Cybersecurity is becoming a daily problem for small business owners. This makes the global cybercrime situation critical.
According to recent
Are you one of the many small businesses who believe they are immune to cyber-attacks?
Disturbing cybersecurity statistics and trends in 2021
Let’s take a look at some alarming statistics put together by Varonis, a data
- Human error caused 95% of cybersecurity breaches
Human error refers to the intentional or unintentional actions by employees that cause, spread, or allow a
This covers a wide range of behaviors, from opening a malware-infected attachment to forgetting to use strong passwords.
Employees use an increasing number of tools and services in their demanding work environments. They have usernames, passwords, and other information to remember. When employees aren’t given more secure options, they begin to take shortcuts to make their lives simpler.
- The average cost of a data breach in 2020 was $3.86 million
The rising frequency of successful cyber attack attempts implies that the quantity and severity of
Data breaches disclose sensitive information, putting exposed individuals in danger of
More significantly, data breaches are costly especially for small businesses. They can impact their financial resources and bottom line.
- Phishing is the most common attack technique
Phishing attacks involve hundreds of millions of individuals and organizations every day. They include:
-
- Email phishing
- Whaling
- Spear Phishing, Smishing, and vishing
- Angler phishing, and more
Viruses, malware, distributed denial of service (DDoS) attacks and many more threats are overwhelming our digital world. Small business leaders can’t ignore the trends if they want their businesses to survive. And the best line of defense against these threats is a robust cyber
What is a Cybersecurity Strategy?
A cyber
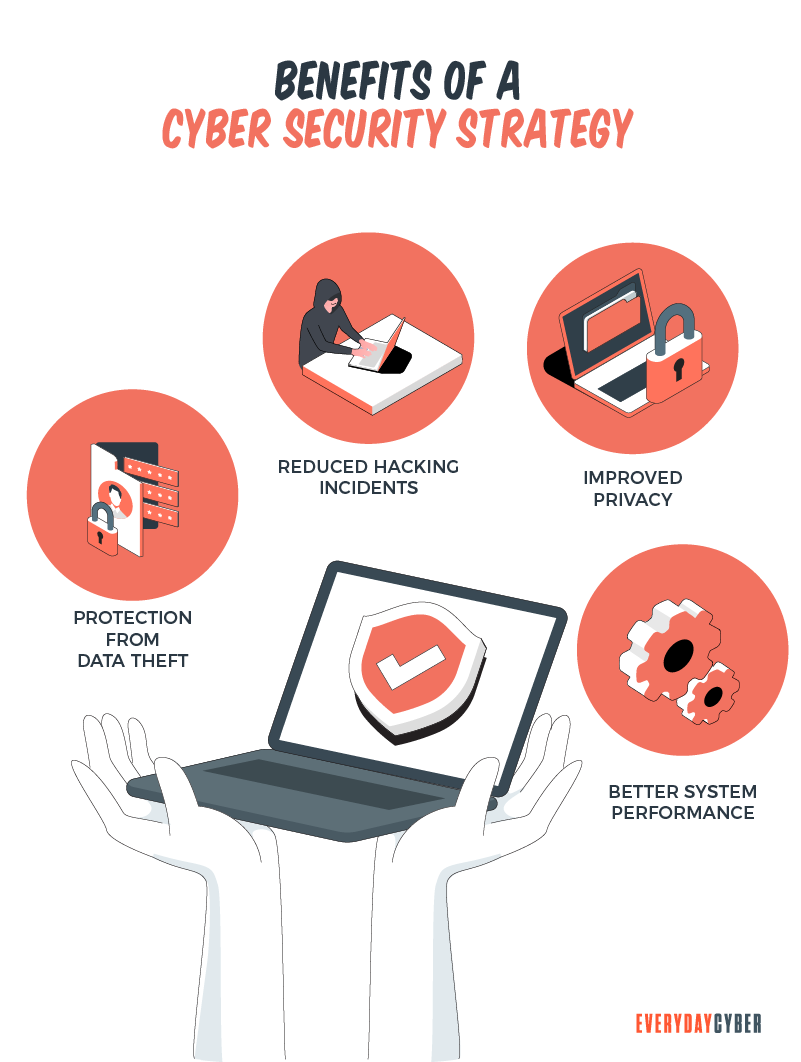
The cyber
A cyber
Do Small and Medium Businesses Need a Cybersecurity Plan?
Definitely, and they should take cyber
The statistics
The statistics make it clear all businesses need a solid cyber
The ever evolving threats
A cyber
1. Phishing
Phishing is a type of social engineering attack that has evolved into one of the most popular and dangerous cybersecurity threats today.
Phishing occurs when a hacker creates a false
What is it about phishing that makes it so popular today? Email, text messaging, instant messaging, and social media profiles are easy vectors that criminals can exploit.
What are some of the most popular phishing techniques?
One of the most prevalent phishing scams uses email to target victims. An attacker sends you an email that appears to originate from your local bank or the government. It asks you to go to a website and enter your username and password.
Another typical strategy is making a false social media account that looks like a friend or family member. The hacker then uses texting to request money or data, making it appear as though it is a family member or acquaintance asking for a favor.
What are some of the most typical phishing warning signs?
- Use of generic terms like “Sir” or “Madame”
- Incorrect grammar or language, or punctuation errors
- A strange sense of urgency
- Requests for sensitive information that are out of the ordinary
2. Malware
Malware is a broad term. It refers to any malicious software that is meant to cause harm to a computer system.
Viruses, worms, or trojans can infect computers. They can steal, delete, or encrypt data, monitor a user’s activity, or hijack essential computing processes.
Worms, viruses, Trojan horses, and spyware are examples of common malware.
Viruses can also encrypt or erase data. They change or hijack core computer functionality, or follows a user’s behavior without their knowledge.
Physical hard disks, USB external drives, and internet downloads are all frequent ways for viruses to spread.
3. Ransomware
Ransomware enables a hacker to encrypt the victim’s computer files and hold them for ransom. Before the hijacked information and system are unlocked, the victim is usually required to make a ransom.
Ransomware is spread by phishing emails or by accessing an infected website without realizing it. Ransomware is destructive since it is difficult to restore information that has been encrypted.
While some victims choose to pay the ransom, there is no guarantee that the hacker would return the victim’s computer content.
4. Social engineering attacks
Social engineering happens when a hacker tricks someone to give them information or access to software. Hackers aim to persuade users to disregard common safety protocols.
What makes social engineering so successful? Social engineering attacks usually target a person’s emotions.
One of the most prevalent deception techniques is convincing someone that they are assisting someone in need. For example, an attacker could impersonate a coworker or a family member and request access to a document, bank account, or sensitive information.
Hackers want something from you
Small and medium businesses don’t have the deep pockets that enterprises do. They have inadequate resources to protect themselves from cyber threats.
This is the very reason why they are easy targets for hackers. Small packets of information, when piled up, are still valuable to cyber criminals. Here are what they want from you:
Valuable information
Criminals realize that even small businesses have a lot of information they can sell on the Dark Web for a profit. Medical records, credit card numbers, Social
Cybercriminals are constantly looking for new ways to steal this information. They either use it to get access to bank accounts and make fraudulent purchases, or they sell it to other criminals.
Computing power
Sometimes cyber criminals are just interested in taking over a company’s computers and turning them into a bot army to launch large DDoS attacks.
DDoS disrupts service to businesses by generating massive amounts of artificial traffic. The hijacked bots contribute to disruptive traffic.
Money
Cybercriminals target both small and large businesses for financial gain. This explains why ransomware is such a popular attack tactic. It frequently succeeds, resulting in revenue for the attackers. Bad actors will continue to use attack tactics that deliver them the money.
A way to the big enterprises
Today’s businesses are digitally connected to each other. They share information, manage supply chain processes, and complete transactions.
Since larger organizations are tougher to penetrate, attackers target small businesses as a way to get into the systems of large corporations.
Regulatory Requirement
Businesses will pay fines If they are found to have breached information or have failed to comply with requirements such as HIPAA, PCI, SOX, GBLA, or GDPR.
Platforms for storing information in the cloud and machines have expanded as a result of the current growth of firms processing data. As a result, the areas of vulnerabilities have also grown.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
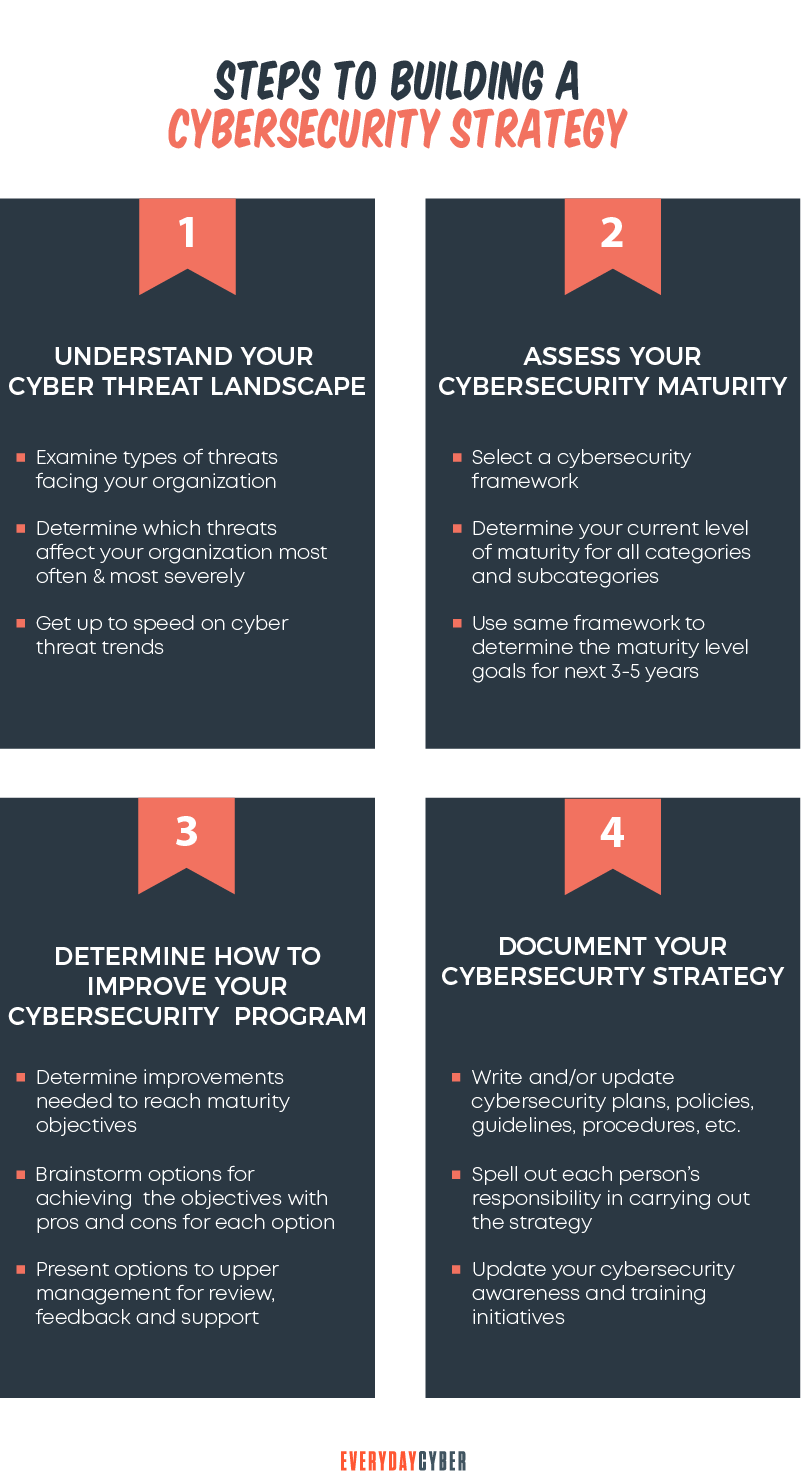
Preparing for Your Cybersecurity Blueprint
Each organization’s needs are unique. Therefore, there’s no standardized solution when developing a cyber

Here are critical steps to take to get you prepared:
1. Perform a security risk analysis
Organizations do an IT enterprise risk assessment to examine, identify, and modify their overall
A thorough enterprise
It is difficult to prioritize and distribute resources where they are most required without first valuing the many forms of data in the company.
To effectively estimate risk, management must first identify the most valuable information sources to the organization, including the storage locations and vulnerabilities connected with them.
2. Determine your security objectives
A crucial component of a cyber
Set reasonable expectations on:
- Assets such as infrastructure, mechanics and people
- Timetable
- Budget
- People
3. Appraise your technology
Examine your network equipment and applications to see if they comply with
In going through this step, find out what tools are currently used. Know if there are enough qualified people to handle them.
4. Educate employees in security principles
To protect critical corporate information, provide cybersecurity training to key personnel. Establish fundamental
Implementing Your Cybersecurity Strategy
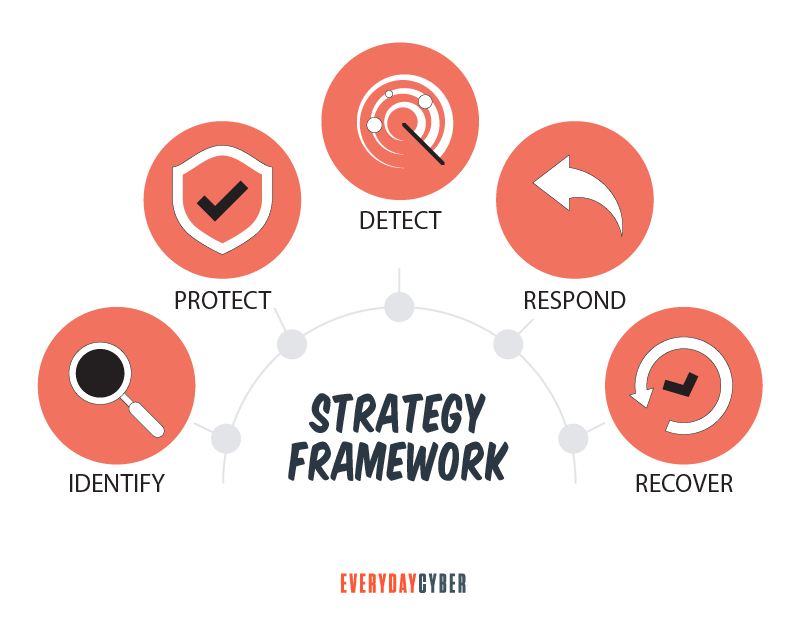
Now you’re ready to implement your
Suggested frameworks:
- Center for Internet
Security (CIS) - International Organizations for Standardization (ISO)
- National Institute of Standards and Technology (NIST) as their framework (NIST)
Cybersecurity basic best practices
During the implementation period, remember to carry out basic
- Update
antivirus and anti-malware software on every device - Protect your Internet connection with a firewall
- Update your operating systems and applications
- Back up all critical data
- Limit access to computers and data to authorized users
- Require all users to have strong passwords and change passwords regularly
- Enforce multi factor authentication
- Patch software vulnerabilities
- Implement endpoint
security - Conduct regular cybersecurity training for your employees
Evaluating Your company’s execution performance
The team must assess the company’s capacity to carry out the plan objectively. They may need to hire third-party expertise or outsource additional tools if they lack the resources to start the approach. Managers must examine potential hiccups, disruptions, and dangers to their plan along the way.
Our final thoughts. We’ve seen cyber attacks affect even the world’s largest companies. That’s why it’s critical for small businesses to implement a customized
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is DNS Hijacking?
DNS hijacking is no laughing matter. It is a serious security threat that is consuming the cyber world. The critical role of DNS for network security has made a primary target for facilitating mass data theft.
A 10 Step Plan for Small Business Cyber Security
An effective cyber security plan outlines in simple language the best cybersecurity practices your organization needs to stay safe. It doesn't have to be complicated, but it should be pragmatic.
What is a Botnet and How to Protect Your Business from One?
A botnet is a network of computers that work as a collective to infiltrate your device. Here's how to protect your business from botnets.
How to Build a Cyber Security Awareness Program for Your SMB Business
Building a cyber security awareness culture should be a top priority for your organization. Every manager, department, and individual in your firm must commit to this on a long-term basis.
What is a Computer Virus?
What's a computer virus? We hear about it all the time but do you really know what it is and how to prevent one?
What to do if your phone is lost or stolen
When your phone is lost or stolen, it is more than just a pricey handheld that is lost. Our phones keep track of our lives. If you’ve lost your phone, there are things you can do to track, locate, and recover it depending on the type of phone you have. Read this to get tips on how.

