A botnet is a robot or robotic network of computers or other intelligent devices that operate as a collective. They deploy and execute malware in a coordinated and large-scale fashion. Many of the worst cybersecurity attacks are through the use of botnets. These attacks target individual consumers, businesses, and governments .
In many ways, major cybersecurity attacks wouldn’t be possible if it weren’t for botnets that coordinate and execute them.
A botnet can consist of as few as five to 10 devices. Or it may scale to the thousands or even tens of thousands of devices. Botnets often grow and expand over time.
Botnets rely on two components to function. First, they need a botnet-infected network of devices. We call them zombies. These do the actual work. They infect servers, phones, and smart devices. The second component is the command-and-control center. They are sometimes referred to as the “bot herder”. This is the part that makes the zombies do something, like spread a virus. With these two components in place, the botnet is ready to cause chaos.
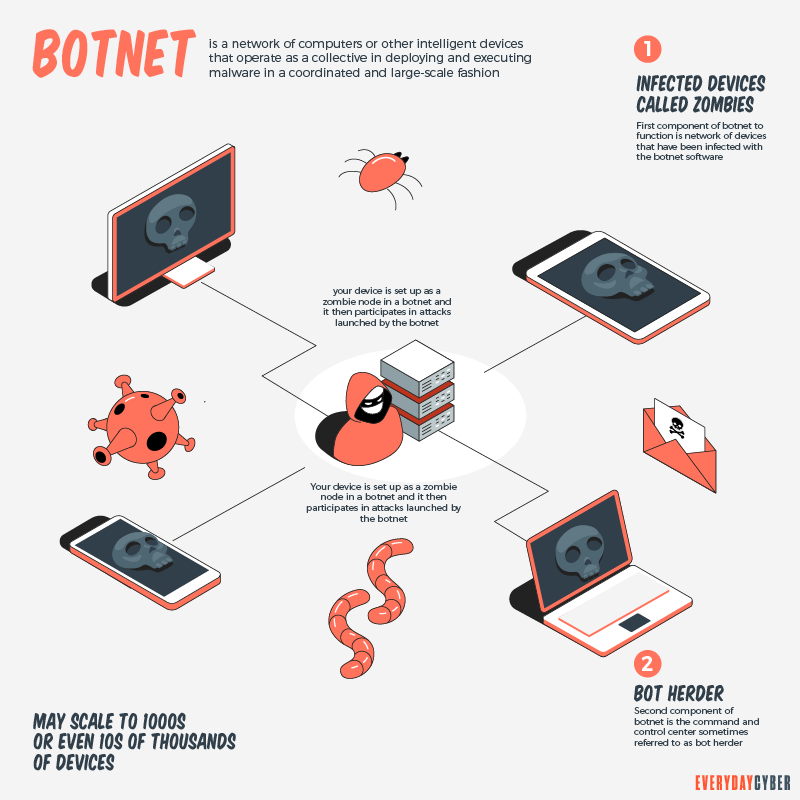
Botnets can affect you or your business in one of two ways. The first way is if you are a victim of a botnet-driven attack. For example, the botnet spreads a virus to your computer, your
So how does a botnet work?
Understanding the specific details of how various forms of botnets work is critical. This is to appreciate the damage and destruction they can cause.
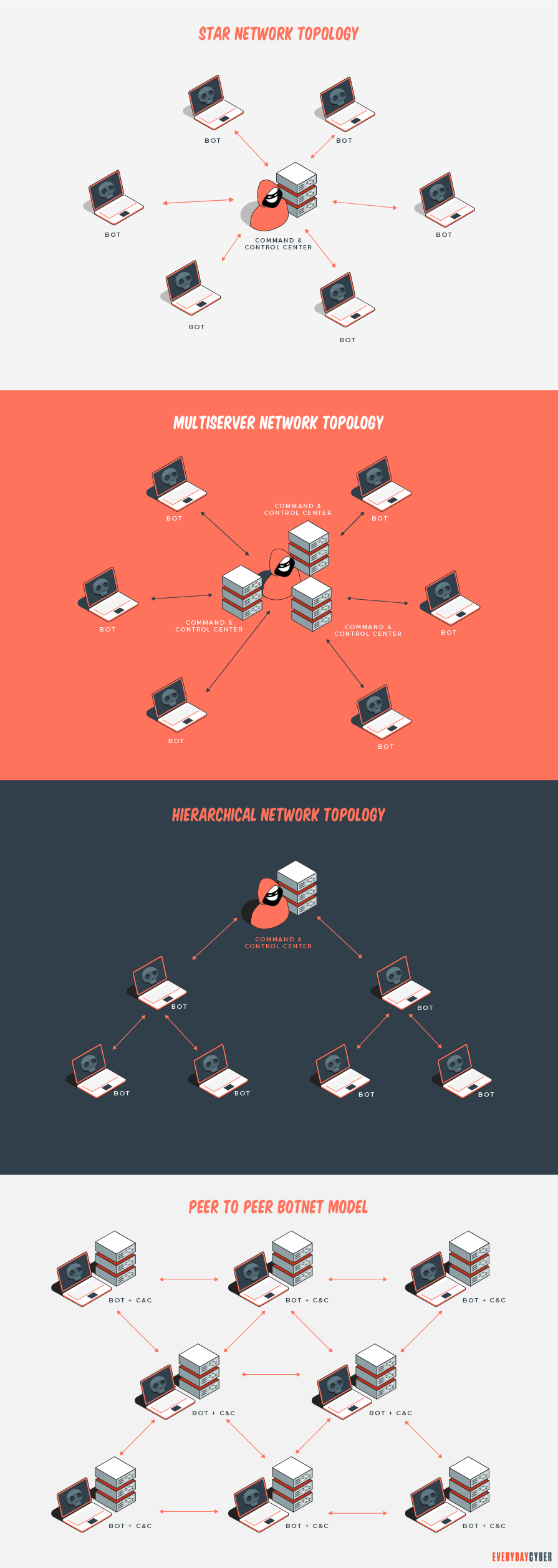
But, in general, botnets take two forms – client-server and peer-to-peer networks.
The client-server model is the original model used by many botnets. It uses the more typical command-and-control center approach described earlier. This model, while effective, is simpler to shut down. If you can shut down the command-and-control component, then the zombies become useless. The network is then taken down.
So, to counter this, bad actors deploy the peer-to-peer model. This model removes the single point of control. Each device in the botnet can communicate with other devices to pass command-and-control instructions. If any of the devices are down or unable to communicate, the devices left continue to operate.
Each infected device in the botnet takes direction via command-and-control authority (the hacker). It then performs whatever action the botnet devices are capable of doing, such as sending phishing emails, setting up malvertising, deploying trojan horses, spreading viruses, etc.
How is a botnet created?
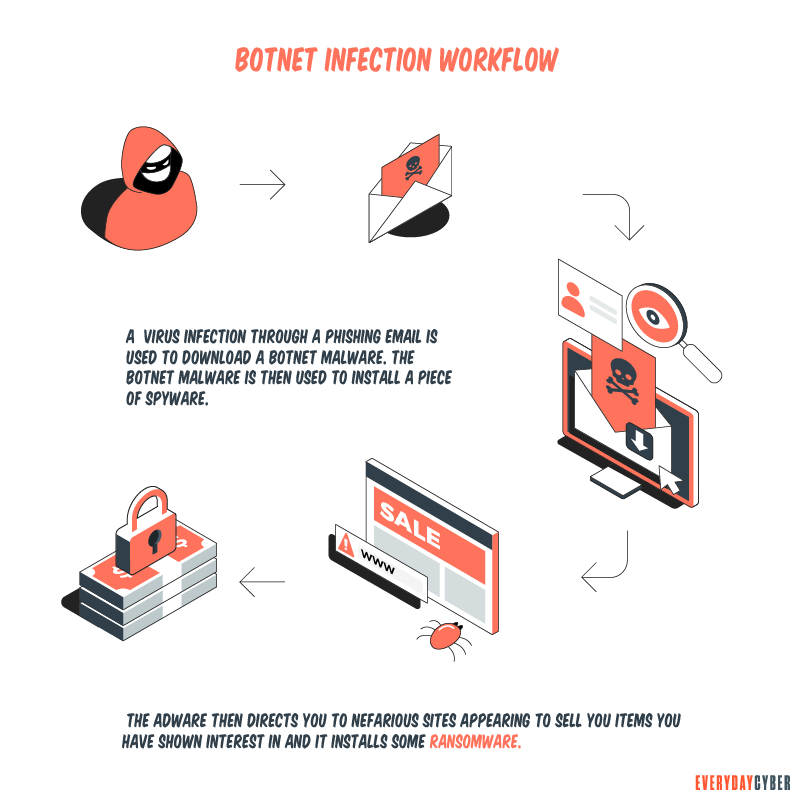
There are many different ways to create botnets. The most common is by downloading a botnet malware into a user’s device through a virus sent by a phishing email. Others use spyware to capture your online shopping patterns and then install adware. The adware will direct you to nefarious sites appearing to sell you items you have shown interest in. It then installs some ransomware, which causes more trouble.
It becomes one infinite, never-ending cycle that’s vicious and potentially costly.
The bottom line is there are many different ways to create botnets. There are also different ways botnet malware can get installed on your devices.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
What can a botnet do?
Evil doers use botnets for many different purposes. The example described above was illustrative. There are also other examples that are worth learning about.
Other examples of what a botnet does:
Massive phishing and spam email attacks. Sending millions of emails to unsuspecting recipients. Most of these are targeted at contacts the bot has accessed from the devices they are running on.
DDoS or denial of services attacks. The bots target a specific website or internet service. They then drown it with an overwhelming barrage of requests. This makes the website or internet service unusable. Your devices can be a part of this type of botnet. They are then the ones making the requests against the targeted sites.
Password farming. Gaining access to passwords to all types of applications, websites, or any online service. These apps that your device might communicate with are valuable to bad actors. Either they sell your passwords on the dark web or use them to access those services themselves for financial gain.
Bots automate the password-stealing business. It’s a scary thing when you have thousands or millions of bots doing this.
Crypto Mining. Mining is a more recent phenomenon. Bad actors aren’t looking to steal your information or threaten you at all. What they want is your computer’s processing power to mine cryptocurrencies. Mining crypto is about performing mathematical calculations. So millions of bots stealing your processing power can be very effective to mine crypto. This slows down your computer, wears it out faster, and costs you money in extra electricity.
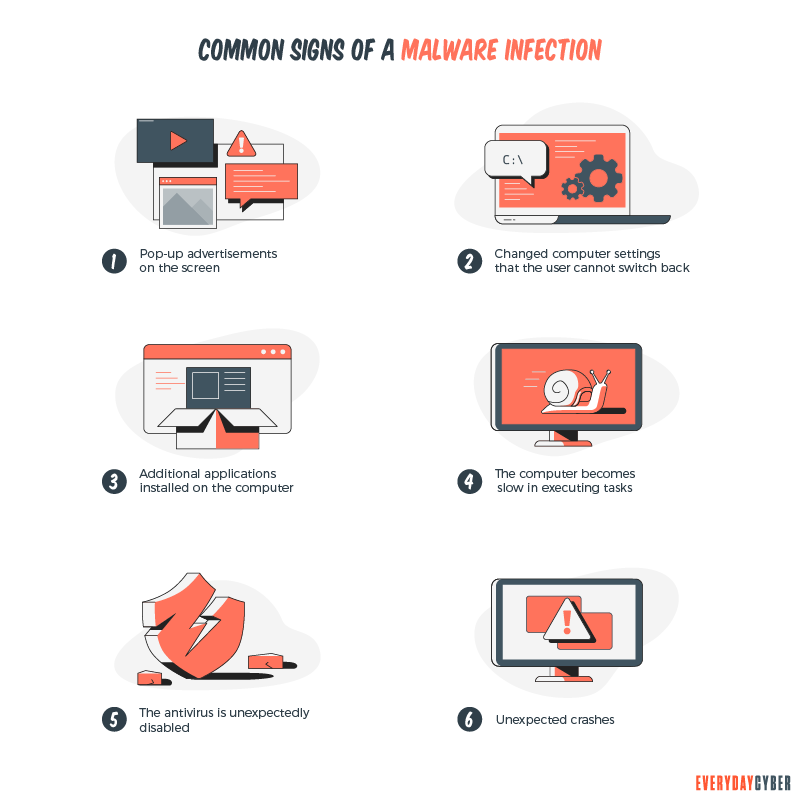
Booting botnets to the curb
How botnets get onto devices is no different from most other forms of malware. Knowing the best defense against becoming a bot or zombie in a botnet is crucial. It is the same as defending against all other forms of malware.
- Don’t click on links you aren’t 100% sure of.
- Don’t download anything you don’t trust.
- Assume all emails are potential phishing emails. Confirm the trustworthiness of any links before clicking.
- Install tools like
antivirus andantimalware on your device.
The first rule of good cybersecurity and digital protection is to apply common sense. “Check twice, click once”.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is AD tracking?
Digital and online ad tracking is the process of gathering data and insights about the performance of online advertising campaigns. Digital systems use methods like cookies, unique tracking URLs, tracking pixels, and other tools
What is Catfishing?
Catfishing is a deceptive technique individuals or criminal entities use to create a fictional personas or fake identities online and use them to scam unwitting victims.
7 ways to secure your home office
People working from home perform most of their tasks online. They are now more exposed to cyber attacks than ever before. Cyber criminals see a great opportunity in the massive growth in working from home and the vulnerabilities of home office security.
12 Ways to Help Older Adults Stay Safe Online These Days
Seniors, like everyone else, have special vulnerabilities in addition to the common Internet risks. They have specific characteristics that make them vulnerable online, particularly to online fraud. Isolation and lockdowns caused by the pandemic have forced seniors to embrace technology like never before. Here are 12 ways to key seniors safe online.
A 10 Step Plan for Small Business Cyber Security
An effective cyber security plan outlines in simple language the best cybersecurity practices your organization needs to stay safe. It doesn't have to be complicated, but it should be pragmatic.
What is an Ad Blocker?
An Ad Blocker is an app or browser extension that stops ads (popup, banner, inline) from displaying on your desktop or mobile device.


