Malware or “malicious software” is a cybersecurity term used to describe all types of software that steals data, spies on you, damages devices and generally causes chaos and destruction.
Malware comes in many forms – viruses, spyware, ransomware, trojan horses, and more. It is created by a team of hackers who are looking to make money by spreading it themselves or selling the malware they created to the highest bidder on the dark web so they can do it instead. In all cases, if it lands on your devices, no good will come of it.
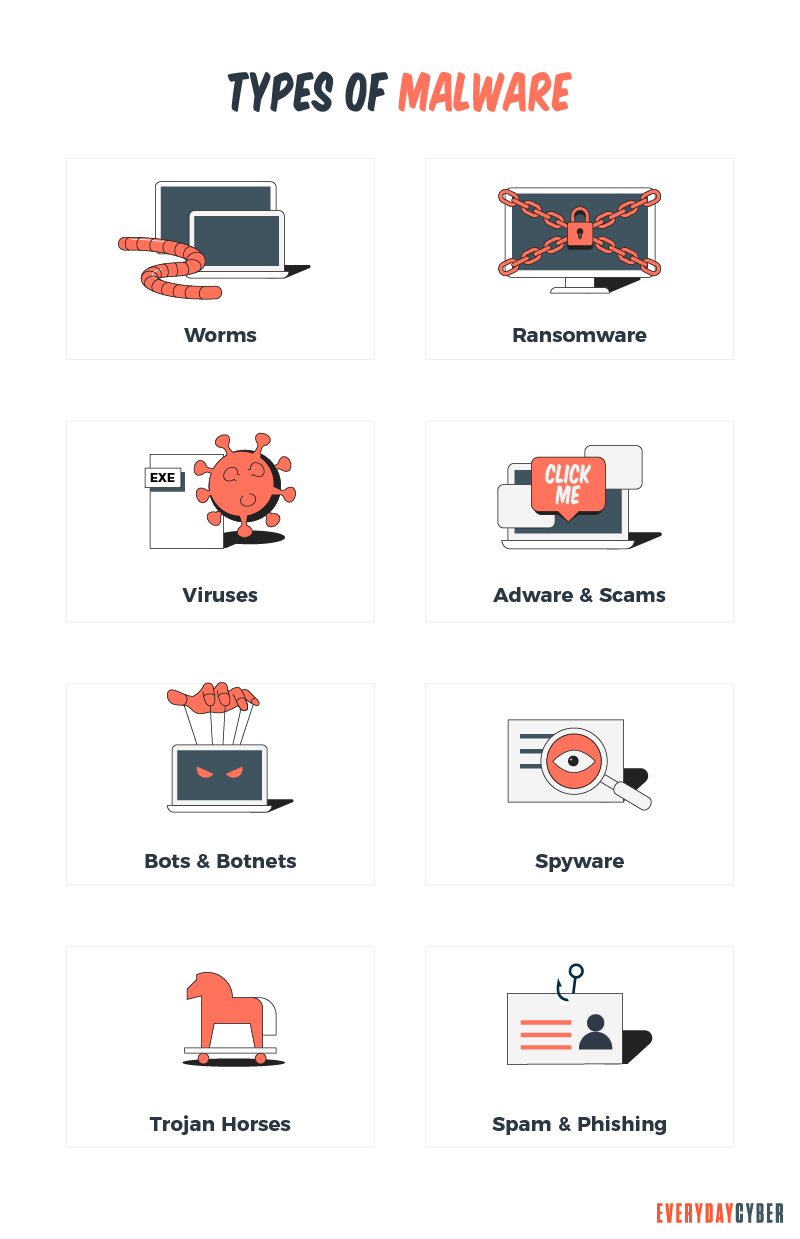
So what can Malware do?
Unfortunately, the answer is many things, and they are not good. Because the term malware covers a very wide and deep group, the things and particularly the bad things it can do are just as deep and wide.
The most common forms of malware are – viruses, spyware, ransomware, adware, trojan horses, worms, and botnets. But there are numerous variations of these, and in a lot of cases, they work together.
- Computer viruses mimic their biological cousins by replicating themselves from device to device and also causing all kinds of havoc on the devices that they have infected.
- Spyware is generally designed to hide in the background and steal your data – passwords,
security codes, internet browsing histories, pictures, listen on your microphone, watch you from your camera – nasty stuff. - Ransomware is probably one of the worst forms because it can lock down your computer and all its data, and unless you pay the ransom, you could lose everything.
- Adware is generally just annoying and likely not malicious but can slow down your device, constantly disrupt you with popups, and typically drive you bonkers.
- Trojan horses present themselves as part of legitimate software or apps. Unfortunately, they are really designed to do bad things once they are loaded and typically provide backdoors on your devices so that other malware – viruses, spyware, etc. can then be loaded undetected.
- Worms are like viruses but are designed to infect entire devices of devices as rapidly as possible. Particularly effective in infecting large groups of Internet of Things (IoT) devices (like smart speakers, digital assistance – Alexa, Siri).
- Botnets are networks comprised of many devices working together to cause mayhem. They are designed as a group and are used to launch massive attacks on devices, services, websites, businesses, and governments … all bad news.
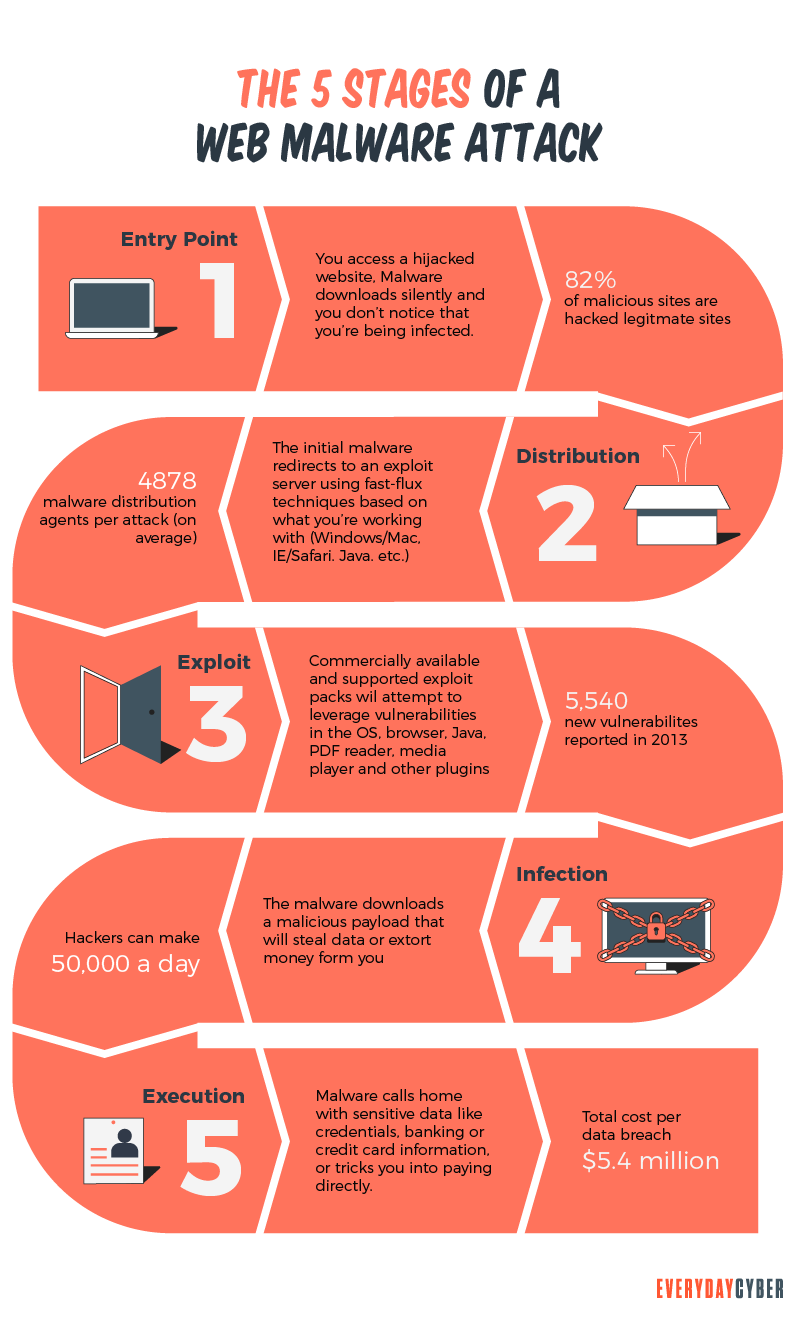
So how do I detect Malware do?
As we described before, Malware takes many forms. In some cases – like with ransomware and adware, you will know very quickly if you are a victim of either of these types of malware. Your computer will be locked and they will be asking for payment or you will be inundated with constant AD pop-ups. Viruses, Trojan horses, worms hide in dark places and hidden corners of your devices, making it much harder to detect. They are intentionally designed to be unnoticed so they can lurk and steal for extended periods. Generally, you need tools (antivirus,
There are worms and viruses – here again, you really need tools on your device to detect them but often their presence becomes apparent because of noticeable slowdowns of your device’s performance, files being deleted or replaced unexpectedly, or just weird behavior happening like unexpected device reboots, system freezes, etc.

Unfortunately, more often than not, the only way to detect these bad actors is to install antivirus/antimalware and similar tools that can detect, quarantine affected files/components of your device or prevent malware from ever infecting your devices to begin with.
Hackers and bad actors are everywhere, and they are constantly creating new types of malware to create chaos for you and me.
You will need to install defensive and proactive tools to combat this never-ending battle.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
So how do I protect myself?
Installing specialized tools like antivirus/antimalware onto your devices is the standard answer. You can also do things to minimize the likelihood that malware will get onto your devices. This includes:
- Be skeptical of everything online!! The biggest threat of having malware installed on your device is “social engineering”. The bad actors understand human behavior and use everything imaginable to lure unsuspecting victims through tantalizing offers via email, alerts, SMS messages, fake profiles, and all kinds of offer mechanisms to get you to click. And once you click that damage is probably done. Do NOT trust any link or file or document unless you are 100% sure it is from a trusted source. Do not CLICK if you don’t know.
- Triple check anything you are looking at downloading. Doesn’t matter if it’s a file, a document or an app. Like the previous item, don’t trust anything online at face value. Check, check and then check again before you download anything.
- Be careful where you browse. Malware is becoming more sophisticated every day and it is now possible for certain types of malware to cause your devices harm without actually downloading onto your device. Simply browsing to a website that is designed to execute, what is described as “drive-by” infection, can cause you harm. So be aware of every site you navigate to, search for information about the site before you go to it to. See if there is any information indicating that it could cause you damage. Be diligent, take a second before you go to a site you don’t know, it could save you a world of pain.
- Get an Ad-blocker. Malvertising is a particularly nefarious form of malware that presents itself as a popup ad or banner on a website. Bad actors use these as platforms for launching all kinds of malware simply by you hovering over the ad or banner. Get an ad-blocker it will save you a whole lot of pain.

Being diligent and even following the above to the letter still will not protect you from all the ways bad actors will try to infect your devices with malware. Inevitably you will still need to install defensive and proactive tools like antivirus/antimalware to create effective protection from the internet’s underbelly.
I am infected, how do I get rid of it?
Every form of malware has its own unique way of infecting your devices which means you will likely require specific tools or methods to remove it. It also depends on the device – desktop, mobile, smart device, etc. Check out our top tips for kicking viruses and other forms of malware off your devices.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is ATM Skimming and Ways to Protect Yourself
ATM skimming can lead you to losing all your money in your bank account. Here's how to protect yourself from it.
What is a Rogue Certificate?
A rogue certificate is a valid certificate issued by a legitimate certificate authority. However, it’s untrustworthy because either it was compromised or was issued to the wrong party.
What you should know about Chatbots And cybersecurity
Chatbots are conversational assistants that automate repetitive chores. We like them because they assist them in completing jobs swiftly and without the need for human interaction. But an unprotected chatbot can be a security problem. Hackers can use defenseless AI chatbots to carry out nefarious activities. Read to learn more.
A 10 Step Plan for Small Business Cyber Security
An effective cyber security plan outlines in simple language the best cybersecurity practices your organization needs to stay safe. It doesn't have to be complicated, but it should be pragmatic.
10 Cyber Security Stats Every Small Business Needs to Know
Knowing the right cyber security stats helps your business fight off and recover from cyber attacks. Get informed.
Why every small and medium business needs a cybersecurity strategy
A truck full of security studies show nearly every small businesses has exposed data and poor cybersecurity policies. Either build and execute a cybersecurity strategy or expect to be a victim of cyber crime. Be prepared, be proactive, and be safe.


