Encryption is a topic that can be a challenge to grasp. It generally isn’t a quick read as it does involve technical concepts. But we believe this article can help you get a good understanding of how it all works and particularly the value of using
So what is 256 bit encryption?
A
That definition isn’t as simple as it sounds. It’s the
A
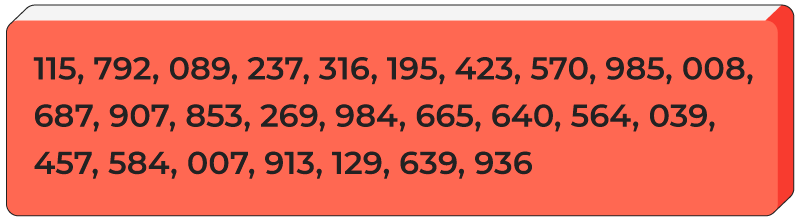
possible combinations.
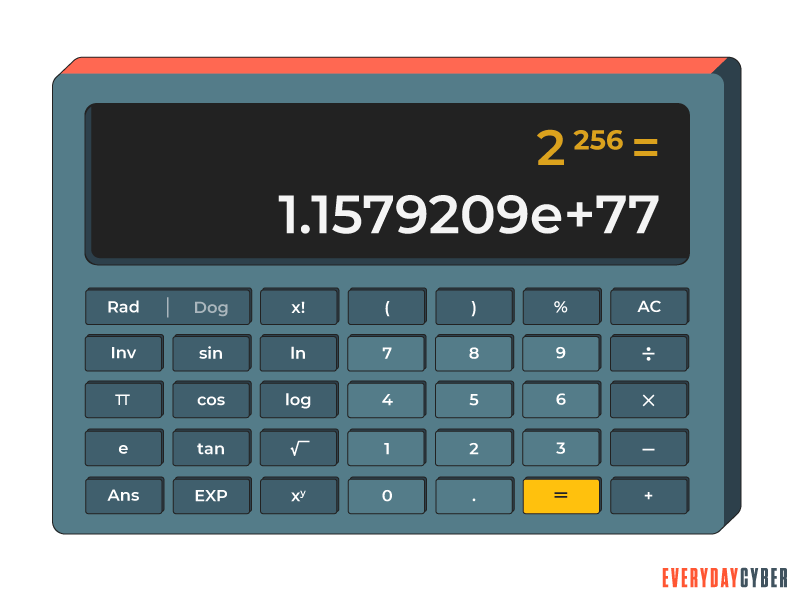
That’s 78 digits.
It will take millions of years to crack
When you factor in an RSA private key, the figure skyrockets even more. RSA derives its name from the names of its creators namely, Rivet, Shamir, and Adleman. According to DigiCert, cracking a 2048-bit RSA key with a standard computer would take 6.4 quadrillion years (6,400,000,000,000,000 years).

A brief review of encryption
You can see how dizzying the math could be. To better understand
First, we need to know the main terms involved in encryption.
Plaintext is encrypted data.
Ciphertext is encrypted data.
A bit is a blend of “binary digits” expressed in 1’s and 0’s. It’s a basic unit of information. The number of bits determines the length of the encryption key.
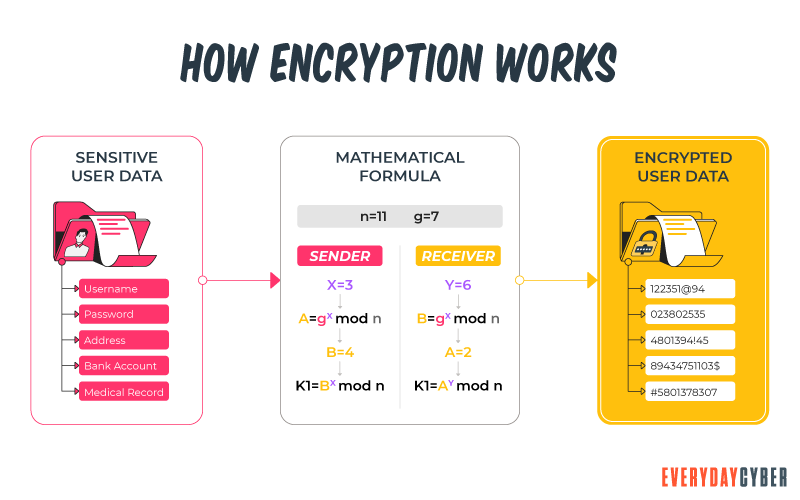
An encryption key is a random string of bits created for scrambling and unscrambling data. It performs algorithmic functions to create a piece of ciphertext. It’s used to encrypt, decrypt, or carry out both functions, based on the type of encryption used. The longer the key, the harder it is to crack the encryption code.
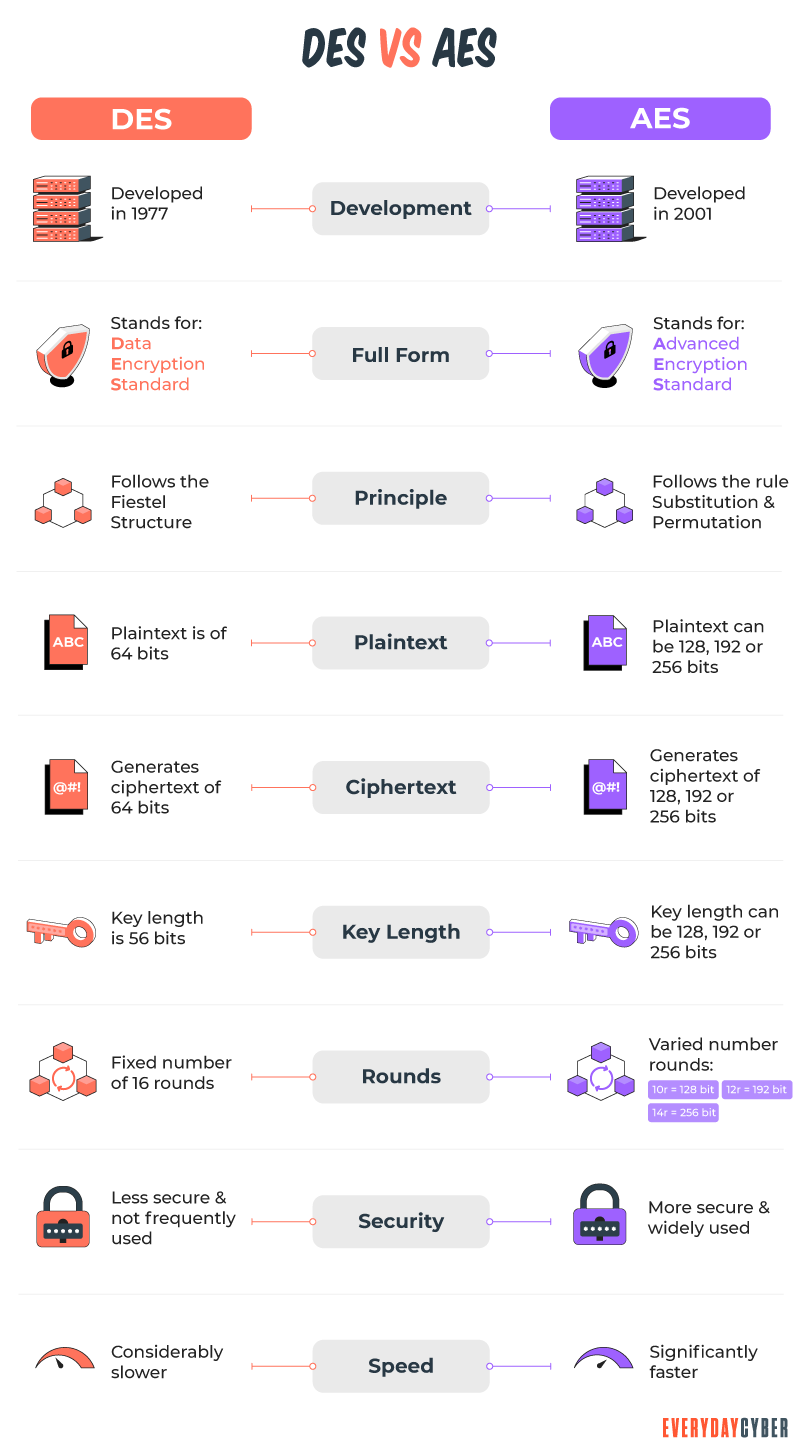
Key length, key size, or key space refers to the number of bits in a key. The AES uses key lengths of 128, 192, and
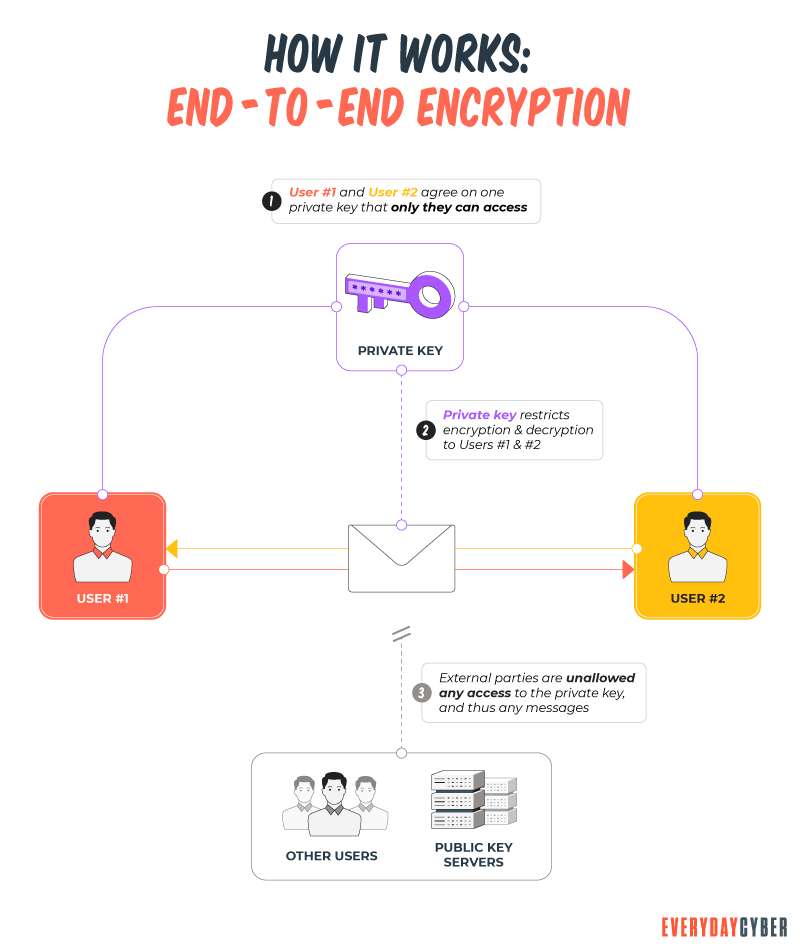
Symmetric encryption uses one key to encrypt and decrypt information.
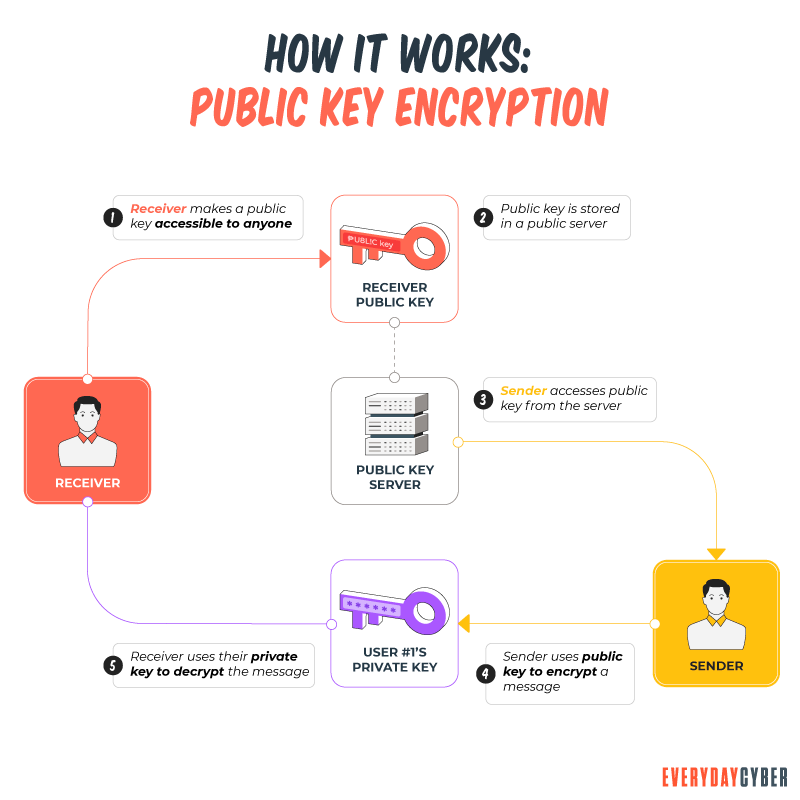
Asymmetric encryption uses two keys: a public key to encrypt data and a private key to decrypt data.
Advanced Encryption Standard (AES) is the most secure encryption algorithm used by the United States and the rest of the world. It uses the Rijndael block cipher with a block size of 128 bits. The key sizes are 128, 192, and
So now what is encryption? When you encrypt something, you’re converting plaintext (unencrypted data) into ciphertext (encrypted data) by applying an algorithmic function to it. The key is the algorithm you’re employing. The value of the encryption key must be kept secret in asymmetric encryption, with the exception of public keys. The only way to decrypt that bit of ciphertext is to use the private key associated with it.
How does 256 bit encryption work
256 bit encryption uses the Advanced Encryption Standard (AES) algorithm. It’s a method of hiding plaintext data using a
AES algorithm rounds
Divide data into blocks
If your message is “call the police”, the blocks of letters represent the initial key. The block might look like this: (This example and the subsequent examples are made up.)
c t i
a h p c
l e o e
l l
After the data is separated into blocks, it undergoes the following changes during AES encryption:
Expand the key
For each cycle of the encryption process, key expansion involves taking the initial key and using it to generate a series of additional keys. Rijndael’s key schedule is used to create these new bit round keys. The initial key is “the sky is blue”.
t b
h s l
e k i u
y s e
The new keys might look something like this:
12 2k w8 yw
ah pk x9 gf
fb 7q sc 3d
lm jn z6 vm
Add the round key
The initial key is added to the block of the message:
c t i
a h p c
l e o e
l l
t b
h s l
e k i u
y s e
For extra protection, you can include an extra encryption algorithm such as XOR cipher. Let’s say we come up with this result:
jq 1k pa m3
hb vw 0c ro
f3 sa rb yr
X8 7d b2 pz
Substitute the bytes
Each byte is replaced according to a predetermined table. For example, the letters can be coded by changing each with the letter that precedes it in the alphabet. So that “police” would be “onkhbd”.
This system is a little more difficult to understand and does not necessarily follow any logic. Instead, the algorithm is based on a table that specifies, for example, that h3 becomes jb, s8 becomes 9f, dj becomes 62, and so on. Let’s imagine the preset table provides us the following results after this step:
kf 5g lq xc
2n rg bz j1
mn we 7c pu
yf 6a db 4x
Shift the rows
The first row doesn’t move. The second row moves one space to the left. The third row moves two spaces to the left. The fourth row moves three spaces to the left. The resulting block would be:
kf 5g lq xc
rg bz j1 2n
7c pu mn we
4x yf 6a db
Mix the columns
Let’s assume a mathematical computation has been applied to each column. The columns might look like this:
q4 v9 rh bp
ku wf 7u de
lg ox 1y pi
rx oh 6c jv
Add a round key again
This process involves adding the results of the mixed columns and the first round key. The columns would now look like this:
q4 v9 rh bp
ku wf 7u de
lg ox 1y pi
rx oh 6c jv
jq 1k pa m3
hb vw 0c ro
f3 sa rb yr
x8 7d b2 pz
After this operation, the new results might be:
c9 ap m2 kx
8q iw u4 yh
vt el d6 ss
1f gq bz o3
The process doesn’t end here.
If you’ve come this far, thank you for bearing with us. We’ve done our best to simplify the steps, but we just wanted to show the computational complexity of the operation.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Why are the steps and rounds necessary?
You may wonder why there are so many steps and why the whole operation needs to undergo 14 rounds. Going through all the steps and rounds alter data. Shortcut attacks were discovered for up to six rounds of the AES procedure when it was being developed. This is why extra rounds were added to beef up encryption
Each step has a crucial role. Expanding keys and adding round keys prevents the use of just one key throughout all the rounds. Substituting bytes alters data in a non-linear way to create confusion to the information. Shifting rows alters data horizontally, while mixing columns alters data vertically. After each round, a new round key derived from the previous key adds more confusion to the data.
Common uses of 256 bit encryption
Being the industry standard,
- Generating symmetric session keys in order to establish a secure SSL/TLS connection
- Encrypting data in transit between a browser and server
- Encrypting data in an email when an email signing certificate is used
- Encrypting data in third-party cloud systems such as Google Drive, Amazon Web Services, and others.
Not all types of industries use
- Financial institutions, such as banks, credit card companies, and money transfer and remittance centers
- Governments and their agencies
- The military
- Large enterprises with e-commerce operations involving online payments
AES security threats to 256 bit encryption
When used with AES, 256 bit encryption is the most secure method for protecting sensitive data.
Cryptographers are continuously looking for flaws in AES, trying new ways to exploit the technology to test its strength. If it isn’t rigorously examined by academics, cyber criminals may get ahead of them.
Only theoretical cracks and side channel assaults have been discovered so far by academics. Here are some of them:
Stolen key
If a hacker can access a user’s key, AES-256 can be cracked. This is why it’s still important to implement firewalls, virus detection, effective password management, and other
Related key attack
This method involves watching how a cipher works under various keys. Researchers determined that related key attacks aren’t particularly dangerous. They only work against protocols that aren’t adequately implemented.
Known key attack
This attack uses a key that is already known in order to find out the fundamental structure of the cipher. Researchers discovered this attack in an eight-round version of AES-128. They say it isn’t too much to worry about for everyday users of AES-128.
Side channel attack
Side channel attack happens in systems with leaking information. The attacker monitors the sound, time, electromagnetic field, and the amount of energy consumed. Here, the attacker gets information from the algorithm and uses it to break it down.
Shor’s algorithm
Shor’s algorithm can break some public key cryptography methods, such as:
- The RSA system
- The Finite Field Diffie-Hellman key exchange
- The Elliptic Curve Diffie-Hellman key exchange
Grover’s algorithm
Grover’s algorithm can reduce the brute force attack time. For AES-256, Grover’s algorithm can shorten the time 2^128. This is still considered very secure.
Shor’s and Grover’s algorithms use quantum computing technology.
How safe is 256 bit encryption?
One of the most secure technologies of our time is
The encryption strength of an SSL/TLS protocol depends on the capabilities of the browser and server. Configuration is also an important factor. If a hacker is able to crack a
So how safe is
Our final thoughts. There’s no doubt
Should we be afraid of quantum computing? Google’s recent vacuum tube computing breakthrough may have entered the era of quantum computers, according to Mark Zhandry, senior scientist at NTTResearch. However, such computers do not have the scale or accuracy to pose a threat to current encryption methods, Zhandry adds.
Other experts say that doesn’t mean we can relax. But at least for now, we are safe with
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is Hacking?
Hacking is an old game in the cyberworld with ever changing players and techniques. It may be done with good intentions or malicious motives. It is growing rapidly because of the proliferation of devices.
What is Spam?
Spam - spam emails, texts and sms messages (i.e. junk email), are unsolicited messages sent indiscriminately in bulk. Spam is a gigantic waste of time and resources.
What is Smishing?
Smishing is a texting scam. Texts appear to come from reputable companies inducing you to reveal personal information, such as passwords or credit card numbers.
What is a WPA2 Password
Your Wi-Fi password is the network security pass you use to connect to your home network. This password is important because it protects your system from intruders.
What is a Drive By Download?
A "drive by download" is a cyber attack where visiting a website or hovering over an Ad causes malware to infect your computer or device.
What is a certificate authority CA and what do they do?
Certificate authorities are the guardians of digital identity. They come in both public and private capacities. Certificates issued by them are trusted because information are validated from the requester’s own records and/or from third party sources.



