Ransomware is a pretty simple concept to understand. Bad actors, install malware (malicious software) on your device encrypt its data and then demand a ransom to restore access.
It’s dangerous for you and incredibly profitable for hackers. Today ransomware has taken over as today’s no. 1
In most cases, the victim must pay the cybercriminal within a set amount of time or risk losing access forever. The really bad side is that since malware attacks are generally deployed by criminals, even paying the ransom doesn’t ensure access will be restored.
Ransomware doesn’t just affect individuals like you and me, it is used to target small and big businesses as well. For them, the consequences can be even bigger and can cause businesses to fail. Ransomware is serious and needs to be taken seriously and you need to protect yourself.
How does Ransomware work?
In most cases Ransomware holds your files and data hostage, keeping you from your documents, photos, applications, and financial information. The data is still on your device – computer,
While the idea behind ransomware may be simple, fighting back when you’re the victim of a malicious ransomware attack can be more complex.
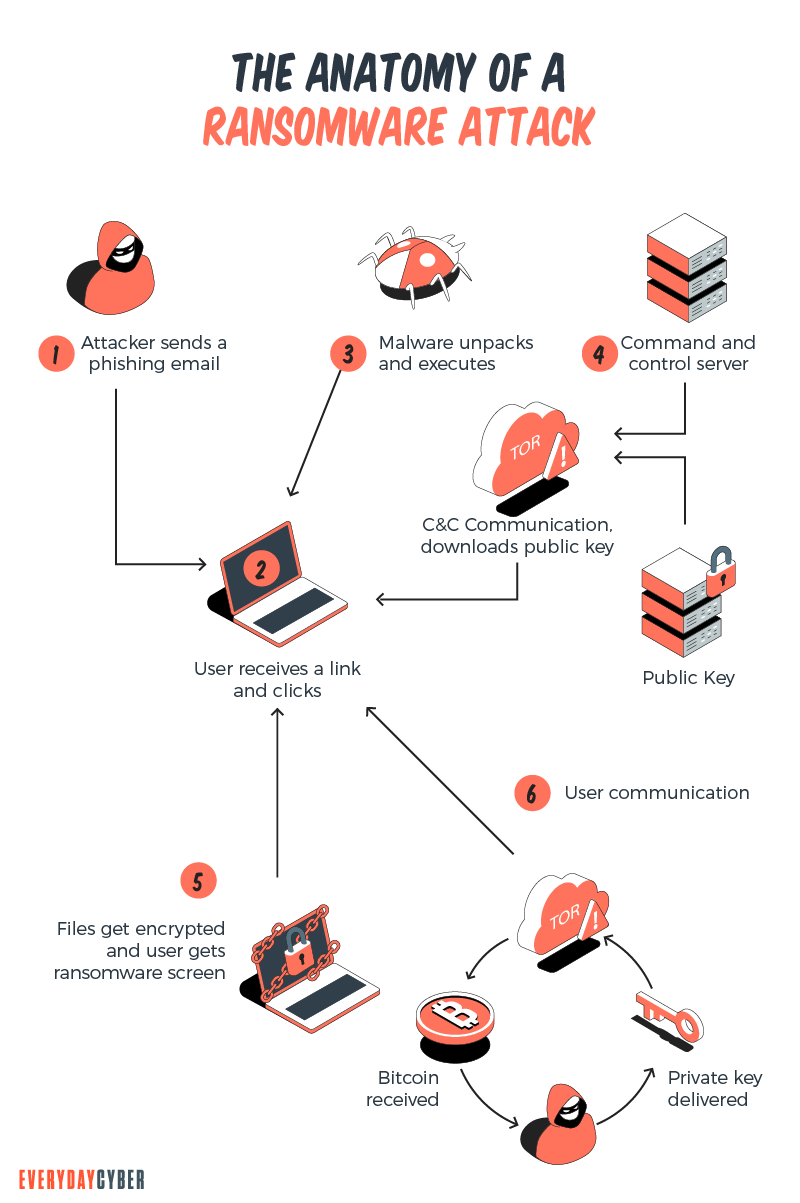
The Ransomware thieves will ask for a monetary ransom, usually in the form of cryptocurrency due to its anonymous nature. The supposed implied agreement is if you pay, they will supply the decryption key and you will be able to restore access to your data. But they are criminals and criminals lie, so there is no assurance that if you pay the ransom you will in fact get the decryption key. It can be a very difficult situation to find yourself or your business in.
Try understanding the types of ransomware out there. Learn the dos and don’ts surrounding these attacks. Knowledge can go a long way toward helping protect yourself or your business from becoming a ransomware victim.
Types of Ransomware
Ransomware attacks are executed using a number of different methods. Some implementations are more harmful than others, but they all have one thing in common: they are seeking a ransom of some type – usually financial.
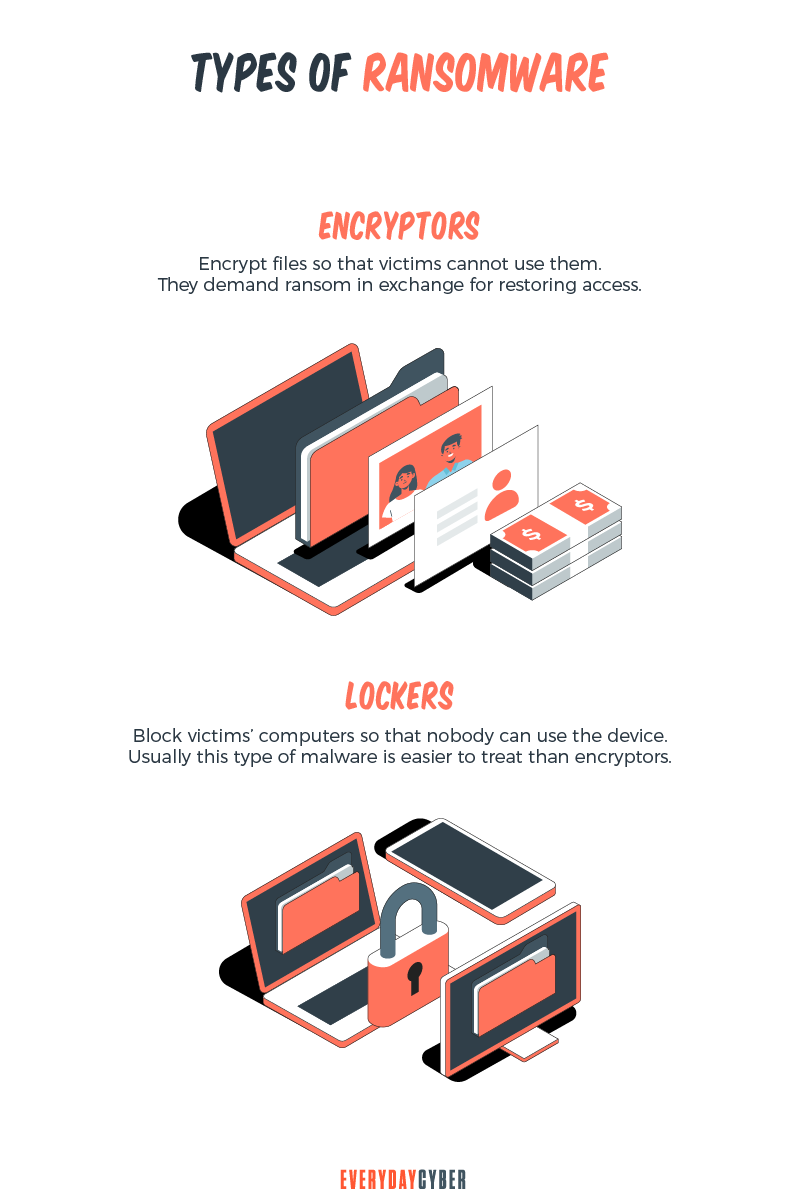
These are some of common implementations of ransomware.
Crypto malware. This ransomware encrypts things like your files, folders, and hard-drives. Victims are typically asked to pay ransom in cryptocurrency (i.e. Bitcoin) to retrieve their data.
Lockers. This ransomware infects your operating system to completely lock you out of your computer or device. Making it impossible to access any of your files or applications. This type most often
Doxware. Also known as leakware or extortionware, threatens to publish your personal, confidential or compromising data online if you don’t pay the ransom.
Scareware. This one is fake software that appears to be an
RaaS. “Ransomware as a service,” has become a new method allowing any bad actor to simply pay for a service to execute any one of the above-mentioned attacks. It has made cybercrime as service from one bad actor to another.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
How do you get Ransomware?
Like most types of malware, ransomware often originates through malicious email attachments and fake links. It also can come through social media networks, drive by downloads, and numerous other methods that bad actors use to infect digital devices.
The most prevalent methods are:
Social engineering – They use human vulnerabilities, emotions and curiosities to trick you to click or download. Malicious files are often disguised as ordinary documents (order confirmations, receipts, bills, notices) and appear to have been sent by a reputable company, institution, friend or colleague. Download one of these to your device your PC, open it, and you’re infected.
Malvertising – ads, often paid ads delivering ransomware, spyware, viruses and other nasty things, all at the click of a button. Yes, cybercriminals will buy ad space on popular websites (including social media networks or YouTube) to get their hands on your data.
Exploit kits – Tools designed to exploit vulnerabilities and
Drive-by downloads – malicious websites take advantage of out-of-date browsers or apps to silently download malware in the background while you’re browsing a website or watching a video.
How to protect from getting hit by Ransomware?
First, exercise common sense cybersecurity methods and common-sense practices when interacting in the digital world. Apply healthy skepticism and validate the website before you browse, never click anything before confirming the link is safe, and do not download any file that you are not 100% sure is safe.
Even applying digital best practices, malware, and ransomware can still hit you.
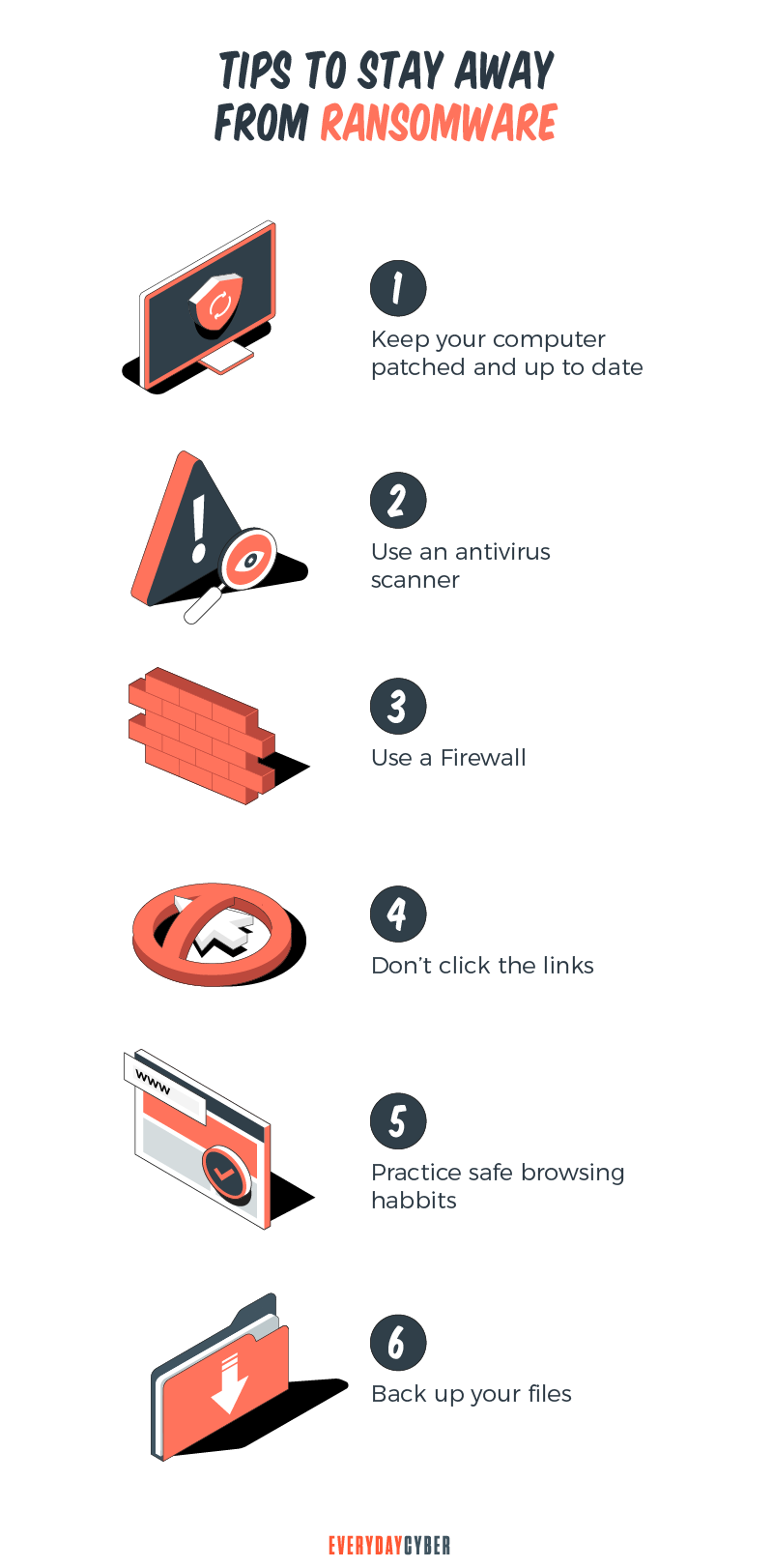
The best strategy to protect against this threat is to be proactive and take steps that provide you with ways to recover your data, your systems, and your devices in the event you get bitten by ransomware.
Back up your important files, your systems Use external drives, cloud storage, or both. There are a number of free cloud storage services out there so cost should not be a barrier. Cloud services such as Dropbox, Google Drive, MS Onedrive, and others offer considerable storage for free and if you have large amounts files, pictures, documents, they all have large volume paid options as well.
Invest in quality
Keep your operating system and app software updated Bad actors are constantly looking for vulnerabilities in operating systems and application software. Software manufacturers want their products to be safe and when they discover vulnerabilities in their products, they are going to want to fix them as quickly as possible through updates and patches.
Always keep your operating system and app software updated, especially with updates or patches that specifically address security issues.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is Phishing?
Phishing is a cyberattack that attempts to trick people using email, text messages, phone calls, or even fake websites into giving away sensitive and confidential information.
What is AD tracking?
Digital and online ad tracking is the process of gathering data and insights about the performance of online advertising campaigns. Digital systems use methods like cookies, unique tracking URLs, tracking pixels, and other tools
What is a Computer Virus?
What's a computer virus? We hear about it all the time but do you really know what it is and how to prevent one?
What to do if your email Is hacked
Identity theft and bank account or credit card fraud are both possible consequences of a stolen email. If you suspect that your email has been hacked, act quickly to limit the harm. Here are 9 steps to take back control of your email if you have been hacked.
What is a Rogue Certificate?
A rogue certificate is a valid certificate issued by a legitimate certificate authority. However, it’s untrustworthy because either it was compromised or was issued to the wrong party.
What is Shoulder Surfing?
Shoulder surfing is a form of social engineering that enables cybercriminals to gather information just by looking over their victims’ shoulders. The aim of shoulder surfing is to obtain personal data, such as usernames, passwords or personal identification numbers (PINs), bank account numbers or credit card numbers.