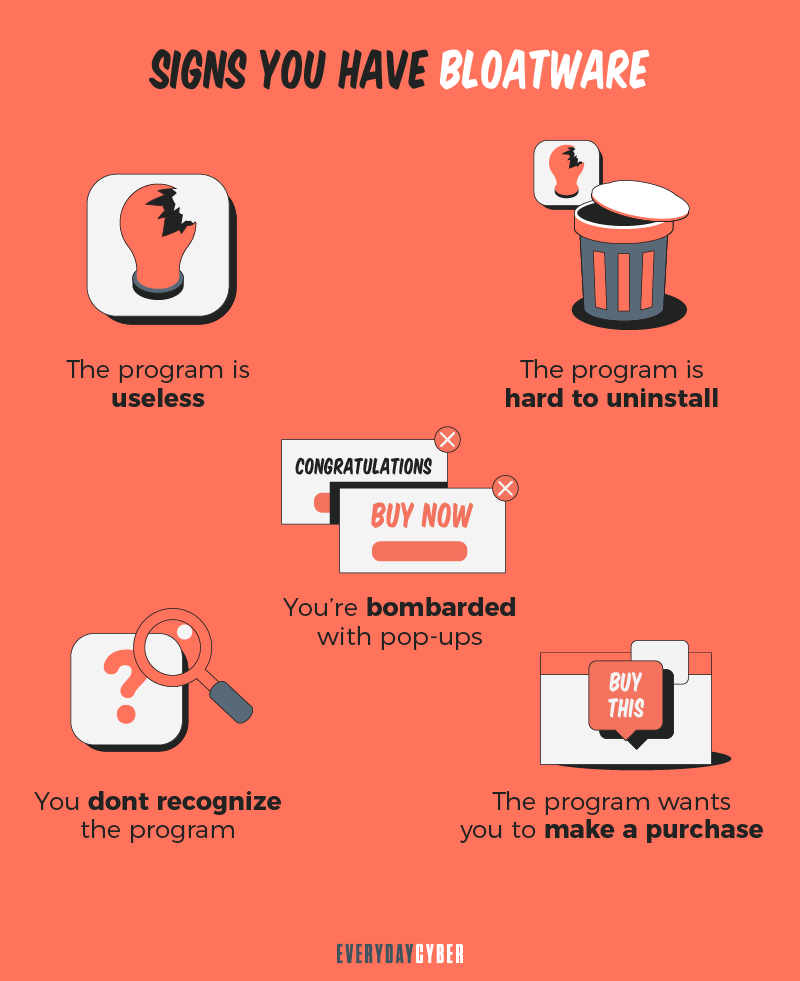
Bloatware on computers and other digital devices is similar to junk mail stuffed into your home mailboxes: unwanted and ignored until there’s just too much of it.
“Bloatware” has become the term that describes many different types of applications with one common trait: they’re unnecessary. They can also expose you to a bunch of cybersecurity risks. If the bloatware connects to the internet, it exposes your device to malware by introducing a host of apps designed to exploit your computing power and personal information, including financial information.
Examples of bloatware include:
- Toolbars: Many of these applications install additional toolbars that clutter up your browser, show you annoying ads, and are not particularly useful.
- Adware: These applications have no other purpose than to serve you ads. Adware can also include annoying shortcuts to commercial websites that are placed on your desktop.
- Trials: Try-before-you-buy versions of apps you probably do not need, don’t want, and didn’t ask for.
Pre-installed Bloatware
Software companies pay device manufacturers and distributors to install demonstration versions of their products onto devices, hoping customers will buy the full versions.
Unless you actively search for and delete demonstration software — and we rarely do — these programs remain on your devices and become part of a growing mound of bloatware. Gradually sucking all of your device’s processing power and grinding it to a halt. Opening even small apps on overloaded storage becomes a total pain.
How to get rid of Bloatware
There are free tools that can help get rid of bloatware. Some that are available include:
These tools use crowdsourcing information to recommend which apps users might want to keep on their devices and those to get rid of it.

Quality Antivirus/Antimalware solutions can also detect adware and malware and alert you to its presence on your devices. Users are then typically given the choice of removing the app or quarantining them to prevent interaction with the system.
Unfortunately, bloatware isn’t going away anytime soon so it’s important to be aware of the threat and how to manage it.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is an Ad Blocker?
An Ad Blocker is an app or browser extension that stops ads (popup, banner, inline) from displaying on your desktop or mobile device.
What is Ransomware?
Ransomware is particularly vicious malware that infects your digital device, encrypting your data and then holding you hostage until you pay a ransom.
What is a Website Security Certificate?
A website security certificate is a digital certificate that asserts the identity of a website. It’s a virtual file approved by an industry-trusted third-party called a certificate authority (CA)
What is a Remote Access Trojan (RAT)?
A remote access Trojan is a software used by hackers to gain unauthorized access and remote control on a user’s computer or mobile device, including mouse and keyboard manipulation.
What is a Back Door Threat?
In cybersecurity, a Back Door Threat enables a hacker to gain unauthorized access to a computer or digital device at any time.
What is Spear Phishing?
Spear phishing is a targeted cyberattack to steal your information. You should be aware of the dangers of this and how to address them.

