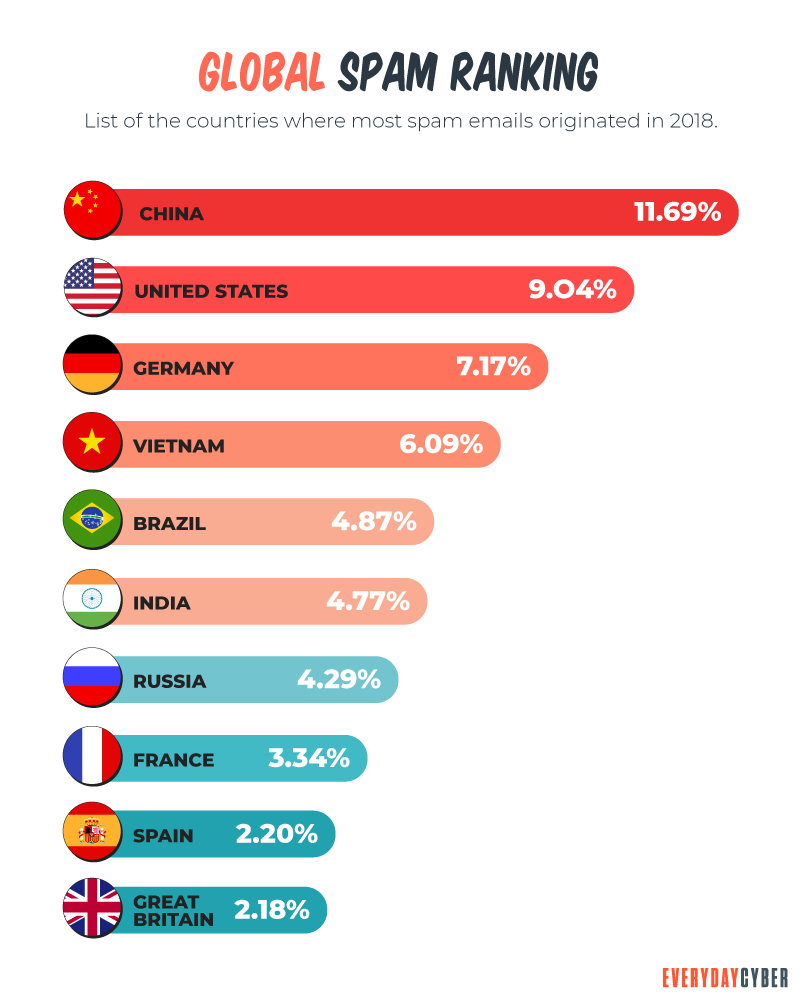
Spam is the digital equivalent to the junk mail you get in your physical mailbox. It is unsolicited messages, sometimes referred to as junk mail, that tend to fill your email inbox or text messaging app with annoying and generally useless material.
Spam can be unending and very annoying, often attempting to convince you to buy something you don’t need. Often these messages are completely untruthful, such as advertising male enhancement pills (when they contain nothing of the sort). Spam also includes phishing content which are messages, emails, and texts, designed to trick or lure you into giving up personal information. Some span can be legitimate advertisements or promotions but they were never something you signed up for.

Spam messages are sent out in mass quantities by spammers and bad actors that doing one or more of the following:
- Extract money from a percentage of recipients (even a small % of a big number targets can be consequential) that respond to the message
- Execute phishing scams – to obtain passwords, credit card numbers, bank account details, and more
- Spread malware (malicious software) code onto a victim’s devices
How do you protect yourself against spam?
There are various strategies and techniques that can help reduce the amount of spam you will have to deal with. Below are some of them.
Set up multiple email addresses
Consider having at least two email addresses. One that is consider private and one that is considered public.
Private email address
Would be used for personal correspondence only and with only trusted individuals. You would never publish this email address on publicly available sources or use it to sign up for services. It would be your email address to communicate with friends and colleagues.
Public email address
Use your public address when you need to register on public forums, chat rooms, subscribing to mailing lists or Internet services like ecommerce sites.
Treat your public address as a temporary address. The chances are high that spammers will rapidly get hold of your public address – especially if it is frequently being used on the Internet.
Consider using multiple public addresses. That way you’ll have a better chance of tracing which services may be selling your address to spammers.

NEVER respond to any spam
Spammers verify receipt and log responses as a way to expand their lists. The more you respond, the more spam you’re likely to receive.
Think before you click ‘unsubscribe’
Spammers send fake unsubscribe letters, in an attempt to collect active email addresses. If you click ‘unsubscribe’ in one of these letters, it may simply increase the amount of spam you receive. Do not click on ‘unsubscribe’ links in emails that come from unknown sources.
Make sure your browser updated
Always keep your web browser updated and that all of the latest Internet
Use anti-spam filters
Only use email providers that include spam filtering capabilities.
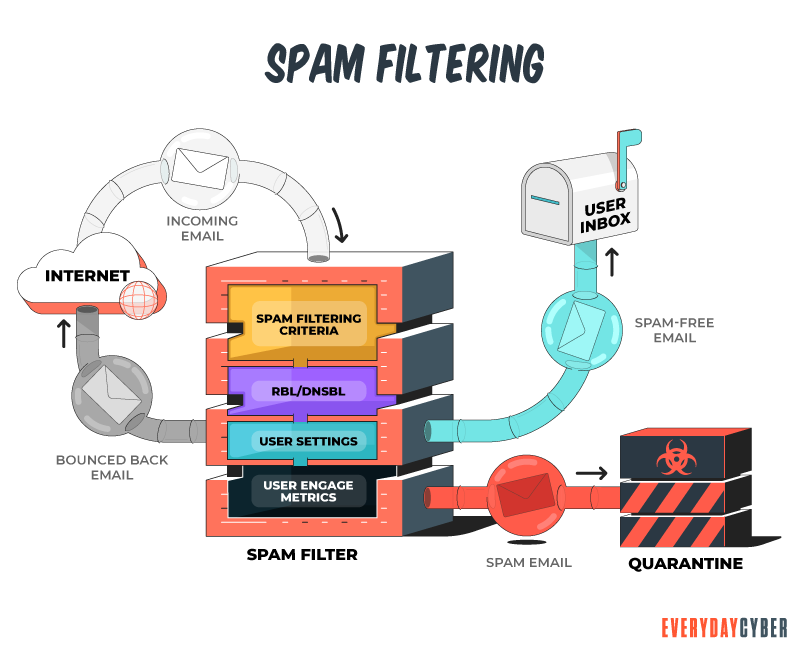
Use quality antivirus /antimalware tools
Quality antivirus/antimalware tools include advanced anti-spam features.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is a Hacker?
A hacker is someone who challenges technology to see if it can be compromised. A hacker can black hat or white hat.
What you should know about Chatbots And cybersecurity
Chatbots are conversational assistants that automate repetitive chores. We like them because they assist them in completing jobs swiftly and without the need for human interaction. But an unprotected chatbot can be a security problem. Hackers can use defenseless AI chatbots to carry out nefarious activities. Read to learn more.
What is a Back Door Threat?
In cybersecurity, a Back Door Threat enables a hacker to gain unauthorized access to a computer or digital device at any time.
What is 256 Bit Encryption?
256 bit encryption has quickly become the industry standard for ensuring security of your data, security of your communication and is really now minimum encryption level for securing your digital environment.
What is a Rogue Certificate?
A rogue certificate is a valid certificate issued by a legitimate certificate authority. However, it’s untrustworthy because either it was compromised or was issued to the wrong party.
What is Malvertising?
Malvertising is advertising malware that infects digital devices with malicious software using online ads and advertising networks as their delivery platforms.