, not realizing it was bogus.
- Whaling
Whaling attacks target corporate leaders (chief executive officers, chief operating officers, or other high-ranking executives in a company.) The objective is to fool these leaders into giving up the most confidential and sensitive corporate data.
These attacks tend to be the most sophisticated and involve plenty of research by scammers. They rely on fraudulent emails that appear to be from trusted sources within the company or legitimate outside 3rd parties.
- Clone phishing
Clone phishing might be one of the most difficult phishing scams to detect. In this type of attack, bad actors create nearly identical versions of emails that victims have already received.
The senders’ address in the cloned email is nearly, but not quite, the same as the message’s original sender’s email address. The email’s body is duplicated, so the emails look the same. The threat comes from the attachments or links in the cloned message. They are changed to a link or attachment that the bad actor has created. If you click on the link or download the attachment, it will take you to a fake website or open an infected attachment.
- Pop-up phishing
Pop-up phishing, which is a variant of malvertising or adware, is a scam in which pop-up ads trick you into installing malware on your devices or convince you to purchase
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
How to protect yourself from these attacks?
Bad actors are a creative group and are constantly coming up with new phishing scam techniques, but there is good news. You can protect yourself and your organization by being cautious, diligent, and applying common-sense practices.
-
- Don’t open suspicious emails. Emails supposedly from financial institutions with subject lines such as – “Account suspended!” or “Funds on hold” — delete it. If you think there is a problem, actually log in to your account or contact the bank directly. If there really is a problem, you’ll find information once you’ve logged in.
- Don’t click on suspicious links in emails. If you open an email from someone you don’t know and are instructed to click on a link, don’t.
- Don’t EVER send financial information through email. Banks or credit card companies never ask you to provide bank account numbers, credit card numbers, your Social
Security number, or passwords through email. - Don’t click on pop-up ads. Scammers can add fraudulent messages that pop up when you visit even legitimate websites. Avoid this temptation. Fraudsters use these ads to install malware on your computer or scam you out of a payment for a computer clean-up you don’t need.
- Use spam filters. Spam filters can help block emails from illegitimate sources. But they aren’t 100%, so follow all the other common-sense practices.
- Use quality
antivirus /antimalware tools. Protect your device using strong, multi-layeredsecurity software.

How to recover if you clicked or downloaded from a phishing email?
The scammers got you. Perhaps you sent financial information or clicked on a link that installed malware on your computer.
If this is the case, you will want to act quickly. Here are some steps you can take if you think a phishing scam has hit you.
- Change your passwords – Change all passwords you use for your banking, credit card, and other accounts. If your financial institution supports multi-factor authentication enable it. Multi-factor authentication requires entering a second piece of information — such as a code sent to your smartphone — to access an account.
- Alert the credit bureaus – Visit the national credit bureaus’ home pages and alert them that you’ve been the victim of a phishing attempt.
- Contact your credit card providers – Inform your credit card providers you may be a victim of a phishing scam and have them freeze your account, check for, watch for fraudulent transactions and issue you a new card.
- Watch your credit reports – Order free copies of your credit reports from AnnualCreditReport.com. Check unfamiliar activity to ensure no one has opened credit card accounts or loans in your name.
- Monitor your credit card statements – Watch for any unauthorized or suspicious charges.
So here is everyone’s reality – Phishing attacks are the most prevalent form of cybercrime. Keep your eyes peeled, or you may get hooked!!
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is the Dark Web?
The dark web is the part of the world wide web that is hardest to reach because it lies at the center of the onion or the bottom portion of the proverbial submerged iceberg.
What is Bloatware?
Preinstalled and unwelcome. Bloatware is unwanted software installed on your digital device; slowing it down, reducing battery life, consuming space and just destabilizing it.
What is a Botnet and How to Protect Your Business from One?
A botnet is a network of computers that work as a collective to infiltrate your device. Here's how to protect your business from botnets.
What is a DDoS (Distributed Denial of Service) Attack?
DDoS attack or Distributed Denial of Service, is a coordinated attack intended to crash and make unavailable targeted websites and online systems by overwhelming them with data.
7 ways to secure your home office
People working from home perform most of their tasks online. They are now more exposed to cyber attacks than ever before. Cyber criminals see a great opportunity in the massive growth in working from home and the vulnerabilities of home office security.
What is a VPN?
A VPN is a virtual private connection to a VPN host server to hide your identity, address and online activity when using a public Internet connection. It does this by encrypting your data and turning them into “rubbish” so no one can make sense of it even if they get their hands on it.

