If you don’t move quickly after losing your
When your
The expensive phones we carry with us at all times are easy targets for burglars. Cyber thieves are always on the lookout for them in subway cars or on coffee shop tables. Given how much we rely on our smartphones, losing or misplacing one might feel like the end of the world.
The Numbers Tell a Story
The true cost of a misplaced
A recent study done by Kensington reveal the following:
- Every year, 70 million smartphones are lost, with just 7% being found.
- 52% of
mobile devices are lost at work, while 24% are stolen at conferences.
The Mobile Theft and Loss Report – 2021/2021 Edition done by Prey Project also found that the majority of lost devices were misplaced.
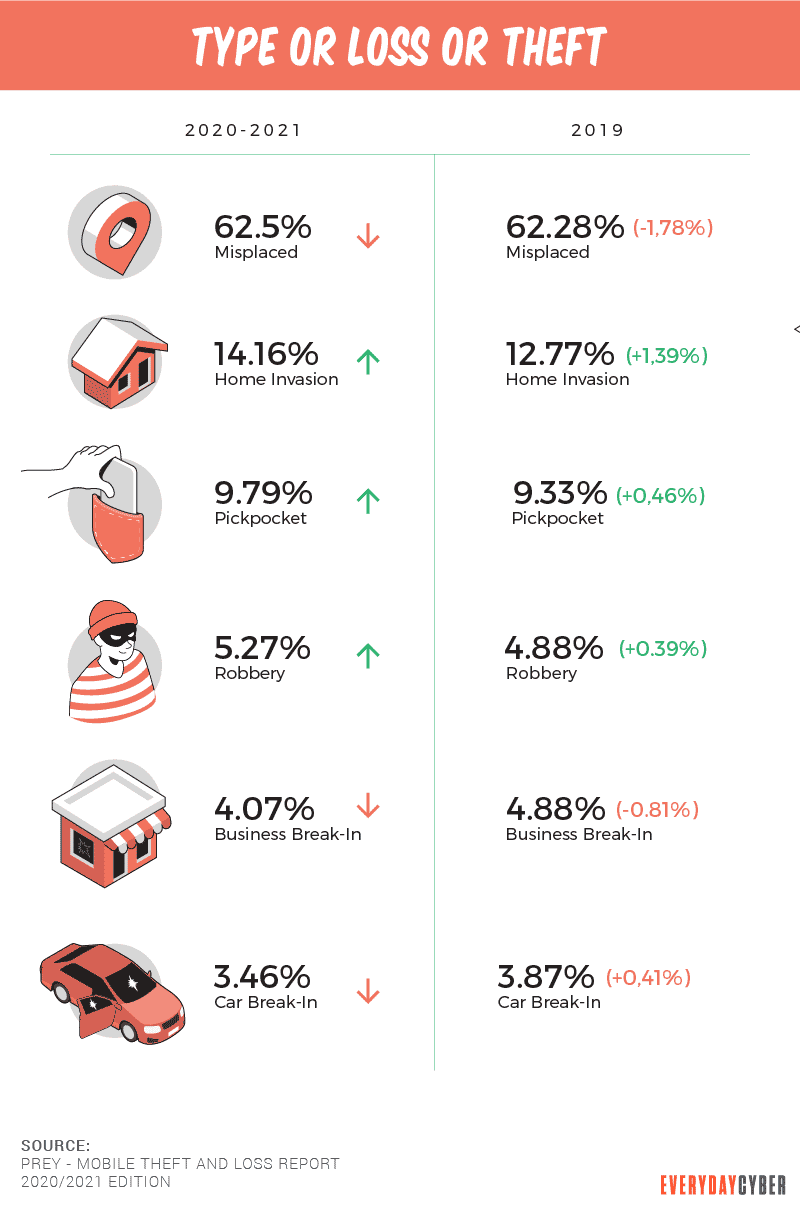
Most losses happen in private places like homes and private cars.
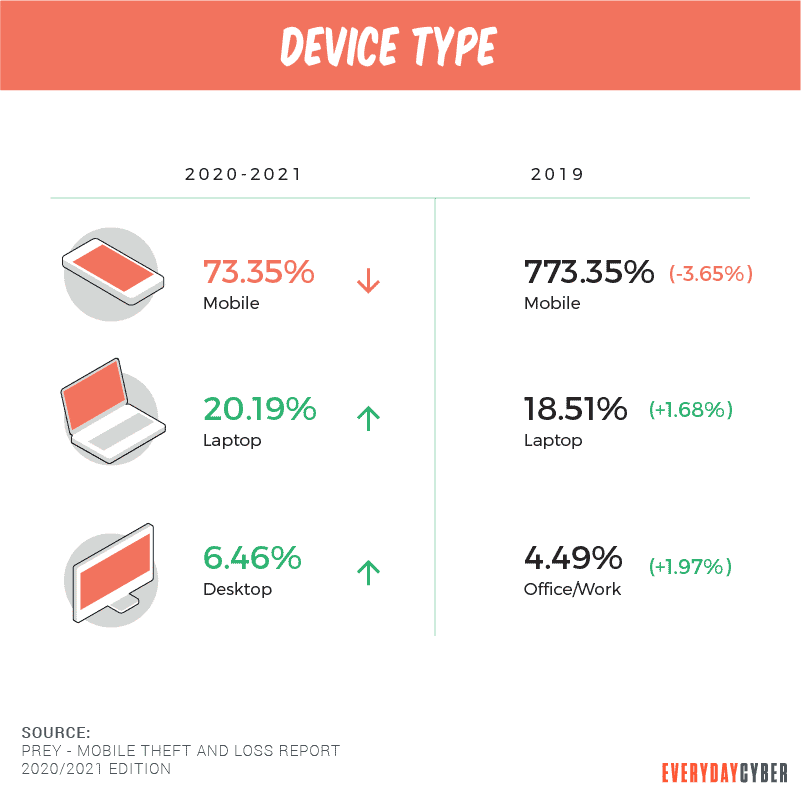
Most frequently stolen devices were mobile.
It’s no laughing stock that tens of millions of mobile phones are lost every year. What about those that were not reported? They could add up to tens of millions more.
What Thieves Can Do with Your Stolen Phone
A
Sell your phone as whole or parts of it
Some thieves are able to manage the password of stolen phones to factory-reset with the help of social engineering. They could then sell the
If the goal was simply to steal a
Steal money
For unlocked phones, such as one snatched physically by a thief from the owner or found unattended and a bank app is open, the
Some banks allow customers to send money electronically. This makes it considerably easy to steal money because any verification codes will be delivered to the stolen
Use personal information for extortion or blackmail
If thieves discover sensitive documents on your smartphone, they may demand a ransom. They may even threaten to delete or forward your messages to your contacts. They can do the same for personal files that could compromise you or someone else.
A thief can also try to breach your Facebook or Instagram accounts and start asking your friends and acquaintances for money.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
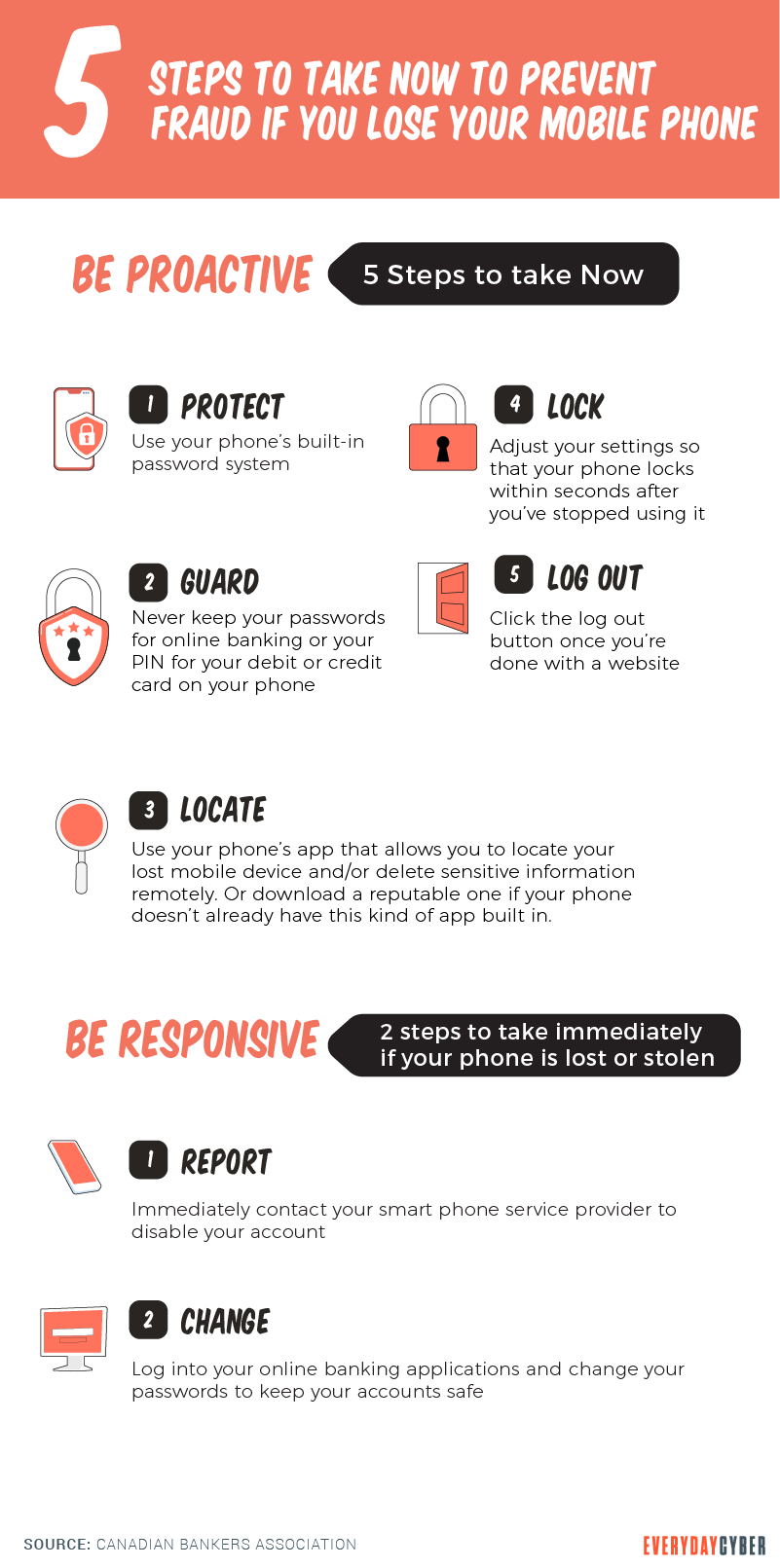
What to Do If your Phone is Lost or Stolen
If you’ve lost your
After the loss or theft of your
Be very suspicious of all texts and calls related to a stolen
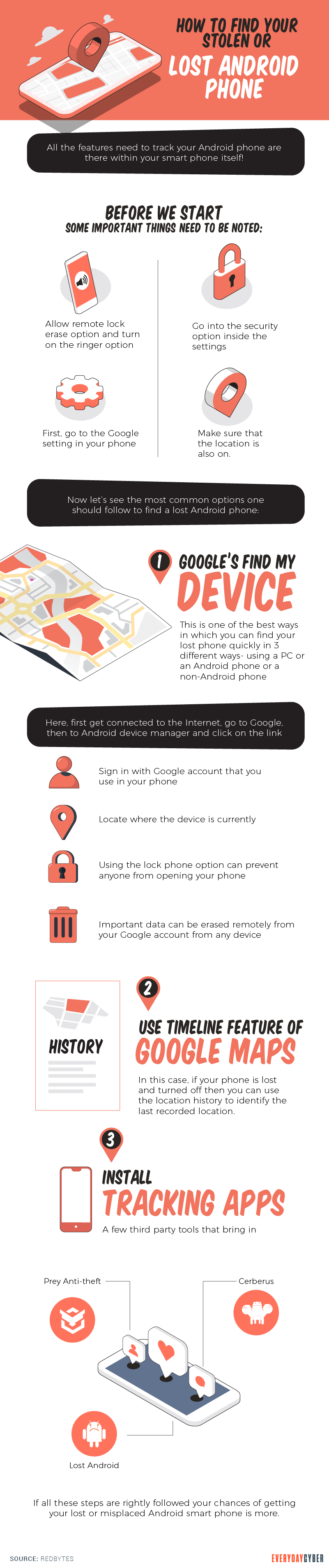
Try to track your phone
If you plan to locate your
Using an alternate
If the
On Android, Find My Device can display a Google Map with your device’s precise GPS position.
On iOS, type Find My
On Apple, the Find My iPhone function allows you to track the position of your iPhone. For this to work you must have location services turned on and access to your iCloud account from a computer.
What to do if recovery of your phone is impossible
If your
1. Call your carrier
Your initial call should be to your service provider. Tell the customer (Image service representative that you’ve misplaced your SIM card and that you’d like it blocked. The thief will be unable to impersonate you once the SIM card has been disabled.
1. Block your phone
To block your stolen smartphone, you’ll need Internet connectivity. Do it on a secure device because you’ll be inputting your password.
Log in to your Google or Apple ID account. Find your missing
Keep an eye out for phishing emails and
3. Lock and/or wipe your phone remotely
If you’re sure your
For
For iOS phones: Go to icloud.com/find and select the Find My iPhone function. Follow the instructions on the screen to set the lock and erase data.
4. Block your phone ’s IMEI number
IMEI stands for International Mobile Equipment
Even with a different SIM card, the stolen
Call your carrier and give the IMEI number of your lost
If you use Android, go to Find My Device and click on the encircled “i” next to the image of your
If you use an iPhone, go to appleid.apple.com feature. Sign in with the Apple ID used on your stolen
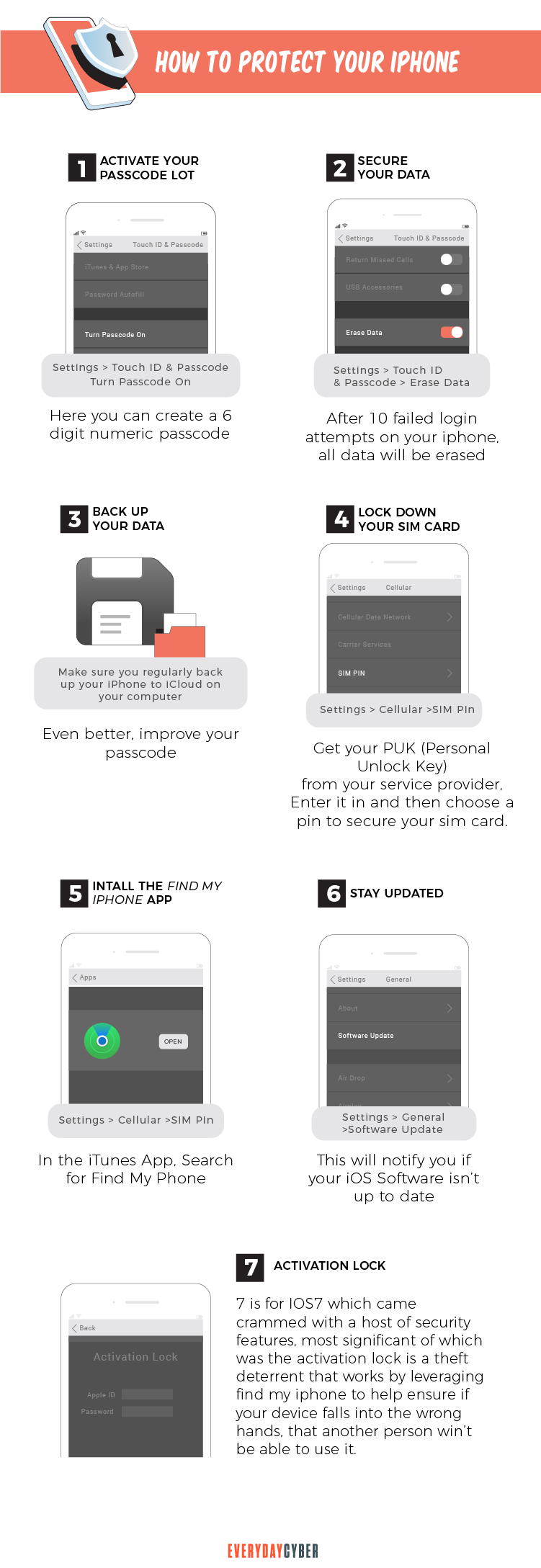
5. Change passwords
To avoid unauthorized access and use, change the passwords for all the critical services you use on your smartphone, such as email, online banking, shopping applications, and
Also consider checking your other accounts and apps to make sure no one is accessing them without your consent. If there is any strange activity or you recognize your stolen
6. Alert your bank
You should contact your bank to inform them that your
In the days and weeks after your
7. Restore your data
You will be able to restore any information, including text messages, on your new smartphone if you enabled backup on the device when it was still in your possession. You can find the steps to do this for
8. Go to the police
File a police report about your stolen or missing
Our final thoughts. In the event that you misplace or lose your
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is Digital Identity?
Your digital identity is your set of unique features and characteristics identifiable to you. It is all data that can be traced back to you.
What to do if your email Is hacked
Identity theft and bank account or credit card fraud are both possible consequences of a stolen email. If you suspect that your email has been hacked, act quickly to limit the harm. Here are 9 steps to take back control of your email if you have been hacked.
What is Catfishing?
Catfishing is a deceptive technique individuals or criminal entities use to create a fictional personas or fake identities online and use them to scam unwitting victims.
What is Malvertising?
Malvertising is advertising malware that infects digital devices with malicious software using online ads and advertising networks as their delivery platforms.
10 Cybersecurity Trends for Small Businesses in 2022
Knowing the latest cybersecurity trends spells the difference between keeping your business safe and opening it up to cyber attackers.
What is a Password Manager?
A password manager is an encrypted storage system for keeping and managing passwords usually protected by a master password. Some password managers use biometric data to protect the vaults instead of master passwords. Still others support the use of two factor authentication for higher security.


